Which of the following allows for the interception of traffic between the source and destination?
A. Self-signed certificate
B. VLAN hopping
C. On-path attack
D. Phishing
Explanation:
On-path attack (formerly "man-in-the-middle" attack) allows an attacker to intercept and potentially alter traffic between the source and destination.
Examples: ARP spoofing, rogue access points, or DNS spoofing.
The attacker secretly relays or modifies communications without either party knowing.
Why Not the Other Options?
A) Self-signed certificate
Incorrect: Self-signed certificates may trigger browser warnings but do not inherently intercept traffic.
B) VLAN hopping
Incorrect: VLAN hopping exploits switch misconfigurations to access restricted VLANs, not intercept traffic.
D) Phishing
Incorrect: Phishing tricks users into revealing data (e.g., via fake emails) but does not intercept live traffic.
Reference:
CompTIA Security+ SY0-601 (Objective 1.4 - On-Path Attacks)
MITRE ATT&CK T1557 (Adversary-in-the-Middle)
A company implements a video streaming solution that will play on all computers that have joined a particular group, but router ACLs are blocking the traffic. Which of the following is the most appropriate IP address that will be allowed in the ACL?
A. 127.0.0.1
B. 172.17.1.1
C. 224.0.0.1
D. 240.0.0.1
Explanation:
224.0.0.1 is the correct choice because it is the multicast IP address for the "all-hosts" group, used for video streaming and other multicast applications.
Multicast efficiently delivers traffic to multiple recipients (e.g., video streams) without flooding the network.
Router ACLs must permit this address (and the multicast range 224.0.0.0/4) for multicast traffic to pass.
Why Not the Other Options?
A) 127.0.0.1
Incorrect: This is the loopback address (local machine only), not used for network traffic.
B) 172.17.1.1
Incorrect: This is a unicast private IP (RFC 1918), not suitable for multicast streaming.
D) 240.0.0.1
Incorrect: Addresses in the 240.0.0.0/4 range are reserved for future use (not multicast).
Reference:
CompTIA Network+ Objective 1.4 (Multicast Addressing)
RFC 5771 (Multicast Address Assignments)
Which of the following routing protocols is most commonly used to interconnect WANs?
A. IGP
B. EIGRP
C. BGP
D. OSPF
Explanation:
The most commonly used routing protocol to interconnect Wide Area Networks (WANs), particularly across different autonomous systems (e.g., between Internet Service Providers or large organizations), is Border Gateway Protocol (BGP). BGP is designed for exchanging routing information between different networks on the internet or large-scale WANs, making it the standard for interconnecting disparate networks.
Here’s why the other options are less likely:
A. IGP (Interior Gateway Protocol):
IGP is a category of routing protocols, not a specific protocol. It includes protocols like OSPF, RIP, and EIGRP, which are used within a single autonomous system (e.g., within an organization’s internal network). IGPs are not typically used for interconnecting WANs across different autonomous systems, as they lack the scalability and policy control needed for external routing.
B. EIGRP (Enhanced Interior Gateway Routing Protocol):
EIGRP is an advanced distance-vector routing protocol developed by Cisco. It is primarily used within a single autonomous system (e.g., within an enterprise network) and is not designed for interconnecting WANs across different organizations or ISPs. EIGRP is less common in WAN interconnection compared to BGP.
D. OSPF (Open Shortest Path First):
OSPF is a link-state routing protocol used within a single autonomous system, typically for internal enterprise networks. While it is efficient for managing routing within a large organization, it is not commonly used for interconnecting WANs across different networks or ISPs, as it lacks the robust policy mechanisms and scalability of BGP.
Why BGP?
BGP is the de facto standard for interconnecting WANs, especially on the internet, because it is an External Gateway Protocol (EGP) designed to handle routing between different autonomous systems (ASes). It supports complex routing policies, scalability for large networks, and the ability to manage the vast number of routes on the internet. BGP is used by ISPs, cloud providers, and large enterprises to exchange routing information across WANs, ensuring efficient and reliable data transfer between disparate networks. There are two main types of BGP:
eBGP (External BGP):
Used between different autonomous systems (e.g., between two ISPs).
iBGP (Internal BGP):
Used within a single autonomous system to distribute external routes internally.
For example, when two ISPs connect their networks to provide internet connectivity, they use BGP to exchange routing tables and determine the best paths for data across the WAN.
