An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device. Which of the following best describes the user’s activity?
A. Penetration testing
B. Phishing campaign
C. External audit
D. Insider threat
Explanation:
An insider threat is a security risk that originates from within the targeted organization. This can be a current or former employee, contractor, or business partner who has inside information concerning the organization's security practices, data, and computer systems. The scenario describes a user (an insider) who:
Logged in remotely after hours (using legitimate access credentials but at an unusual time).
Copied large amounts of data to a personal device (an unauthorized action that indicates data exfiltration).
This behavior is a classic indicator of malicious insider activity, whether it's for intellectual property theft, espionage, or other malicious purposes.
Why not A?
Penetration testing: This is an authorized, simulated cyberattack conducted by security professionals to evaluate the security of a system. It is done with explicit permission and knowledge of the organization, not covertly by a regular user.
Why not B?
Phishing campaign: This is a broad social engineering attack conducted by external threat actors to trick users into revealing sensitive information. It is not an activity performed by an internal user using their own credentials.
Why not C?
External audit: This is a formal review conducted by an independent third party to assess compliance, financial records, or security controls. It is a legitimate, authorized activity that would not involve copying data to a personal device without oversight.
Reference:
Domain 1.2: "Compare and contrast common threat actors and motivations." The SY0-701 objectives specifically categorize insider threats as a major type of threat actor. The description of unauthorized data access and exfiltration by a legitimate user is a key indicator of this threat.
Which of the following is the most common data loss path for an air-gapped network?
A. Bastion host
B. Unsecured Bluetooth
C. Unpatched OS
D. Removable devices
Explanation:
An air-gapped network is physically isolated from unsecured networks, such as the public internet or other local networks. This makes common network-based attack vectors (like an unpatched OS exploited over the internet) irrelevant. The primary data loss path for such a secured environment is through physical media.
Removable devices (e.g., USB drives, external hard drives) are the most common threat because they provide a simple, direct method for:
Data Exfiltration:
A malicious insider or an attacker who gains physical access can copy sensitive data onto a device and walk it out.
Data Introduction:
The same device can be used to introduce malware into the air-gapped system (e.g., via the Stuxnet worm, which famously used USB drives to propagate).
Why not A?
A bastion host is a specially hardened computer designed to withstand attacks. It is typically exposed to the public internet and acts as a gateway to a more secure internal network. An air-gapped network, by definition, has no such gateway to the internet, making a bastion host an irrelevant data loss path.
Why not B?
Unsecured Bluetooth is a wireless attack vector. A properly implemented air-gapped network will have all wireless adapters (Wi-Fi, Bluetooth, etc.) physically disabled or removed to enforce the "air gap," making this an unlikely path.
Why not C?
An unpatched operating system (OS) is a major vulnerability, but it is typically exploited over a network connection. Since the air-gapped network has no connection to external networks, the risk of a remote exploit is virtually eliminated. The threat from an unpatched OS in an air-gapped system would be primarily from malware introduced via a physical vector, like a removable device.
Reference:
Domain 2.1: "Explain the importance of security concepts in an enterprise environment." The concept of air-gapping falls under network segmentation and isolation. The associated risks highlight the need for physical security controls (e.g., disabling USB ports) to mitigate the primary threat of removable media.
Which of the following is an algorithm performed to verify that data has not been modified?
A. Hash
B. Code check
C. Encryption
D. Checksum
Explanation:
A cryptographic hash function is an algorithm specifically designed to verify the integrity of data. It takes an input (or 'message') and returns a fixed-size string of bytes, typically a digest that is unique to the unique input.
The process for verifying integrity is:
A sender calculates the hash of the original data.
The data and its hash are sent to the recipient.
The recipient independently calculates the hash of the received data.
The recipient compares their calculated hash with the hash that was sent.
If the two hashes match exactly, it proves the data was not modified in transit. Even the smallest change to the original data will produce a completely different hash value.
This property is fundamental to ensuring data has not been tampered with and is a core function of integrity verification.
Why the other options are incorrect:
B. Code check:
This is not a standard cryptographic term. It could refer to error-correcting codes in programming or data transmission, but it is not the precise algorithm used for cryptographic verification of integrity.
C. Encryption:
Encryption is an algorithm designed to provide confidentiality by transforming data into ciphertext to hide its content. While some encryption modes can also provide integrity, its primary purpose is not verification. It is possible to modify encrypted data in a way that is not detectable without an additional integrity mechanism. Hashing is the primary tool for pure verification.
