A network administrator is developing a method of device monitoring with the following
requirements:
- Allows for explicit, by user, privilege management
- Includes centralized logging of changes
- Offers widely accessible remote management
- Provides support of service accounts
A. SNMP
B. API
C. SIEM
D. SSO
Explanation:
The network administrator is seeking a device monitoring method with specific requirements: explicit user privilege management, centralized logging of changes, widely accessible remote management, and support for service accounts. Let’s evaluate how SIEM (Security Information and Event Management) meets these needs and why it is the best fit compared to the other options.
C. SIEM (Security Information and Event Management):
Explicit, by user, privilege management: SIEM solutions allow administrators to define and manage user roles and permissions, ensuring that only authorized users can access or modify monitoring data and configurations.
Centralized logging of changes:
SIEM systems aggregate and store logs from various devices and systems in a centralized location, providing a comprehensive record of changes, events, and potential security incidents.
Widely accessible remote management:
SIEM platforms are typically cloud-based or accessible via web interfaces, enabling remote management from anywhere with an internet connection, often with role-based access control.
Support of service accounts:
SIEM can integrate with service accounts for automated monitoring tasks or system-to-system authentication, ensuring that non-human accounts (e.g., for scripts or applications) are supported.
Why it fits:
SIEM is designed for real-time monitoring, analysis, and reporting of security events across a network, making it an ideal choice for these requirements in a network administration context.
Why Not the Other Options?
A. SNMP (Simple Network Management Protocol):
SNMP is a protocol for monitoring and managing devices on a network (e.g., routers, switches). It supports basic monitoring and remote management but lacks robust privilege management (typically relies on community strings with limited security), centralized logging (logs are device-specific unless integrated with another system), and explicit support for service accounts. It’s more of a monitoring tool than a comprehensive management solution.
B. API (Application Programming Interface):
An API is a set of rules for software interaction, not a monitoring method itself. While APIs can be used to build custom monitoring solutions with privilege management and remote access, they require significant development and don’t inherently provide centralized logging or service account support without additional implementation. This makes it less suitable as a standalone solution.
D. SSO (Single Sign-On):
SSO is an authentication method that allows users to access multiple systems with one set of credentials. It supports privilege management and remote access but does not provide device monitoring, centralized logging of changes, or support for service accounts as a primary function. It’s a security feature, not a monitoring solution.
Why SIEM?
SIEM platforms (e.g., Splunk, IBM QRadar, or ArcSight) are specifically designed to meet the needs of network administrators by providing a centralized dashboard for monitoring, detailed logging for auditing, and flexible access controls. They can integrate with various devices and support service accounts through authentication mechanisms, making them the closest match to the listed requirements. For example, a SIEM could log a network device configuration change, restrict access to authorized users only, and allow the administrator to manage it remotely via a secure web interface.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.3 – "Given a scenario, implement secure network configurations." This includes understanding monitoring tools like SIEM for logging and management.
NIST SP 800-137 (Information Security Continuous Monitoring):
Describes SIEM as a tool for centralized logging and privilege management in network monitoring.
Vendor Documentation (e.g., Splunk, QRadar):
Highlights SIEM features like role-based access, centralized event logging, and remote management capabilities.
A network engineer is testing a website to ensure it is compatible with IPv6. After attempting to ping the website by its IPv6 address, the engineer determines that the DNS has not been set up properly. Which of the following should the network engineer complete to resolve this issue?
A. Enable a PTR record.
B. Update the existing TXT record.
C. Add a new AAAA record.
D. Configure a secondary NS record.
Explanation:
The network engineer is testing a website’s compatibility with IPv6 and finds that pinging the website by its IPv6 address fails due to improper DNS setup. This indicates that the DNS is not correctly resolving the website’s domain name to its IPv6 address. To resolve this, the engineer needs to ensure the DNS includes the appropriate record for IPv6.
C. Add a new AAAA record:
A AAAA (quad-A) record is the DNS record type used to map a domain name to an IPv6 address. If the website’s IPv6 address is not resolving, it’s likely because no AAAA record exists for the domain. Adding a new AAAA record with the website’s IPv6 address (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) will allow DNS to resolve the domain to its IPv6 address, enabling connectivity and testing.