Reference:
CompTIA Network+ (N10-009) Exam Objectives: Section 1.5 – "Compare and contrast common network protocols and their functions." This includes understanding routing protocols like BGP for WAN connectivity.
RFC 4271:
Defines BGP-4, the current version of the Border Gateway Protocol, outlining its role in inter-domain routing across WANs.
Cisco Networking Resources:
BGP is described as the primary protocol for interconnecting autonomous systems in WAN environments, widely used in ISP and enterprise WAN scenarios.
A company recently converted most of the office laptops to connect wirelessly to the corporate network. After a high-traffic malware attack, narrowing the event to a specific user was difficult because of the wireless configuration. Which of the following actions should the company take?
A. Restrict users to the 5GHz frequency.
B. Upgrade to a mesh network.
C. Migrate from PSK to Enterprise.
D. Implement WPA2 encryption.
Explanation:
The issue described in the question involves difficulty in tracking a specific user responsible for a high-traffic malware attack on a wireless network. This is likely due to the use of a Pre-Shared Key (PSK) authentication method, which is common in simpler wireless configurations like WPA2-Personal. With PSK, all users share the same key, making it challenging to attribute network activity to a specific user. To address this, the company should migrate from PSK to Enterprise (WPA2-Enterprise or WPA3-Enterprise), which provides individual user authentication and better tracking capabilities.
Here’s why the other options are less suitable:
A. Restrict users to the 5GHz frequency:
Restricting users to the 5GHz frequency improves bandwidth and reduces interference compared to 2.4GHz, but it does not address user identification or tracking. It has no direct impact on attributing network activity to specific users during a malware attack
.
B. Upgrade to a mesh network:
A mesh network enhances wireless coverage and reliability by using multiple access points that work together. However, it does not inherently improve user authentication or tracking, so it wouldn’t help narrow down the source of a malware attack.
D. Implement WPA2 encryption:
WPA2 encryption is likely already in use, as it is a standard security protocol for modern wireless networks (especially in corporate environments). The issue isn’t the encryption itself but the authentication method (PSK vs. Enterprise). Implementing WPA2 doesn’t address the lack of user-specific tracking
.
Why Migrate from PSK to Enterprise?
PSK (Pre-Shared Key):
In WPA2-Personal (or WPA3-Personal), all devices use a single shared key for authentication. This makes it difficult to track individual users because there’s no unique identifier for each user’s session. If a malware attack occurs, logs may show activity from the shared key but not from a specific user.
Enterprise (WPA2-Enterprise or WPA3-Enterprise):
This mode uses a RADIUS server for authentication, requiring each user to log in with unique credentials (e.g., username and password) via protocols like EAP (Extensible Authentication Protocol). This creates individual user sessions, making it easier to track network activity to a specific user in logs. For example, during a malware investigation, the RADIUS server logs can identify which user’s credentials were associated with malicious traffic.
Benefits for Malware Investigation:
Enterprise mode enables better auditing and accountability, which is critical for identifying the source of a malware attack. It also integrates with directory services (e.g., Active Directory) for centralized user management, enhancing security in corporate environments.
Implementation Steps for WPA2-Enterprise:
Set up a RADIUS server (e.g., FreeRADIUS or Microsoft NPS) to handle authentication.
Configure the wireless access points to use WPA2-Enterprise with EAP (e.g., EAP-TLS or PEAP).
Create unique user accounts or certificates for each employee.
Update client devices to connect using Enterprise credentials.
Monitor logs on the RADIUS server and wireless controller to track user activity.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.3 – "Given a scenario, implement secure network configurations." This includes configuring secure wireless networks and authentication methods like WPA2-Enterprise.
IEEE 802.11i:
Defines WPA2 security standards, including the difference between PSK (Personal) and Enterprise modes.
Cisco Wireless Security Guidelines:
Emphasize WPA2-Enterprise for corporate environments needing user accountability and tracking.
A network administrator notices uncommon communication between VMsonephemeral ports on the same subnet. The administrator is concerned about that traffic moving laterallywithin the network. Which of the following describes the type of traffic flow the administrator is analyzing?
A. East-west
B. Point-to-point
C. Horizontal-scaling
D. Hub-and-spoke
Explanation:
The scenario describes a network administrator observing unusual communication between virtual machines (VMs) on ephemeral ports within the same subnet, with concerns about lateral movement within the network. This type of traffic is best described as east-west traffic.