D. Checksum:
A checksum is a value used to verify the integrity of a file or a data transfer. The key difference is that a checksum is designed to detect accidental errors (like those from network noise or disk faults), but it is not cryptographically secure. A malicious actor can easily modify the data and calculate a new valid checksum to match the altered data. A cryptographic hash function is designed to be computationally infeasible to reverse or to find two different inputs that produce the same output, making it suitable for detecting intentional, malicious modification.
Exam Objective Reference:
This question relates to Domain 2.0: Architecture and Design, specifically the concepts of cryptography and the core security service of integrity. It tests the understanding of the different purposes of hashing (integrity) versus encryption (confidentiality).
Which of the following roles, according to the shared responsibility model, is responsible for securing the company’s database in an IaaS model for a cloud environment?
A. Client
B. Third-party vendor
C. Cloud provider
D. DBA
Explanation:
In the cloud shared responsibility model, the division of security duties depends on the service model (IaaS, PaaS, SaaS). The question specifies an IaaS (Infrastructure as a Service) model.
IaaS Model:
The cloud provider is responsible for the security of the cloud. This includes the physical infrastructure, network connectivity, and the hypervisor that virtualizes the compute, storage, and networking resources.
The client (the company using the service) is responsible for security in the cloud. This includes securing:
The guest operating systems on their virtual machines
The applications installed on those VMs
The data, including the company's database and its configuration
Identity and Access Management (IAM) for their users
Since the database is an application installed and managed by the company on the virtual infrastructure provided by the cloud provider, securing it is the client's responsibility.
Why the other options are incorrect:
B. Third-party vendor (Incorrect):
A third-party vendor might provide the database software (e.g., Oracle, MongoDB), but the responsibility for securing the installation, configuration, patching, and access to that database instance falls on the client who owns and operates it in their IaaS environment.
C. Cloud provider (Incorrect):
The cloud provider's responsibility in IaaS ends at the virtualization layer. They ensure the underlying infrastructure is available and secure, but they have no access to or responsibility for the operating systems, applications, or data you deploy on that infrastructure.
D. DBA (Incorrect):
A Database Administrator (DBA) is a role within the client's organization. While the DBA would be the individual tasked by the client with implementing the technical controls to secure the database (e.g., configuring authentication, encryption, auditing), the ultimate responsibility belongs to the client organization itself, as defined in the contract with the cloud provider.
Reference:
This question falls under Domain 2.0: Threats, Vulnerabilities, and Mitigations and Domain 3.0: Security Architecture, specifically testing knowledge of cloud service models (IaaS, PaaS, SaaS) and the shared responsibility matrix. Understanding what security tasks are the client's duty in each model is a critical objective for the SY0-701 exam.
A data administrator is configuring authentication for a SaaS application and would like to reduce the number of credentials employees need to maintain. The company prefers to use domain credentials to access new SaaS applications. Which of the following methods would allow this functionality?
A. SSO
B. LEAP
C. MFA
D. PEAP
Explanation: SSO stands for single sign-on, which is a method of authentication that allows users to access multiple applications or services with one set of credentials. SSO reduces the number of credentials employees need to maintain and simplifies the login process. SSO can also improve security by reducing the risk of password reuse, phishing, and credential theft. SSO can be implemented using various protocols, such as SAML, OAuth, OpenID Connect, and Kerberos, that enable the exchange of authentication information between different domains or systems. SSO is commonly used for accessing SaaS applications, such as Office 365, Google Workspace, Salesforce, and others, using domain credentials123.
B. LEAP stands for Lightweight Extensible Authentication Protocol, which is a Cisco proprietary protocol that provides authentication for wireless networks. LEAP is not related to SaaS applications or domain credentials4.
C. MFA stands for multi-factor authentication, which is a method of authentication that requires users to provide two or more pieces of evidence to prove their identity. MFA can enhance security by adding an extra layer of protection beyond passwords, such as tokens, biometrics, or codes. MFA is not related to SaaS applications or domain credentials, but it can be used in conjunction with SSO.
D. PEAP stands for Protected Extensible Authentication Protocol, which is a protocol that provides secure authentication for wireless networks. PEAP uses TLS to create an encrypted tunnel between the client and the server, and then uses another authentication method, such as MS-CHAPv2 or EAP-GTC, to verify the user’s identity. PEAP is not related to SaaS applications or domain credentials.