This directly addresses the issue of IPv6 compatibility and the failed ping attempt.
Why Not the Other Options?
A. Enable a PTR record:
A PTR (Pointer) record is used for reverse DNS lookups, mapping an IP address to a domain name (e.g., for verifying the origin of an IP). While useful for security or email validation, it is not required for forward resolution of a domain to an IPv6 address, which is the issue here. Enabling a PTR record alone won’t fix the inability to ping the website by its IPv6 address
.
B. Update the existing TXT record:
A TXT (Text) record is used for storing arbitrary text data, often for SPF, DKIM, or domain verification purposes. It is unrelated to resolving IPv6 addresses and won’t help with the website’s IPv6 compatibility or ping failure.
D. Configure a secondary NS record:
A NS (Name Server) record specifies the authoritative name servers for a domain. Adding a secondary NS record provides redundancy for DNS resolution but does not address the lack of an IPv6 address mapping. The primary issue is the missing AAAA record, not a lack of name server redundancy.
Why AAAA Record?
The engineer’s test involves pinging the website by its IPv6 address, suggesting the domain should resolve to an IPv6 address via DNS. Without an AAAA record, the DNS server cannot provide the IPv6 address, causing the ping to fail. Adding the AAAA record ensures the domain is associated with its IPv6 address, enabling IPv6 connectivity. After adding the record, the engineer should verify resolution using a tool like nslookup -type=AAAA domain.com or dig AAAA domain.com.
Steps to Resolve:
Log in to the DNS management interface (e.g., domain registrar or DNS provider).
Create a new AAAA record for the website’s domain (e.g., www.example.com) with the corresponding IPv6 address.
Allow time for DNS propagation (typically up to 24–48 hours, though often faster).
Retest by pinging the domain with the IPv6 address.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 1.4 – "Explain the purposes and uses of network addressing and name resolution." This includes understanding DNS records like AAAA for IPv6.
RFC 3596:
Defines the AAAA record for IPv6 address mapping in DNS.
ICANN DNS Guidelines:
Recommends using AAAA records to support IPv6 compatibility for websites.
An IT department asks a newly hired employee to use a personal laptop until the company can provide one. Which of the following policies is most applicable to this situation?
A. IAM
B. BYOD
C. DLP
D. AUP
Explanation:
The IT department has asked a newly hired employee to use a personal laptop until a company-provided device is available. This situation falls under the BYOD (Bring Your Own Device) policy, which allows employees to use their personal devices for work purposes.
B. BYOD (Bring Your Own Device):
A BYOD policy governs the use of personal devices (e.g., laptops, smartphones) for accessing company networks, data, or applications. In this case, the employee using a personal laptop aligns with BYOD, and the company would likely need to enforce security measures (e.g., VPNs, device encryption) and usage guidelines to protect sensitive data.
This policy is most applicable as it directly addresses the scenario of using a personal device for work.
Why Not the Other Options?
A. IAM (Identity and Access Management):
IAM focuses on managing user identities and controlling access to systems and resources. While IAM might be involved in securing the employee’s access via the personal laptop (e.g., through authentication), it is a broader security framework and not specific to the use of personal devices.
C. DLP (Data Loss Prevention):
DLP policies are designed to prevent unauthorized access, use, or distribution of sensitive data. While DLP might be applied to the personal laptop to protect company data, it is a security measure rather than the policy governing the use of the device itself.
D. AUP (Acceptable Use Policy):
An AUP defines acceptable behaviors and usage of company IT resources. It could apply once the employee uses the laptop (e.g., outlining what they can or cannot do), but it is a general policy that applies to all users and devices, not specifically to the scenario of using a personal device temporarily.
Why BYOD?
