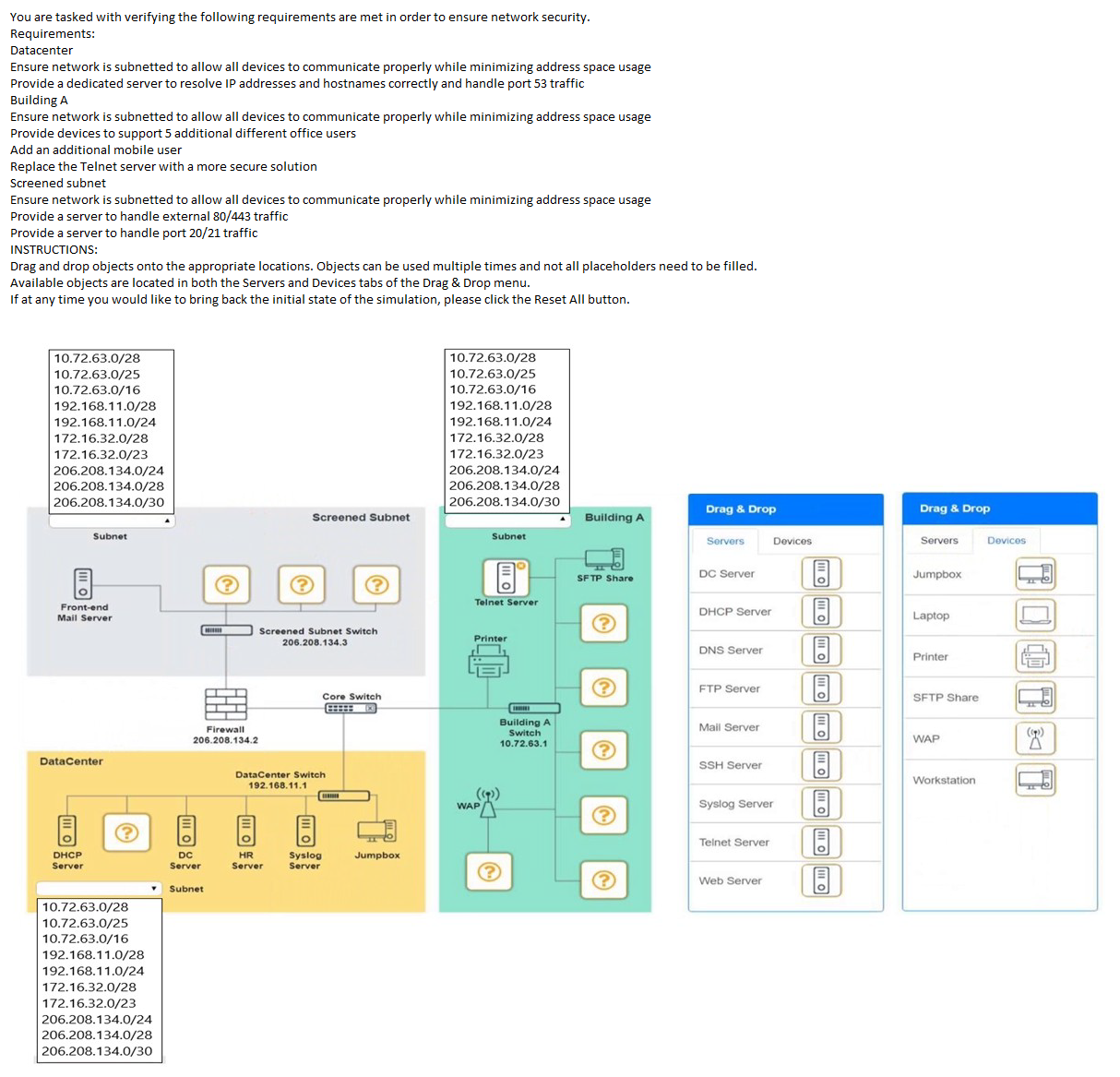
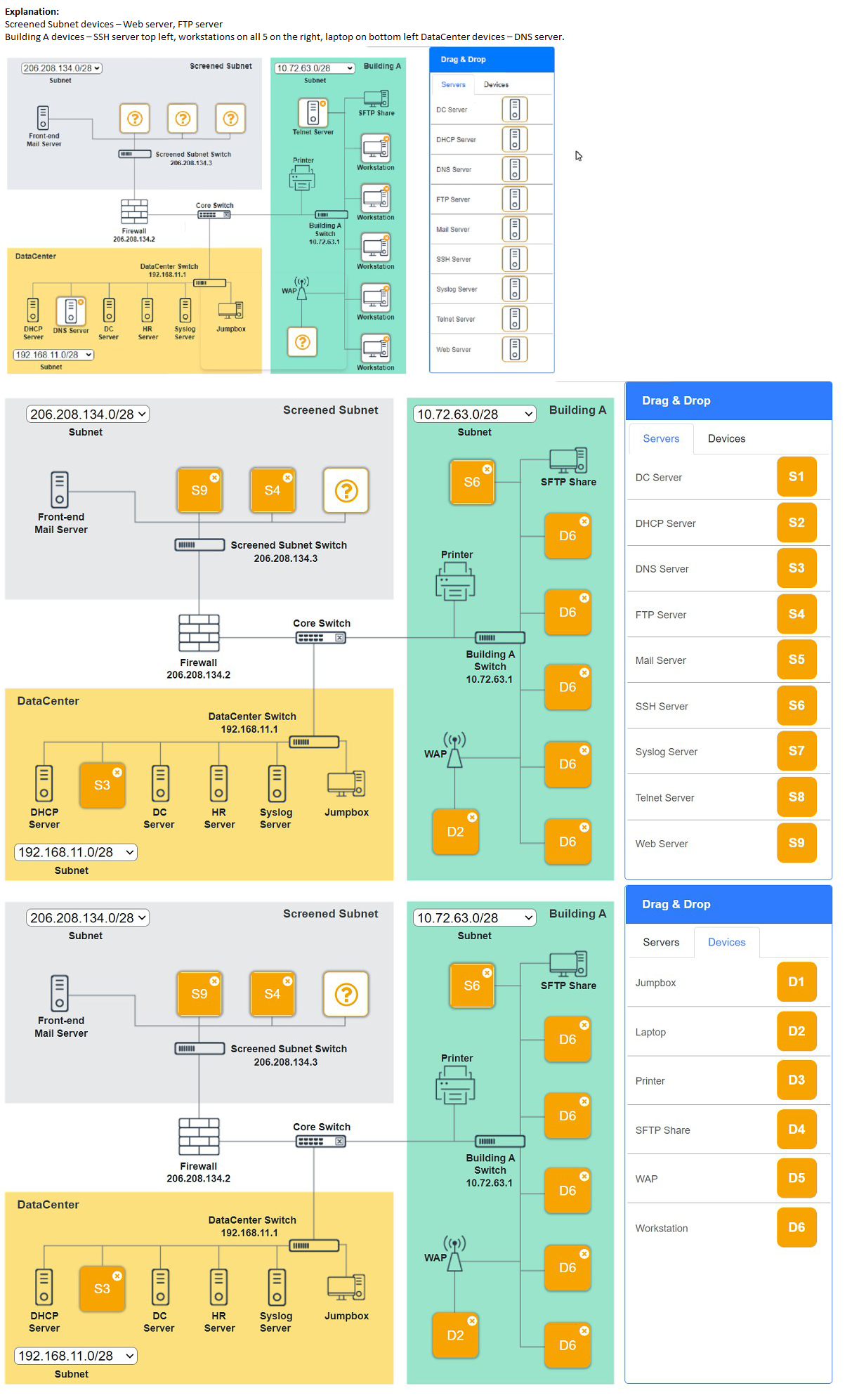
An organization requires the ability to send encrypted email messages to a partner from an email server that is hosted on premises. The organization prefers to use the standard default ports when creating firewall rules. Which of the following ports should be open to satisfy the requirements?
