Which of the following have data manipulation and procedural scripting power? (Choose two.)
A. PQL
B. PL/SQL
C. Advanced
D. SQL
E. SQL
F. T-SQL
F. T-SQL
A database administrator needs to provide access to data from two different tables to multiple group users in order to facilitate ongoing reporting. However, some columns in each table are restricted, and users should not be able to see the values in these columns. Which of the following is thebestaction for the administrator to take?
A. Create a stored procedure.
B. Create a view.
C. Create a csv export.
D. Create a trigger.
A database administrator wants to remove inactive customers from a database. Which of
the following statements should the administrator use?
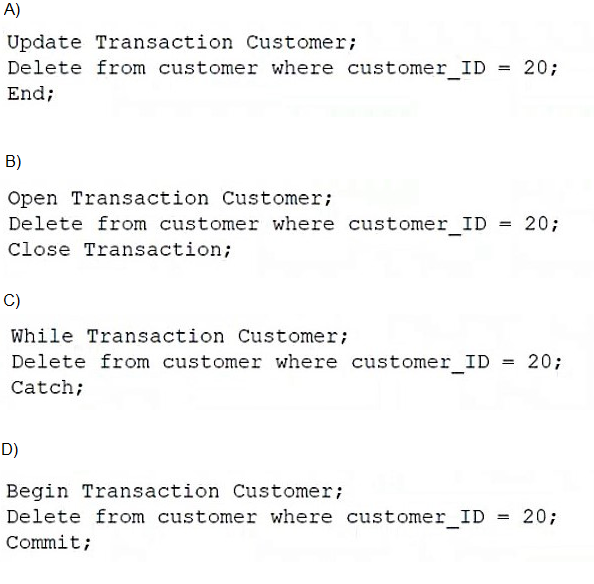
A. Option A
B. Option B
C. Option C
D. Option D
A database administrator would like to create a table named XYZ. Which of the following
queries should the database administrator use to create the table?
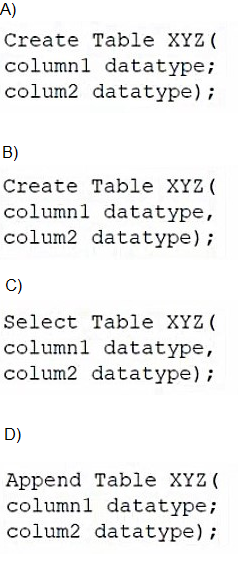
A. Option A
B. Option B
C. Option C
D. Option D
Which of the following cloud delivery models provides users with thehighestlevel of flexibility regarding resource provisioning and administration?
A. DBaaS
B. IaaS
C. SaaS
D. PaaS
Which of the following statements contains an error?
A. Select EmpId from employee where EmpId=90030
B. Select EmpId where EmpId=90030 and DeptId=34
C. Select* from employee where EmpId=90030
D. Select EmpId from employee
Which of the following is used to write SQL queries in various programming languages?
A. Indexing
B. Object-relational mapping
C. Excel
D. Normalization
Which of the following is a result of an on-path attack on a system?
A. A Wi-Fi networkthat redirects to clones of legitimate websites
B. A website that has crashed and is no longer accessible
C. An email from an unknown source requesting bank account details
D. A web application that returns the addresses of its customers
Which of the following ismostlikely to prevent tampering with server hardware that houses data?
A. Biometric locks
B. Strong password policy
C. Network firewall
D. Surveillance cameras
A database's daily backup failed. Previous backups were completed successfully. Which of the following should the database administrator examinefirstto troubleshoot the issue?
A. CPU usage
B. Disk space
C. Event log
D. OS performance
| Page 2 out of 8 Pages |