The BYOD policy is tailored to situations where employees bring and use their own devices for work, addressing security, compliance, and support considerations. In this case, the company may need to implement a BYOD policy to ensure the personal laptop meets security standards (e.g., updated OS, antivirus) and to define the employee’s responsibilities until a company device is provided. This is a common practice in organizations facing equipment shortages or onboarding delays.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.3 – "Given a scenario, implement secure network configurations." This includes understanding policies like BYOD for device management.
NIST SP 800-124 (Guidelines for Managing and Securing Mobile Devices):
Discusses BYOD policies for securing personal devices in the workplace.
Corporate IT Policy Frameworks:
Highlight BYOD as a specific policy for managing personal device usage in professional settings.
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
A. SIEM
B. Syslog
C. NetFlow
D. SNMPv3
Explanation:
The network administrator is planning to implement device monitoring to enhance network visibility, with the requirement that the solution provides authentication and encryption. Let’s evaluate the options to determine the best fit:
D. SNMPv3 (Simple Network Management Protocol version 3):
Device Monitoring and Network Visibility: SNMPv3 is a protocol designed for monitoring and managing devices on a network (e.g., routers, switches, servers), providing detailed visibility into device performance, traffic, and status.
Authentication and Encryption:SNMPv3 introduces security features that previous versions (e.g., SNMPv1, SNMPv2c) lack, including user-based authentication (e.g., via usernames and passwords or MD5/SHA hashing) and encryption of data (e.g., using DES or AES) to protect communication between the management system and devices. This meets the requirement for a secure monitoring solution.
Why it fits: SNMPv3 is widely used for network device monitoring with built-in security, making it an ideal choice for enhancing visibility while ensuring data integrity and confidentiality.
Why Not the Other Options?
A. SIEM (Security Information and Event Management):
SIEM provides centralized logging, analysis, and monitoring of security events across the network, offering visibility and security features like authentication. However, SIEM is not a monitoring protocol itself but a system that aggregates data from other sources (e.g., logs, SNMP). It relies on underlying protocols like SNMPv3 for device monitoring and does not inherently provide encryption or authentication for the monitoring process unless configured with secure data feeds.
B. Syslog:
Syslog is a protocol for sending log messages from devices to a central server, providing visibility into system events. However, it lacks built-in authentication and encryption by default (though secure variants like TLS can be configured). It is more of a logging mechanism than a comprehensive device monitoring solution with security features.
C. NetFlow:
NetFlow (or similar technologies like sFlow) is used to collect and analyze network traffic flow data, offering visibility into traffic patterns. While it can enhance network monitoring, it does not provide authentication or encryption as part of its core functionality. Security would need to be added via external measures (e.g., encrypted transport).
Why SNMPv3?
SNMPv3 is specifically designed to address the security shortcomings of earlier SNMP versions by incorporating authentication (to verify the identity of users or devices) and encryption (to protect data in transit). This makes it suitable for monitoring devices in a secure manner, aligning with the administrator’s requirements for both visibility and security. For example, an SNMPv3 manager can securely poll devices for metrics like CPU usage or interface status, ensuring that the data is protected from unauthorized access or tampering.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.3 – "Given a scenario, implement secure network configurations." This includes understanding secure monitoring protocols like SNMPv3.
RFC 3414 (User-based Security Model for SNMPv3):
Defines authentication and encryption features in SNMPv3.
Cisco Networking Documentation:
Highlights SNMPv3 as a secure version of SNMP for network device monitoring with authentication and privacy options.
A network engineer is completing a wireless installation in a new building. A requirement is that all clients be able to automatically connect to the fastest supported network. Which of the following best supports this requirement?
A. Enabling band steering
B. Disabling the 5GHz SSID
C. Adding a captive portal
D. Configuring MAC filtering
E. Configuring MAC filtering
Explanation:
The network engineer is installing a wireless network in a new building with a requirement that all clients automatically connect to the fastest supported network. This implies the need for clients to connect to the 5GHz band (which typically offers higher speeds than the 2.4GHz band) when available, without manual intervention. The best solution to meet this requirement is enabling band steering.