A. 110
B. 143
C. 587
D. 636
Explanation:
The organization needs to send encrypted email messages from an on-premises email server to a partner, using standard default ports for firewall rules. This scenario involves email encryption, typically achieved using protocols like STARTTLS or TLS/SSL over SMTP (Simple Mail Transfer Protocol). Let’s evaluate the options:
C. 587:
Purpose: Port 587 is the standard default port for email submission using SMTP with encryption (e.g., STARTTLS or TLS). It is designed for clients (e.g., email servers or user agents) to submit messages to a mail server securely, often with authentication.
Why it fits: For an on-premises email server to send encrypted messages to a partner’s server, port 587 should be open on the firewall to allow secure SMTP submission. This port supports encryption via STARTTLS, ensuring the email content is protected during transmission. The organization’s preference for default ports aligns with 587 as the modern standard for secure email submission, as defined by RFC 8314, which recommends using 587 with opportunistic TLS.
Context: The on-premises server would use 587 to connect to the partner’s mail server (or its own submission service) for outbound encrypted email.
Why Not the Other Options?
A. 110:
Port 110 is the default port for POP3 (Post Office Protocol version 3), used by email clients to retrieve messages from a server. While POP3 can support encryption (e.g., POP3S on port 995), it is not designed for sending emails or server-to-server communication, making it irrelevant for this requirement.
B. 143:
Port 143 is the default port for IMAP (Internet Message Access Protocol), used for retrieving and managing emails on a server. Like POP3, IMAP is for client access, not for sending emails between servers, and it doesn’t meet the need for encrypted email transmission.
D. 636:
Port 636 is the default port for LDAPS (LDAP over SSL/TLS), used for secure directory service queries (e.g., Active Directory authentication). It is not related to email transmission or SMTP, so it does not satisfy the requirement for sending encrypted emails.
Why Port 587?
Port 587 is specifically designated for secure email submission, allowing the on-premises email server to authenticate and encrypt messages using STARTTLS or TLS before sending them to the partner’s server. This is distinct from port 25 (unencrypted SMTP), which is traditionally used for mail server relay but is less secure and often blocked by firewalls for outbound traffic. The use of 587 ensures compliance with modern email security standards while adhering to the organization’s preference for default ports.
Additional Considerations:
The partner’s email server must also support port 587 and encryption for the connection to succeed.
If the organization uses a specific email client or server (e.g., Microsoft Exchange, Postfix), it should be configured to use 587 with TLS.
Firewall rules should allow outbound traffic on 587 to the partner’s mail server IP or domain.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 1.5 – "Compare and contrast common network protocols and their functions." This includes understanding email-related ports like 587.
RFC 8314 (Cleartext Considered Obsolete):
Recommends using port 587 with opportunistic TLS for secure email submission.
IANA Service Name and Transport Protocol Port Number Registry:
Lists 587 as the official port for secure SMTP submission.
A network administrator installed anew VLAN to the network after a company added an additional floor to the office. Users are unable to obtain an IP address on the new VLAN, but ports on existing VLANs are working properly. Which of the following configurations should the administrator update?
A. Scope size
B. Address reservations
C. Lease time
D. IP helper
Explanation:
The network administrator has added a new VLAN to the network following the addition of a new floor to the office. Users on the new VLAN cannot obtain an IP address, while ports on existing VLANs are functioning correctly. This suggests a configuration issue specific to the new VLAN’s ability to communicate with the DHCP server, which is not a problem for the existing VLANs. The most likely solution is to update the IP helper configuration.
D. IP helper:
Purpose: An IP helper (or DHCP relay agent) is configured on a router or Layer 3 switch to forward DHCP broadcast requests from clients on a VLAN to a DHCP server located on a different subnet or VLAN. By default, DHCP requests are broadcast messages that do not cross VLAN boundaries unless relayed.