A. East-west:
East-west traffic refers to data flow between devices within the same network or data center, such as communication between VMs on the same subnet or between servers in a data center. In this case, the VMs communicating on the same subnet represent east-west traffic. Lateral movement, often associated with malware or attackers spreading within a network, is a common security concern for east-west traffic, as it involves devices within the same network segment. The use of ephemeral ports (temporary, high-numbered ports assigned for client-server communication) suggests dynamic, potentially suspicious activity, reinforcing the need to monitor this traffic.
B. Point-to-point:
Point-to-point refers to direct communication between two specific devices, often over a dedicated link (e.g., a VPN or leased line). While VM communication could be point-to-point in a technical sense, this term is less specific to the context of lateral movement within a subnet or data center and is not the best description for the scenario.
C. Horizontal-scaling:
Horizontal scaling refers to adding more machines or instances (e.g., VMs or servers) to handle increased load, typically in a distributed system. It is not a type of traffic flow but rather a system design concept, so it doesn’t apply to the administrator’s analysis of network traffic.
D. Hub-and-spoke:
Hub-and-spoke describes a network topology where traffic flows through a central device (the hub, e.g., a router or switch) to reach other devices (spokes). This model is more relevant to traffic moving between different subnets or sites, not communication between VMs on the same subnet, which is direct and doesn’t typically involve a central hub.
Why East-West Traffic?
East-west traffic is a critical concept in modern network security, especially in virtualized environments like data centers or cloud infrastructures. VMs on the same subnet can communicate directly without traversing a gateway, making it easier for malicious activity (e.g., malware or unauthorized access) to spread laterally. The administrator’s concern about lateral movement—where an attacker moves from one compromised device to another within the network—aligns directly with east-west traffic patterns. Monitoring and securing this traffic often involves tools like intrusion detection systems (IDS), firewalls with micro-segmentation, or network traffic analysis to detect unusual activity on ephemeral ports.
Reference:
CompTIA Network+ (N10-009) Exam Objectives: Section 3.2 – "Given a scenario, troubleshoot common network connectivity issues." This includes understanding network traffic patterns and identifying potential security issues like lateral movement.
NIST SP 800-207 (Zero Trust Architecture):
Discusses east-west traffic in the context of securing internal network communications, emphasizing the need to monitor and control lateral movement in virtualized environments.
VMware/Cisco Networking Documentation:
Defines east-west traffic as communication between devices within the same network or data center, contrasting it with north-south traffic (between the network and external entities like the internet).
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses, one for a computer and one for a phone connected to the network. Which of the following classful IPv4 address ranges will be best-suited for the network?
A. Class D
B. Class B
C. Class A
D. Class C
Explanation:
To determine the best-suited classful IPv4 address range for the new site, we need to calculate the total number of IP addresses required and match it to the appropriate classful address range. The site will initially have 150 users, growing by 10 users within a year, and each user requires two IP addresses (one for a computer and one for a phone). Let’s break it down:
Calculate IP address requirements:
Initial users:
150
Additional users in one year:
10
Total users:
150 + 10 = 160
IP addresses per user:
2 (computer + phone)
Total IP addresses needed:
160 × 2 = 320
Additional considerations:A few extra IP addresses are typically needed for network devices (e.g., routers, switches, or servers). Assuming a small number (e.g., 10–20 additional addresses), let’s estimate a total of approximately 340 IP addresses.
Classful IPv4 address ranges:
Class A:
Range 1.0.0.0 to 126.0.0.0, with a default subnet mask of /8 (255.0.0.0). Provides 2^24 – 2 = 16,777,214 host addresses. This is far too large for 340 IP addresses and would be inefficient.
Class B:
Range 128.0.0.0 to 191.255.0.0, with a default subnet mask of /16 (255.255.0.0). Provides 2^16 – 2 = 65,534 host addresses. This is also excessively large for the site’s needs.
Class C:
Range 192.0.0.0 to 223.255.255.0, with a default subnet mask of /24 (255.255.255.0). Provides 2^8 – 2 = 254 host addresses per subnet. Two Class C subnets (/24) would provide 2 × 254 = 508 host addresses, which is sufficient for 340 IP addresses.
Class D:
Range 224.0.0.0 to 239.255.255.255, used for multicast addresses, not for assignable host addresses. This is unsuitable for the network’s needs.
Why Class C?