A. Enabling band steering:
How it works: Band steering is a feature on dual-band wireless access points (APs) that encourages or directs compatible client devices to connect to the 5GHz band (faster and less congested) instead of the 2.4GHz band. It does this by either preferring the 5GHz band for new connections or steering clients away from 2.4GHz when 5GHz is available, based on signal strength and client capability.
Why it fits: This ensures that clients automatically connect to the fastest supported network (5GHz) when their devices support it, meeting the requirement without requiring user action. For example, a laptop with dual-band capability will be guided to 5GHz, which offers higher throughput due to wider channels and less interference.
Considerations: Band steering requires compatible client devices and proper AP configuration (e.g., overlapping coverage and balanced load).
Why Not the Other Options?
B. Disabling the 5GHz SSID:
Disabling the 5GHz band entirely eliminates the option for clients to connect to the faster network, forcing all connections to the slower 2.4GHz band. This directly contradicts the requirement for automatic connection to the fastest supported network.
C. Adding a captive portal:
A captive portal is used for authentication (e.g., requiring users to log in) and does not influence which band (2.4GHz or 5GHz) clients connect to. It has no impact on automatically selecting the fastest network.
D. Configuring MAC filtering:
MAC filtering controls which devices can connect to the network based on their MAC addresses, but it does not determine the band selection or ensure connection to the fastest network. It’s a security feature, not a band management tool.
E. Configuring MAC filtering (repeated):
As with option D, this is irrelevant to the requirement of automatic connection to the fastest network.
Why Band Steering?
In a dual-band wireless environment, the 5GHz band typically provides higher speeds (e.g., up to 1-2 Gbps with 802.11ac/ax) compared to the 2.4GHz band (e.g., up to 150-600 Mbps), due to wider channels and less interference. However, not all clients automatically prefer 5GHz unless configured to do so. Band steering optimizes the network by leveraging the faster band for capable devices, ensuring the requirement is met without manual user intervention. The engineer should configure the APs to enable band steering and verify that the 5GHz coverage is adequate across the building.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 2.2 – "Given a scenario, configure and deploy common network devices." This includes configuring wireless APs with features like band steering.
IEEE 802.11 Standards:
Defines dual-band operation (2.4GHz and 5GHz) and the role of band steering in optimizing wireless performance.
Cisco Wireless Deployment Guides:
Recommend band steering to automatically direct clients to the 5GHz band for better performance.
Which of the following connector types would most likely be used to connect to an external antenna?
A. BNC
B. ST
C. LC
D. MPO
Explanation:
The question asks about the connector type most likely used to connect to an external antenna, which is a common requirement in wireless networking or radio frequency (RF) applications. Let’s evaluate the options:
A. BNC (Bayonet Neill-Concelman):
Use Case: BNC connectors are widely used in RF applications, including connecting external antennas to wireless access points, routers, or radio equipment. They are known for their bayonet-style locking mechanism, which provides a secure connection for coaxial cables carrying RF signals.
Why it fits: BNC connectors are a standard choice for external antenna connections in networking devices, especially in older or industrial-grade wireless systems (e.g., Wi-Fi access points or point-to-multipoint radios). They support the impedance (typically 50 ohms) required for antenna systems and are durable for outdoor use.
Example: A network administrator might use a BNC connector to attach an external omnidirectional antenna to a wireless bridge.
Why Not the Other Options?
B. ST (Straight Tip):
ST connectors are fiber optic connectors with a push-pull coupling mechanism, commonly used in Ethernet or fiber-based networks (e.g., connecting fiber patch panels). They are not designed for RF signals or external antennas, making them unsuitable.
C. LC (Lucent Connector):
LC connectors are small-form-factor fiber optic connectors used in high-density fiber optic applications (e.g., data centers or SFP modules). They are irrelevant to RF or antenna connections.
D. MPO (Multi-Fiber Push-On):
MPO connectors are multi-fiber optic connectors used for high-speed data transmission in fiber optic cables (e.g., 40G/100G Ethernet). They are not applicable to external antenna connections, which require coaxial or RF-specific connectors.
Why BNC?