Why it fits: Since the new VLAN is isolated from the existing VLANs, and the DHCP server is likely on an existing VLAN (given that other VLANs work), the new VLAN’s clients cannot reach the DHCP server without an IP helper address. Adding or configuring an IP helper address on the router or switch interface for the new VLAN (pointing to the DHCP server’s IP) will allow clients to obtain IP addresses.
Example: If the DHCP server is at 192.168.1.10 and the new VLAN is 192.168.2.0/24, the administrator would configure ip helper-address 192.168.1.10 on the VLAN 2 interface.
Why Not the Other Options?
A. Scope size: The DHCP scope defines the range of IP addresses available for a subnet. While the scope size might need adjustment if the new VLAN has too few addresses for the number of users, the fact that users cannot obtain any IP address suggests the DHCP server isn’t being reached, not that the scope is exhausted. This is a connectivity issue, not a scope size issue.
B. Address reservations: DHCP address reservations assign specific IP addresses to devices based on their MAC addresses. This is unrelated to the inability to obtain any IP address and would only apply if specific devices need static assignments, which isn’t indicated here.
C. Lease time: The lease time determines how long a DHCP client can use an IP address before renewing it. Changing the lease time wouldn’t address the fundamental issue of clients not receiving an IP address in the first place due to lack of DHCP communication.
Why IP Helper?
In a multi-VLAN environment, each VLAN operates as a separate broadcast domain. The existing VLANs likely have IP helper configurations or are on the same subnet as the DHCP server, allowing them to function. The new VLAN, however, lacks this configuration, preventing DHCP broadcasts from reaching the server. Adding an IP helper address ensures the DHCP requests are relayed, resolving the issue. The administrator should verify the DHCP server’s location and ensure the helper address is correctly set.
Troubleshooting Steps:
Confirm the DHCP server’s IP address and subnet.
Check the router or Layer 3 switch interface for the new VLAN (e.g., VLAN 10) and add the IP helper command.
Test by releasing and renewing IP addresses on a client (e.g., ipconfig /release and ipconfig /renew on Windows).
Verify connectivity with a ping to the gateway.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 2.3 – "Given a scenario, configure and deploy common network devices." This includes configuring DHCP relay (IP helper) for VLANs.
RFC 2131 (Dynamic Host Configuration Protocol):
Describes DHCP operation and the need for relay agents in multi-subnet environments.
Cisco Networking Documentation:
Details the use of ip helper-address to enable DHCP across VLANs.
An organization has a security requirement that all network connections can be traced back to a user. A network administrator needs to identify a solution to implement on the wireless network. Which of the following is the best solution?
A. Implementing enterprise authentication
B. Requiring the use of PSKs
C. Configuring a captive portal for users
D. Enforcing wired equivalent protection
Explanation:
The organization requires that all network connections on the wireless network can be traced back to a user, meaning each connection must be uniquely associated with an individual for accountability and auditing purposes. The best solution to meet this requirement is implementing enterprise authentication.
A. Implementing enterprise authentication:
How it works: Enterprise authentication, typically using WPA2-Enterprise or WPA3-Enterprise, relies on a RADIUS (Remote Authentication Dial-In User Service) server to authenticate users with unique credentials (e.g., username and password or certificates). Each user’s connection is logged with their identity, allowing traceability.
Why it fits: This method ensures that every wireless connection is tied to a specific user, enabling the organization to trace network activity back to an individual via RADIUS logs. For example, if a security incident occurs, the administrator can identify the user associated with the connection, meeting the traceability requirement.
Additional Benefits: It also supports strong security through individual authentication and can integrate with existing directory services (e.g., Active Directory).
Why Not the Other Options?
B. Requiring the use of PSKs (Pre-Shared Keys):
A PSK, used in WPA2-Personal or WPA3-Personal, involves all users sharing a single key. This makes it impossible to trace connections to individual users, as all activity is associated with the shared key, not a unique identity. This does not meet the requirement.