A single Class C subnet (/24) provides 254 usable IP addresses, which is insufficient for 340 addresses. However, using two Class C subnets (e.g., 192.168.1.0/24 and 192.168.2.0/24) provides 508 usable addresses, comfortably accommodating the 320–340 required IP addresses with room for future growth or additional devices.
Class A and Class B ranges provide far more addresses than needed, leading to inefficient use of IP address space.
In modern networking, classful addressing is rarely used strictly, and Classless Inter-Domain Routing (CIDR) is more common. However, since the question specifies classful addressing, Class C is the smallest range that can meet the requirements with minimal waste (using two subnets).
Practical Considerations:
The network could use a single subnet with a larger mask, such as /23 (255.255.254.0, providing 510 usable addresses), but this is a classless approach and not an option in the question.
Two Class C subnets can be configured on the same network with proper routing or VLAN segmentation to manage the 150–160 users and their devices.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 1.4 – "Explain the purposes and uses of network addressing and name resolution." This includes understanding IPv4 address classes and their application in network design.
RFC 791 (Internet Protocol):
Defines the structure of IPv4 address classes (A, B, C, D, E).
Cisco Networking Academy:
Covers classful addressing and subnetting for network design, emphasizing Class C for small to medium-sized networks.
A small company has the following IP addressing strategy:
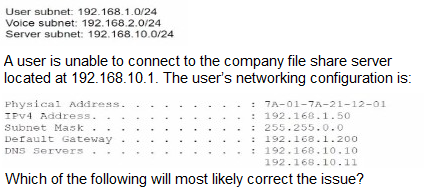
A. Changing the IPv4 address to 192.168.10.1
B. Changing the subnet mask to 255.255.255.0
C. Changing the DNS servers to internet IPs
D. Changing the physical address to 7A-01-7A-21-01-50
Explanation:
The user is unable to connect to the company file share server located at 192.168.10.1, and the issue stems from a mismatch in the network configuration. Let’s analyze the user’s configuration and the company’s IP addressing strategy to identify the problem:
Company IP Addressing Strategy:
User subnet: 192.168.1.0/24 (subnet mask 255.255.255.0)
Voice subnet: 192.168.2.0/24 (subnet mask 255.255.255.0)
Server subnet: 192.168.10.0/24 (subnet mask 255.255.255.0)
User’s Network Configuration:
IPv4 Address: 192.168.1.50
Subnet Mask: 255.255.0.0 (default /16, not matching the company’s /24)
Default Gateway: 192.168.1.1
DNS Servers: 192.168.10.11
Problem Analysis:
The user’s IP address (192.168.1.50) falls within the user subnet (192.168.1.0/24), and the default gateway (192.168.1.1) is likely the router for that subnet.
The file share server is on the 192.168.10.0/24 subnet, which is a different network from the user’s subnet (192.168.1.0/24).
The user’s subnet mask is set to 255.255.0.0 (/16), which incorrectly includes the server’s subnet (192.168.10.0) within the same network. With a /16 mask, the user’s device thinks the server (192.168.10.1) is on the same local network, but the router or switch configuration likely enforces the /24 boundaries, preventing direct communication without proper routing.
For the user to reach the server, the subnet mask must match the company’s strategy (255.255.255.0 /24), allowing the device to recognize that 192.168.10.1 is on a different subnet and send traffic to the default gateway for routing.
Why B. Changing the subnet mask to 255.255.255.0?
Changing the subnet mask from 255.255.0.0 to 255.255.255.0 aligns the user’s configuration with the company’s /24 subnets. This ensures the user’s device correctly identifies that the server (192.168.10.1) is on a different subnet, prompting it to send traffic to the default gateway (192.168.1.1) for routing to the 192.168.10.0/24 network.
With the correct subnet mask, the user’s device will have a network range of 192.168.1.0 to 192.168.1.255, and it will route traffic to 192.168.10.1 via the gateway, assuming proper routing is configured between the subnets.
Why Not the Other Options?
A. Changing the IPv4 address to 192.168.10.1:
This would place the user on the server subnet, but it doesn’t address the root issue (mismatched subnet mask) and could cause conflicts if 192.168.10.1 is already assigned to the server. The user should remain on the 192.168.1.0/24 subnet.
C. Changing the DNS servers to internet IPs:
The DNS servers (192.168.10.11) are on the server subnet, which is appropriate for internal resolution. Changing to internet IPs (e.g., Google DNS 8.8.8.8) might work for external access but won’t resolve the connectivity issue to the local file share server, which depends on proper subnet configuration, not DNS.