BNC connectors are historically and practically the most likely choice for connecting external antennas in networking contexts, particularly in wireless installations. While other RF connectors like SMA, RP-SMA, or N-type might also be used in modern systems (especially for higher frequencies or outdoor antennas), BNC remains a recognized standard in the CompTIA Network+ (N10-009) curriculum for this purpose due to its widespread use in legacy and mid-range equipment. The question’s focus on “most likely” aligns with BNC given its commonality in networking scenarios.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 2.1 – "Explain the characteristics of network topologies and types." This includes understanding connector types, including BNC for RF applications.
IEEE 802.11 Wireless Standards:
References BNC as a connector type for early wireless antenna connections.
Cable and Connector Guides (e.g., Fluke Networks):
Identify BNC as a standard for coaxial connections to external antennas.
Which of the following facilities is the best example of a warm site in the event of information system disruption?
A. A combination of public and private cloud services to restore data
B. A partial infrastructure, software, and data on site
C. A full electrical infrastructure in place, but no customer devices on site
D. A full infrastructure in place, but no current data on site
Explanation:
In the context of disaster recovery and business continuity, a warm site is a facility that provides an intermediate level of readiness for restoring information systems after a disruption. It balances cost and recovery time, offering partial infrastructure, software, and data that can be quickly activated, typically within hours to a day. Let’s evaluate the options:
B. A partial infrastructure, software, and data on site:
Definition Fit: A warm site includes pre-installed hardware (e.g., servers, networking equipment) and some software, with a portion of critical data replicated or backed up. It requires minimal setup (e.g., restoring additional data or configuring applications) to become operational, aligning with the warm site concept.
Why it fits: This option reflects a warm site’s characteristics—partially equipped and ready for use, allowing for a reasonable recovery time objective (RTO) without the full expense of a hot site. For example, a company might use this site to restore core services after a disruption, completing data synchronization from backups.
Recovery Time: Typically, a warm site can be operational within 12–24 hours, depending on the extent of data restoration.
Why Not the Other Options?
A. A combination of public and private cloud services to restore data:
This describes a cloud-based disaster recovery solution, which could be part of a hot site (immediate access) or cold site (longer setup) depending on configuration. However, it lacks the physical infrastructure of a traditional warm site and is more aligned with modern hybrid recovery strategies, not a specific facility type.
C. A full electrical infrastructure in place, but no customer devices on site:
This resembles a cold site, which has basic infrastructure (e.g., power, space) but requires significant setup (e.g., installing hardware and data) before use. Cold sites are cheaper but have a longer RTO (days to weeks), making this less suitable for a warm site.
D. A full infrastructure in place, but no current data on site:
This describes a hot site, which has fully operational hardware, software, and infrastructure with real-time or near-real-time data replication. Hot sites are ready for immediate use (minutes to hours) but are more expensive, distinguishing them from the partial readiness of a warm site.
Why Partial Infrastructure, Software, and Data?
A warm site strikes a balance between cost and readiness. It includes enough infrastructure and data to resume critical operations quickly, but it’s not fully redundant like a hot site, nor as bare-bones as a cold site. For instance, a warm site might have servers and a basic network setup with daily data backups, requiring only the latest incremental backups to be restored—fitting the scenario of a partial setup.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.5 – "Explain common mitigation techniques and their purposes." This includes understanding disaster recovery sites like warm sites.
NIST SP 800-34 (Contingency Planning Guide):
Defines warm sites as partially equipped facilities with some data and infrastructure for quicker recovery than cold sites.
Business Continuity Institute (BCI) Guidelines:
Describes warm sites as a middle ground with partial resources ready for activation
A network technician is troubleshooting a faulty NIC and tests the theory. Which of the following should the technician do next?
A. Develop a theory.
B. Establish a plan of action.
C. Implement the solution.
D. Document the findings
Explanation:
The network technician is troubleshooting a faulty Network Interface Card (NIC) and has already tested the theory, which is a step in the troubleshooting process. Based on the CompTIA troubleshooting methodology, the next logical step after testing a theory is to establish a plan of action.