C. Configuring a captive portal for users:
A captive portal requires users to log in (e.g., with credentials) before accessing the network, which can provide user identification. However, it is primarily an authentication mechanism for public Wi-Fi and does not inherently log or trace all network connections continuously. It also requires user interaction each time, which may not be practical for a corporate wireless network, and logging depends on additional configuration.
D. Enforcing wired equivalent protection:
WEP (Wired Equivalent Privacy) is an outdated and insecure wireless encryption standard. It does not provide user-based authentication or traceability, as it relies on a shared key similar to PSKs. WEP is no longer recommended due to its vulnerabilities and does not meet the requirement.
Why Enterprise Authentication?
Enterprise authentication with a RADIUS server creates a unique session for each user, logging their connection details (e.g., username, timestamp, IP address) in the RADIUS server logs. This allows the network administrator to audit and trace any network activity back to the responsible user, fulfilling the security requirement. For instance, in the event of a policy violation or breach, the logs can pinpoint the user’s device and actions, enhancing accountability
.
Implementation Steps:
Configure a RADIUS server (e.g., FreeRADIUS, Microsoft NPS) with user accounts or certificates.
Set up the wireless access points to use WPA2-Enterprise or WPA3-Enterprise with RADIUS authentication.
Distribute unique credentials to each user.
Enable logging on the RADIUS server to record connection details.
Test connectivity and verify log entries.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.3 – "Given a scenario, implement secure network configurations." This includes configuring enterprise authentication for user traceability.
RFC 2865 (Remote Authentication Dial-In User Service):
Defines RADIUS and its role in user authentication and logging.
Cisco Wireless Security Guides:
Recommend WPA2-Enterprise with RADIUS for user-based wireless authentication and auditing
A technician needs to identify a computer on the network that is reportedly downloading unauthorized content. Which of the following should the technician use?
A. Anomaly alerts
B. Port mirroring
C. Performance monitoring
D. Packet capture
Explanation:
A technician needs to identify a computer on the network that is downloading unauthorized content, requiring a method to inspect and analyze the specific network traffic associated with the activity. The best tool for this task is packet capture.
D. Packet capture:
How it works: Packet capture (e.g., using tools like Wireshark, tcpdump, or a network analyzer) records and analyzes the actual data packets traveling across the network. It allows the technician to inspect packet contents, including source/destination IP addresses, ports, protocols, and payload data, to identify the offending computer.
Why it fits: By capturing packets, the technician can trace the source IP address of the unauthorized downloads, match it to a device on the network, and analyze the content or destination (e.g., file-sharing sites or malicious servers). This provides concrete evidence to pinpoint the responsible computer.
Example: The technician could filter packets for specific ports (e.g., 80 for HTTP, 443 for HTTPS) or keywords related to unauthorized content.
Why Not the Other Options?
A. Anomaly alerts:
Anomaly alerts, typically generated by intrusion detection systems (IDS) or security information and event management (SIEM) tools, flag unusual network behavior (e.g., high traffic or unexpected patterns). While useful for initial detection, they don’t provide detailed packet-level data to identify the specific computer or confirm unauthorized content without further investigation.
B. Port mirroring:
Port mirroring (or SPAN - Switched Port Analyzer) copies traffic from one or more switch ports to a monitoring port for analysis. While it can be used as a setup for packet capture, it is a configuration step rather than a standalone solution. Without capturing and analyzing the mirrored traffic (e.g., with a packet analyzer), it doesn’t directly identify the computer.
C. Performance monitoring:
Performance monitoring tools (e.g., SNMP or network management software) track metrics like bandwidth usage, latency, or device health. They can indicate a device is using excessive resources but lack the granularity to identify unauthorized content or trace it to a specific computer without packet-level inspection.
Why Packet Capture?