References = 1: Security+ (SY0-701) Certification Study Guide | CompTIA IT Certifications 2: What is Single Sign-On (SSO)? - Definition from WhatIs.com 3: Single sign-on - Wikipedia 4: Lightweight Extensible Authentication Protocol - Wikipedia : What is Multi-Factor Authentication (MFA)? - Definition from WhatIs.com : Protected Extensible Authentication Protocol - Wikipedia
A recent penetration test identified that an attacker could flood the MAC address table of network switches. Which of the following would best mitigate this type of attack?
A. Load balancer
B. Port security
C. IPS
D. NGFW
Explanation:
Why B is Correct:
Port security is a feature on network switches that directly mitigates MAC address table flooding attacks. In this type of attack, an attacker sends a large number of frames with spoofed source MAC addresses to overwhelm the switch's MAC address table, causing it to enter a "fail-open" state where it broadcasts traffic to all ports (like a hub), allowing the attacker to eavesdrop. Port security can be configured to:
Limit the number of MAC addresses allowed on a specific port.
Dynamically learn and sticky-MAC addresses to prevent spoofing.
Take action (e.g., shut down the port) if unauthorized MAC addresses are detected.
This prevents the switch's MAC address table from being flooded.
Why A is Incorrect:
A load balancer distributes network traffic across multiple servers to optimize resource use and ensure availability. It operates at higher layers (e.g., Layer 4 or 7) and is not designed to protect Layer 2 switch functionality like MAC address tables.
Why C is Incorrect:
An Intrusion Prevention System (IPS) monitors network traffic for malicious activity and can block attacks. While some IPS systems might have signatures for MAC flooding, they are not as effective or direct as port security, which is implemented on the switch itself where the attack occurs. Port security is a preventive control, while IPS is more reactive.
Why D is Incorrect:
A Next-Generation Firewall (NGFW) provides advanced network security by inspecting traffic at multiple layers and applying policies. However, it is typically deployed at the network perimeter or between segments and does not protect internal switches from Layer 2 attacks like MAC flooding.
Reference:
This question falls under Domain 2.0: Architecture and Design, specifically covering network security controls. Port security is a fundamental switch configuration best practice to prevent Layer 2 attacks, including MAC address table flooding, and is a key objective for the SY0-701 exam.
A Chief Information Security Officer (CISO) wants to explicitly raise awareness about the increase of ransomware-as-a-service in a report to the management team. Which of the following best describes the threat actor in the CISO's report?
A. Insider threat
B. Hacktivist
C. Nation-state
D. Organized crime
Explanation:
Ransomware-as-a-Service (RaaS) is a cybercrime business model where developers create ransomware and lease it to affiliates, who then carry out the attacks. The profits are shared between the developers and the affiliates.
D. Organized crime is correct.
This business model is a hallmark of cyber-organized crime. These groups operate like sophisticated businesses, with developers, distributors, and customer support, all focused on financial profit. Their structured, profit-driven approach aligns perfectly with the characteristics of organized crime.
A. Insider threat is incorrect.
An insider threat is a current or former employee, contractor, or business partner who has inside access and misuses it to harm the organization. While an insider might use ransomware, the RaaS model itself is operated and promoted by external criminal organizations, not typically by insiders.
B. Hacktivist is incorrect.
Hacktivists are motivated by ideology or social/political causes, not financial gain. Their goal is to raise awareness or disrupt services for their cause. They would not typically develop and sell a service for profit; their actions are meant to send a message.
C. Nation-state is incorrect.
Nation-state actors are sponsored by governments and are primarily motivated by espionage, intellectual property theft, or sabotage to achieve strategic goals. While they may use ransomware as a tool for disruption or to create plausible deniability, their primary motive is not financial profit. The RaaS model is fundamentally a for-profit criminal enterprise, not a nation-state intelligence operation.
Reference:
CompTIA Security+ SY0-701 Objective 1.5: "Explain different threat actor models and attributes." This objective requires understanding the motivations and characteristics of different threat actors. Organized crime is explicitly defined by its financial motivation and increasingly sophisticated, business-like operations, such as Ransomware-as-a-Service (RaaS).
While considering the organization's cloud-adoption strategy, the Chief Information Security Officer sets a goal to outsource patching of firmware, operating systems, and applications to the chosen cloud vendor. Which of the following best meets this goal?
A. Community cloud
B. PaaS
C. Containerization
D. Private cloud
E. SaaS
F. laaS
Explanation: Software as a Service (SaaS) is the cloud model that best meets the goal of outsourcing the management, including patching, of firmware, operating systems, and applications to the cloud vendor. In a SaaS environment, the cloud provider is responsible for maintaining and updating the entire software stack, allowing the organization to focus on using the software rather than managing its infrastructure.