Troubleshooting Process Overview:
Identify the problem: Gather information and define the issue (e.g., faulty NIC).
Develop a theory: Formulate potential causes (e.g., driver issue, hardware failure).
Test the theory: Verify the cause through testing (e.g., swapping the NIC, checking diagnostics).
Establish a plan of action: Outline the steps to resolve the issue based on the test results.
Implement the solution: Execute the plan (e.g., replace the NIC).
Verify functionality: Confirm the issue is resolved.
Document findings: Record the process and outcome.
Why B. Establish a plan of action?
Since the technician has tested the theory and presumably confirmed the cause of the faulty NIC (e.g., hardware failure or configuration issue), the next step is to create a plan. This plan might include actions like replacing the NIC, updating drivers, or reconfiguring settings, depending on the test outcome. Establishing a plan ensures a structured approach to resolution, minimizing risks and downtime.
Why Not the Other Options?
A. Develop a theory:
This step comes before testing the theory. Since the technician has already tested it, this is no longer the next step.
C. Implement the solution:
Implementation follows the establishment of a plan. Acting without a plan could lead to incomplete or incorrect fixes.
D. Document the findings:
Documentation is the final step after verifying the solution works, to record the process and lessons learned. It’s premature at this stage.
Why This Step?
After testing confirms the NIC issue (e.g., no link lights or failed loopback test), the technician needs to decide on the best course of action—e.g., replacing the hardware, updating firmware, or escalating to a vendor. A plan ensures all necessary tools, permissions, and steps are prepared before implementation.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.2 – "Given a scenario, troubleshoot common network connectivity issues." This includes following the structured troubleshooting methodology.
CompTIA A+ and Network+ Study Guides:
Emphasize the sequence of troubleshooting steps, with "establish a plan of action" following theory testing.
A network administrator is configuring access points for installation in a dense environment where coverage is often overlapping. Which of the following channel widths should the administrator choose to help minimize interference in the 2.4GHz spectrum?
A. 11MHz
B. 20MHz
C. 40MHz
D. 80MHz
E. 160MHz
Explanation:
The network administrator is configuring access points (APs) in a dense environment with overlapping coverage, aiming to minimize interference in the 2.4GHz spectrum. The choice of channel width plays a critical role in managing interference, especially in crowded wireless environments.
B. 20MHz:
How it works: In the 2.4GHz band, which has only three non-overlapping channels (1, 6, and 11), a 20MHz channel width uses the full bandwidth of these channels without overlapping with adjacent channels when properly configured. This minimizes co-channel and adjacent-channel interference, which is a significant concern in dense deployments with overlapping APs.
Why it fits: In a dense environment, narrower channel widths like 20MHz reduce the likelihood of interference by allowing more APs to operate on non-overlapping channels (1, 6, 11) without overlap. Wider channels (e.g., 40MHz or 80MHz) exceed the 2.4GHz band’s capacity, causing significant overlap and interference, degrading performance.
Considerations: Using 20MHz ensures better coexistence with other Wi-Fi networks and non-Wi-Fi devices (e.g., Bluetooth, microwaves) that also operate in the 2.4GHz band.
Why Not the Other Options?
A. 11MHz:
This is not a standard channel width for Wi-Fi. The 2.4GHz band uses 20MHz as the base channel width, with options to extend to 40MHz in some cases. An 11MHz width is not supported by 802.11 standards, making it invalid.
C. 40MHz:
A 40MHz channel width combines two 20MHz channels, but in the 2.4GHz band, there are only three non-overlapping 20MHz channels (1, 6, 11). Using 40MHz would result in significant overlap (e.g., channels 1-5 or 6-10), increasing interference, especially in a dense environment. This is generally avoided in 2.4GHz due to limited spectrum.
D. 80MHz:
An 80MHz channel width is far too wide for the 2.4GHz band, which has a total usable bandwidth of approximately 83.5MHz. This would cause extreme overlap and interference, rendering it impractical and unsuitable for dense deployments.
E. 160MHz:
This width is designed for the 5GHz band (where more spectrum is available) and is completely incompatible with the 2.4GHz band’s limited capacity, leading to maximum interference and poor performance.