Packet capture is the most effective method for this scenario because it provides detailed, real-time visibility into network traffic. The technician can set up a capture on a switch port, mirror port, or network tap, filter for suspicious traffic (e.g., large downloads or specific IPs), and correlate the source IP with the network’s DHCP or ARP records to identify the computer. This approach is direct and aligns with troubleshooting unauthorized activity.
Implementation Steps:
Identify a monitoring point (e.g., switch port or span port) near the suspected traffic.
Use a packet capture tool to record traffic.
Filter packets by protocol, port, or IP range to isolate unauthorized downloads.
Trace the source IP to a device using network documentation or DHCP logs.
Document findings for further action (e.g., blocking the device).
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.2 – "Given a scenario, troubleshoot common network connectivity issues." This includes using packet capture for network analysis.
RFC 791 (Internet Protocol):
Provides the foundation for packet structure and analysis.
Wireshark Documentation:
Details how packet capture can be used to identify network activity, including unauthorized downloads.
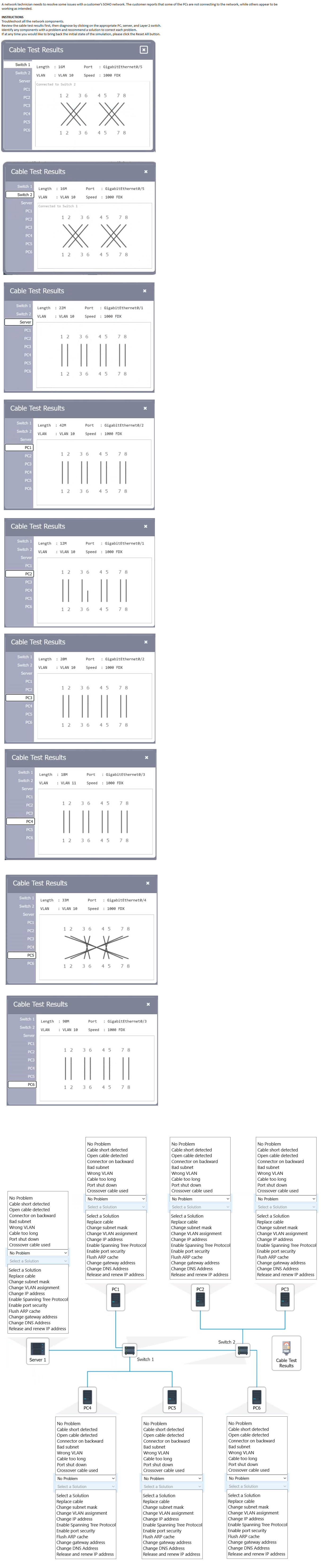
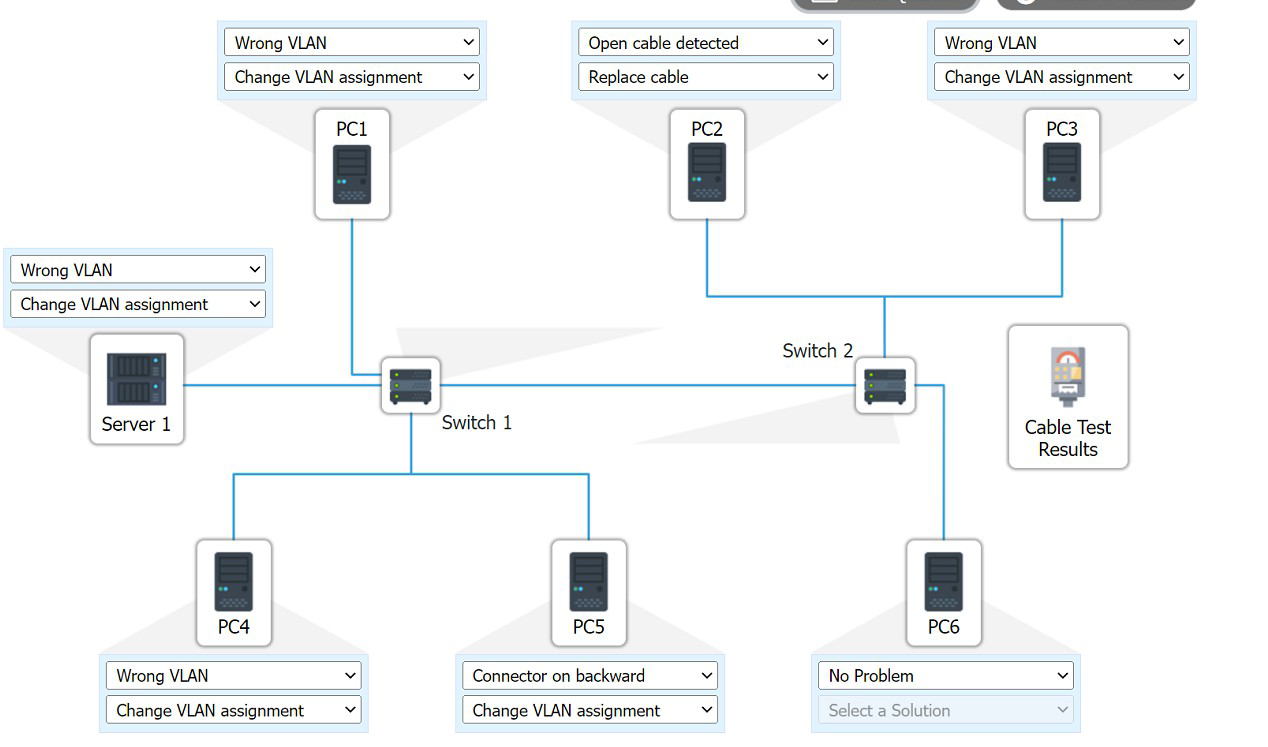
A network administrator needs to connect a department to a new network segment. They need to use a DHCP server located on another network. Which of the following can the administrator use to complete this task?
A. IP Helper
B. Reservation
C. Exclusion
D. Scope
Explanation:
The network administrator needs to connect a department to a new network segment and use a DHCP server located on another network. This requires a mechanism to allow DHCP requests from the new segment to reach the DHCP server across different network boundaries, which is best achieved using an IP Helper.
A. IP Helper:
How it works: An IP Helper (or DHCP relay agent) is configured on a router or Layer 3 switch to forward DHCP broadcast requests from clients on one network segment (e.g., the new department VLAN) to a DHCP server on a different network. By default, DHCP requests are broadcast messages that do not cross router boundaries unless relayed.
Why it fits: Since the DHCP server is on another network, the administrator must configure an IP Helper address on the router interface for the new network segment, pointing to the DHCP server’s IP address. This ensures clients in the new segment can obtain IP addresses dynamically. For example, if the DHCP server is at 192.168.1.10 and the new segment is 192.168.2.0/24, the command ip helper-address 192.168.1.10 would be added to the router’s VLAN 2 interface.
Context: This is a common solution in multi-segment or multi-VLAN networks where the DHCP server is centralized.
Why Not the Other Options?
B. Reservation:
A DHCP reservation assigns a specific IP address to a device based on its MAC address within a DHCP scope. This is useful for ensuring a device always gets the same IP but does not address the issue of reaching a DHCP server on another network.
C. Exclusion:
A DHCP exclusion reserves a range of IP addresses within a scope that the DHCP server will not assign to clients. This is a scope management feature and does not help clients on a new network segment communicate with a remote DHCP server.
D. Scope:
A DHCP scope defines the range of IP addresses a server can assign to clients within a specific subnet. While a new scope would need to be created for the new network segment, it must reside on the DHCP server. Without an IP Helper to relay requests to the server on another network, clients cannot access it.
Why IP Helper?
In a network with multiple segments or VLANs, the DHCP server is often centralized on one subnet (e.g., the main office network). The new department’s network segment, being separate, cannot broadcast to the DHCP server unless a relay agent (IP Helper) is configured. This solution ensures seamless IP address assignment without requiring a DHCP server on every segment.