A security administrator recently reset local passwords and the following values were recorded in the system:
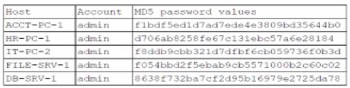
Which of the following in the security administrator most likely protecting against?
A. Account sharing
B. Weak password complexity
C. Pass-the-hash attacks
D. Password compromise
Explanation:
The correct answer is C. Pass-the-hash attacks.
A pass-the-hash (PtH) attack is a technique where an attacker steals a hashed user credential (the NTLM or LAN Manager hash in Windows environments) and then uses it to authenticate to a remote system or service without needing to know the plaintext password. The attack exploits the authentication protocol itself, not the strength of the password.
The image shows that after the password was reset, the system recorded a new hash for the user's password, but the LMHistory and NTHistory values were also updated.
These history values store the hashes of previous passwords. By resetting the local passwords and ensuring the system records and manages these history values, the administrator is ensuring that the old password hashes are no longer valid for authentication.
This action directly invalidates any hashes an attacker may have previously captured. Even if an attacker had stolen the old hash before the reset, they can no longer use it in a pass-the-hash attack because the system has recorded that it is an old, invalid credential.
Why the other options are incorrect:
A. Account sharing:
Account sharing is a policy violation where multiple people use the same login credentials. Resetting a password and recording its hash does nothing to prevent multiple individuals from learning and using the new password. Preventing account sharing requires policy enforcement, user training, and technical controls like multi-factor authentication (MFA), not password resets with hash history.
B. Weak password complexity:
Password complexity rules (e.g., requiring uppercase, lowercase, numbers, and symbols) are enforced by password policy settings at the time a new password is created. The act of resetting a password and recording the hash is an action taken after the password has already been created. It does not affect the complexity of the new or old password.
D. Password compromise:
While resetting a password is a standard response to a suspected or confirmed password compromise, the key detail in the question is the recording of the values in the history. A simple password reset would just change the current hash. The specific action of managing the password history hashes is a targeted measure against PtH attacks, not just a general response to a compromised plaintext password.
Reference:
This defense is specifically outlined in resources like the MITRE ATT&CK framework under technique T1550.002 - Use
Alternate Authentication Material:
Pass the Hash. Mitigation strategies include:
Password Reset:
Regularly resetting passwords, especially for privileged accounts.
Password History:
Enforcing password history policies to prevent the immediate reuse of old passwords and, crucially, to invalidate their associated hashes.
A systems administrator receives the following alert from a file integrity monitoring tool:
The hash of the cmd.exe file has changed.
The systems administrator checks the OS logs and notices that no patches were applied in the last two months. Which of the following most likely occurred?
A. The end user changed the file permissions.
B. A cryptographic collision was detected.
C. A snapshot of the file system was taken.
D. A rootkit was deployed.
Explanation:
A File Integrity Monitoring (FIM) tool alerts when a system file has been altered, which is a significant event, especially for a critical system file like cmd.exe.
D. A rootkit was deployed is correct.
A rootkit is a type of malware designed to gain privileged access to a system while actively hiding its presence. A common technique for maintaining persistence and avoiding detection is to replace or modify core system files (like cmd.exe) with malicious versions. The fact that no patches were applied rules out a legitimate change from an OS update, making unauthorized modification by a rootkit the most likely cause of the altered hash.
A. The end user changed the file permissions is incorrect.
Changing file permissions (e.g., read, write, execute) does not alter the actual contents of the file. The FIM tool is alerting that the hash has changed, which means the binary data of the file itself is different. Permissions are metadata, not file content.
B. A cryptographic collision was detected is incorrect.
A cryptographic collision occurs when two different inputs produce the same hash output. While theoretically possible with older algorithms like MD5, it is computationally infeasible with modern hashing algorithms (like SHA-256) used by FIM tools. This is an extremely unlikely event and would not be the assumed cause without evidence.
C. A snapshot of the file system was taken is incorrect.
Taking a snapshot (a point-in-time copy of a filesystem) is a read-only operation. It does not modify the original file or change its hash.
Reference:
CompTIA Security+ SY0-701 Objective 1.4: "Given a scenario, analyze indicators of malicious activity." The alteration of a core OS file is a primary indicator of compromise (IOC), often associated with malware like rootkits that attempt to hide their activity by subverting the operating system.
| Page 23 out of 72 Pages |