Why 20MHz?
The 2.4GHz band is congested due to its limited number of non-overlapping channels and widespread use by various devices. In a dense environment with overlapping coverage, using 20MHz channels allows the administrator to assign APs to channels 1, 6, and 11, minimizing interference. Wider channels (40MHz or more) are better suited for the 5GHz band, where more non-overlapping channels are available. For optimal performance, the administrator should also use tools like a spectrum analyzer to adjust channel assignments and reduce overlap.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 2.2 – "Given a scenario, configure and deploy common network devices." This includes configuring wireless APs and managing channel widths to reduce interference.
IEEE 802.11 Standards:
Define channel widths and the three non-overlapping 20MHz channels (1, 6, 11) in the 2.4GHz band.
Cisco Wireless Design Guides:
Recommend 20MHz channels in the 2.4GHz band for dense environments to minimize interference.
A network administrator has been tasked with configuring a network for a new corporate office. The office consists of two buildings, separated by 50 feet with no physical connectivity. The configuration must meet the following requirements:
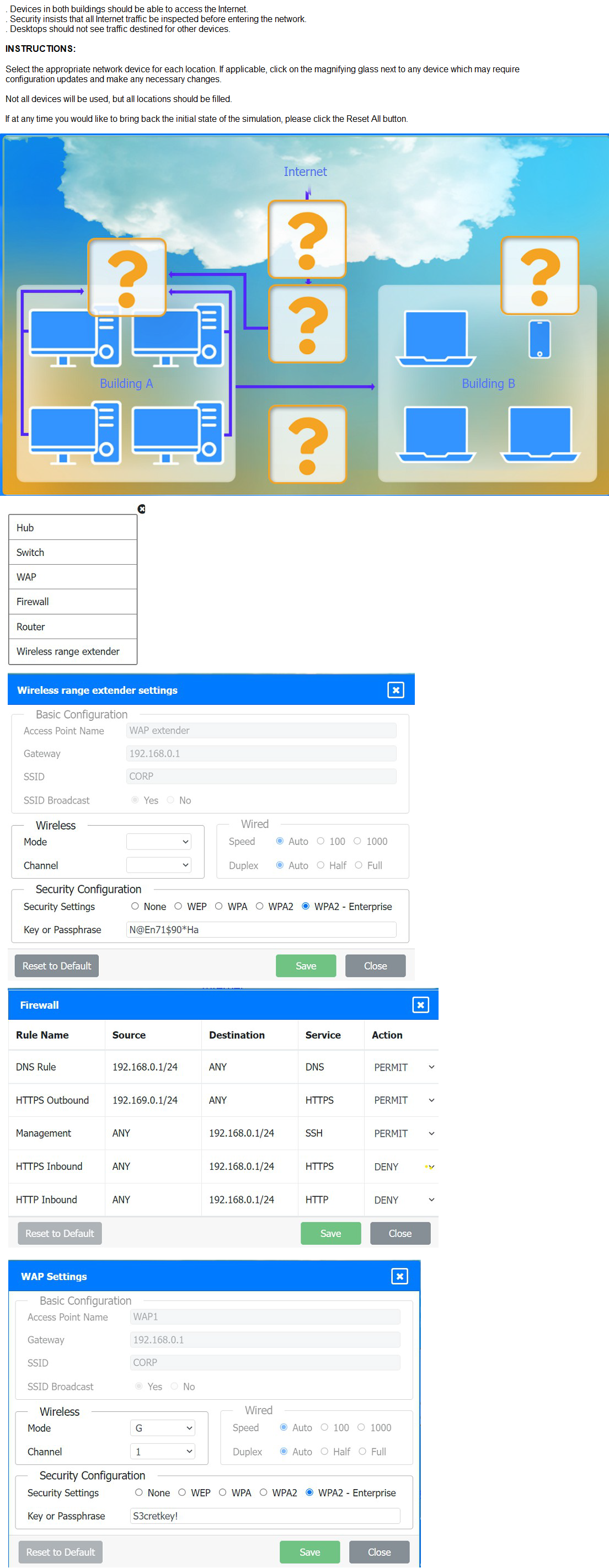
Analysis and Required Adjustments:
The current configuration has several issues that need to be addressed to meet the requirements:
Single Subnet Issue: Both the WAP and WAP Extender are configured with gateways in the 192.168.1.0/24 subnet (192.168.1.0 and 192.168.1.1), suggesting they are part of the same network. However, the WAP Extender’s gateway (192.168.1.1) should typically be the router or AP it connects to, not a different IP in the same subnet unless it’s a relay. This could cause IP conflicts or routing issues.