Implementation Steps:
Identify the IP address of the DHCP server on the other network.
Configure the IP Helper address on the router or Layer 3 switch interface for the new network segment (e.g., ip helper-address
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 2.3 – "Given a scenario, configure and deploy common network devices." This includes configuring DHCP relay (IP Helper) for inter-network DHCP.
RFC 2131 (Dynamic Host Configuration Protocol):
Describes the need for DHCP relay agents in multi-subnet environments.
Cisco Networking Documentation:
Details the use of ip helper-address to enable DHCP across network segments.
A client with a 2.4GHz wireless network has stated that the entire office is experiencing intermittent issues with laptops after the WAP was moved. Which of the following is the most likely reason for these issues?
A. The network uses a non-overlapping channel.
B. The signal is reflecting too much.
C. The network has excessive noise.
D. A microwave is in the office.
Explanation:
The client with a 2.4GHz wireless network is experiencing intermittent issues with laptops across the entire office after the Wireless Access Point (WAP) was moved. This suggests a widespread interference problem affecting the wireless signal. The most likely reason is the network has excessive noise.
C. The network has excessive noise:
How it works: The 2.4GHz band is crowded with potential sources of interference, including other Wi-Fi networks, Bluetooth devices, cordless phones, microwave ovens, and other electronic equipment. Moving the WAP may have placed it closer to or within range of additional noise sources, causing intermittent connectivity issues across the office.
Why it fits: Intermittent issues affecting all laptops indicate a general environmental factor rather than a specific device or configuration problem. Excessive noise degrades the signal-to-noise ratio (SNR), leading to dropped connections or reduced performance, which aligns with the symptom of widespread intermittent issues after the WAP relocation.
Example: The WAP might now be near a crowded area with multiple overlapping Wi-Fi networks or electronic devices, increasing noise levels.
Why Not the Other Options?
A. The network uses a non-overlapping channel:
The 2.4GHz band has three non-overlapping channels (1, 6, and 11). Using a non-overlapping channel is a best practice to reduce interference, not a cause of issues. If the WAP was moved to a location where it still uses a non-overlapping channel but problems persist, the issue lies elsewhere (e.g., noise), not the channel itself.
B. The signal is reflecting too much:
Excessive signal reflection (multipath interference) can cause issues like packet loss or reduced throughput, but it typically affects specific areas rather than the entire office uniformly. Moving the WAP might alter reflection patterns, but intermittent issues across all laptops are more indicative of broad interference (noise) than localized reflection problems.
D. A microwave is in the office:
A microwave can interfere with the 2.4GHz band, especially when operating, causing intermittent disruptions. However, this would likely affect a localized area near the microwave rather than the entire office unless multiple microwaves or other devices are present throughout. The widespread nature of the issue after the WAP move points to a broader noise problem.
Why Excessive Noise?
The 2.4GHz band is highly susceptible to interference due to its limited spectrum and widespread use. Moving the WAP might have shifted it into a noisier environment (e.g., closer to other APs, electronic equipment, or physical obstructions), amplifying interference across the office. A site survey or spectrum analyzer could confirm high noise levels, and the administrator might mitigate this by adjusting the channel, reducing power, or relocating the WAP again.
Troubleshooting Steps:
Use a Wi-Fi analyzer to check for noise levels and overlapping networks.
Test different channels (1, 6, 11) to find the least noisy option.
Relocate the WAP to a less congested area if noise sources are identified.
Verify client signal strength and adjust AP power if needed.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.2 – "Given a scenario, troubleshoot common network connectivity issues." This includes identifying interference as a cause of wireless problems.
IEEE 802.11 Standards:
Detail the 2.4GHz band’s susceptibility to noise and interference.
Cisco Wireless Troubleshooting Guides:
Highlight excessive noise as a common cause of intermittent wireless issues.
| Page 15 out of 43 Pages |