D. Changing the physical address to 7A-01-7A-21-01-50:
The physical address (MAC address) is unrelated to IP configuration or subnet issues. Changing it won’t affect IP-based connectivity to the server.
Additional Notes:
The issue assumes the network has routing enabled between the 192.168.1.0/24 and 192.168.10.0/24 subnets via the default gateway. If routing is not configured, the problem would persist even with the correct subnet mask, but the question implies a configuration fix is sufficient.
The image confirms the user’s subnet mask mismatch as the likely cause.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 1.4 – "Explain the purposes and uses of network addressing and name resolution." This includes configuring subnet masks for proper network segmentation.
RFC 950 (Internet Standard Subnetting Procedure):
Defines subnet masking and its role in network communication.
Microsoft Networking Documentation:
Explains how incorrect subnet masks can prevent communication between devices on different subnets.
A user cannot access an external server for a client after connecting to a VPN. Which of the following commands would a support agent most likely use to examine the issue? (Select two).
A. nslookup
B. tcpdump
C. arp
D. dig
E. tracert
F. route print
F. route print
Explanation:
A user cannot access an external server after connecting to a VPN, indicating a potential issue with routing or connectivity between the local network and the external server. The support agent would most likely use the following two commands to diagnose the issue:
E. tracert:
This command (known as traceroute on Unix-based systems) traces the path that packets take to reach the external server by showing each hop along the way, including IP addresses and response times. After connecting to a VPN, the routing path may change, and tracert can help identify where the connection fails (e.g., at the VPN gateway or beyond). This is critical for determining if the issue is due to a network blockage, routing misconfiguration, or VPN tunnel failure.
F. route print:
This command (or route on Unix-based systems) displays the local routing table, showing how the system directs traffic to different networks, including the VPN. After a VPN connection, the routing table may be modified to route traffic through the VPN tunnel. Checking route print helps identify if the external server’s IP address is being routed correctly or if there’s a conflict (e.g., split tunneling misconfiguration) preventing access.
Why Not the Other Options?
A. nslookup:
This command queries DNS servers to resolve domain names to IP addresses. While it could check if the external server’s hostname resolves correctly, it doesn’t address connectivity or routing issues, which are more likely the cause of the problem after a VPN connection.
B. tcpdump:
This is a packet capture tool used to analyze network traffic at a detailed level. While useful for advanced troubleshooting, it requires significant expertise and is less commonly used as an initial diagnostic tool compared to tracert or route print for this scenario.
C. arp:
The Address Resolution Protocol (ARP) command displays or modifies the ARP cache, which maps IP addresses to MAC addresses on the local network. It is irrelevant for troubleshooting access to an external server over a VPN, as the issue is beyond the local subnet.
D. dig:
Similar to nslookup, dig is a DNS lookup tool used to query DNS records. It’s useful for verifying DNS resolution but doesn’t help diagnose routing or connectivity issues to the external server.
Why These Two?
After connecting to a VPN, the system’s routing table is often updated to direct traffic through the VPN tunnel. If the external server is not reachable, route print can reveal whether the traffic is being misrouted or if the VPN has overridden the default gateway incorrectly. tracert complements this by showing the actual path taken, helping pinpoint where the connection drops (e.g., at the VPN endpoint or an intermediate hop).
This combination is practical and aligns with standard troubleshooting steps for VPN-related connectivity issues, such as verifying routing and tracing the network path.
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.2 – "Given a scenario, troubleshoot common network connectivity issues." This includes using tools like tracert and route to diagnose routing and connectivity problems.
Microsoft Documentation:
Describes tracert and route print as key commands for troubleshooting network and routing issues in Windows environments.
Cisco Networking Academy:
Highlights the use of traceroute and route table analysis for diagnosing VPN and external connectivity problems.
A research facility is expecting to see an exponential increase in global network traffic in the near future. The offices are equipped with 2.5Gbps fiber connections from the ISP, but the facility is currently only utilizing 1Gbps connections. Which of the following would need to be configured in order to use the ISP's connection speed?
A. 802.1Q tagging
B. Network address translation
C. Port duplex
D. Link aggregation
Explanation:
Port duplex settings must be configured to match the ISP's connection speed (2.5Gbps).
Issue: The facility’s current 1Gbps connections suggest auto-negotiation mismatches or half-duplex settings, limiting throughput.