Channel Overlap:
Both the WAP (Channel 1) and WAP Extender (channel not specified, likely defaulting to 1 or overlapping) may interfere with each other over 50 feet, especially in a dense environment.
Security Mismatch:
The WAP and WAP Extender use different WPA2 passphrases (5zcret!ey1 vs. N@e71590!Ha), which could prevent seamless roaming unless clients are configured for both.
Firewall Restrictions:
The firewall blocks inbound HTTP (Rules 4 and 5), which might prevent inter-building communication if desktops use HTTP for file sharing or other services, unless SSH or HTTPS is used instead.
Internet Access:
The router’s role is unclear, but the firewall rules suggest internet access (DNS, HTTPS) is permitted, assuming the router is configured correctly.
Steps to Meet Requirements
To ensure desktops in both buildings can access the internet and each other, the administrator should:
Verify and Adjust IP Configuration:
Ensure the WAP (192.168.1.0) and WAP Extender (gateway 192.168.1.1) are on the same subnet (192.168.1.0/24) with no IP conflicts. The WAP Extender should use 192.168.1.1 as its gateway, pointing to the router or WAP.
Confirm the router’s IP (e.g., 192.168.1.1) is the default gateway for all devices.
Optimize Wireless Channels:
Set the WAP to Channel 1 and the WAP Extender to Channel 6 or 11 to minimize interference over 50 feet. This leverages the three non-overlapping channels (1, 6, 11) in the 2.4GHz band.
Use a site survey tool to adjust if interference persists.
Standardize Security Settings:
Update the WAP Extender’s passphrase to match the WAP (5zcret!ey1) to ensure seamless client roaming between Building A and Building
B.
Adjust Firewall Rules:
Modify or add a rule to permit inter-building traffic (e.g., Source 192.168.1.0/24, Destination 192.168.1.0/24, Service ANY, Action PERMIT) if desktops need to communicate using protocols beyond SSH or HTTPS.
Ensure the DENY rule for HTTP inbound is intentional and doesn’t block required services.
Test Connectivity:
Verify that desktops in both buildings can ping each other (e.g., 192.168.1.x to 192.168.1.y) and access the internet (e.g., ping 8.8.8.8).
Check for roaming by moving a client device between buildings.
Final Configuration:
WAP Settings:
Gateway: 192.168.1.1 (router)
SSID: CORP
Channel:1
Security: WPA2,
Passphrase: 5zcret!ey1
WAP Extender Settings:
Gateway: 192.168.1.1 (router)
SSID: CORP
Channel:6
Security: WPA2,
Passphrase: 5zcret!ey1
Router: Ensure it provides NAT and routing to the internet, with 192.168.1.1 as the gateway.
Firewall:
Adjust rules to permit inter-building traffic if needed.
Conclusion
With these adjustments, desktops in both Building A and Building B should be able to access the internet (via the router and firewall-permitted services) and each other (via the unified wireless network and adjusted firewall rules). The 50-foot separation is manageable with a wireless range extender, and the configuration aligns with the N10-009 focus on wireless network setup.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 2.2 – "Given a scenario, configure and deploy common network devices." This includes configuring WAPs, extenders, and firewalls.
IEEE 802.11 Standards:
Guide channel selection and security settings for wireless networks.
Cisco Wireless Deployment Guides:
Recommend channel planning and security standardization for multi-AP environments.
| Page 14 out of 43 Pages |