Solution: Ensure ports are set to full-duplex and 2.5Gbps-capable (e.g., 2.5GBASE-T).
Why Not the Other Options?
A) 802.1Q tagging
Incorrect: This is for VLAN trunking, not speed/duplex configuration.
B) Network address translation (NAT)
Incorrect: NAT translates IP addresses but doesn’t affect physical link speed.
D) Link aggregation
Incorrect: Aggregating 1Gbps links (e.g., LACP) could increase bandwidth but doesn’t address the 2.5Gbps ISP link.
Reference:
CompTIA Network+ Objective 2.1 (Ethernet Standards)
IEEE 802.3bz (2.5G/5GBASE-T)
A customer calls the help desk to report issues connection to the internet. The customer
can reach a local database server. A technician goes to the site and examines the
configuration: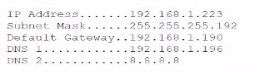
Which of the following is causing the user's issue?
A. Incorrect DNS
B. Unreachable gateway
C. Failed root bridge
D. Poor upstream routing
Explanation:
Scenario Analysis:
The customer can access a local database server, indicating that the local network (e.g., LAN) is operational, and the device’s IP configuration (IP address, subnet mask) is likely correct for the local subnet. However, the inability to connect to the internet suggests an issue with reaching external networks, which typically involves the default gateway (the router or device responsible for forwarding traffic outside the local network).
Why B.
Unreachable gateway?
The default gateway is the device that routes traffic from the local network to the internet or other external networks. If the gateway is unreachable (e.g., due to a misconfigured IP address, the gateway being down, or a connectivity issue between the user’s device and the gateway), the user will be unable to access the internet while still reaching local resources like the database server.
Common causes include:
The default gateway IP address in the user’s configuration is incorrect or points to a non-existent device.
The gateway device (e.g., router) is offline or has a failed interface.
A physical or logical disconnection (e.g., a cable issue or VLAN misconfiguration) prevents communication with the gateway.
The technician examining the configuration would likely check the user’s IP settings (e.g., using ipconfig or ifconfig) and ping the gateway to confirm reachability.
Why Not the Other Options?
A. Incorrect DNS:
If the DNS settings were incorrect, the user might struggle to resolve domain names (e.g., www.google.com) but could still access the internet using IP addresses directly. Since the user can’t connect to the internet at all, and the local database server (likely accessed by IP or local hostname) works, DNS is unlikely the primary issue. However, DNS could be a secondary concern if the technician finds it misconfigured during the investigation.
C. Failed root bridge:
This term is more relevant to wireless networks using Spanning Tree Protocol (STP) or wireless mesh networks, where a root bridge is a central access point. A failed root bridge would typically disrupt local wireless connectivity, but the user can still reach the local database server, suggesting the local network (including wireless, if applicable) is functional. This option is less likely unless the network heavily relies on a specific root bridge for internet access, which is uncommon.
D. Poor upstream routing:
Poor upstream routing (e.g., issues beyond the gateway, such as with the ISP or intermediate routers) would typically affect all users or require external confirmation (e.g., from the ISP). Since the technician is examining the local configuration and the issue is specific to this user, the problem is more likely local (e.g., unreachable gateway) rather than an upstream routing issue.
Troubleshooting Steps the Technician Might Take:
Verify the user’s IP configuration (e.g., ipconfig /all on Windows) to check the default gateway IP.
Ping the default gateway from the user’s device to test reachability.
Check the gateway device (e.g., router) status or interface connectivity.
If the gateway is reachable, use tracert or traceroute to see where the internet connection fails.
Assumption:
Since no specific configuration data (e.g., IP addresses, subnet masks) was provided, the conclusion is based on the symptom (local access works, internet fails), which points to a gateway issue as the most likely cause. If the configuration details (e.g., from an image) were available, they would confirm this (e.g., a mismatched gateway IP).
Reference:
CompTIA Network+ (N10-009) Exam Objectives:
Section 3.2 – "Given a scenario, troubleshoot common network connectivity issues." This includes diagnosing issues with the default gateway as a common cause of internet connectivity problems.
Microsoft Networking Documentation:
Highlights the default gateway as the critical link for internet access and how its unavailability prevents external connectivity.
Cisco Networking Basics:
Explains the role of the default gateway in routing traffic from a local network to external networks.
| Page 13 out of 43 Pages |
