Topic 3: Exam Pool C
A security analyst needs to determine how an attacker was able to use User3 to gain a
foothold within a company's network. The company's lockout policy requires that an
account be locked out for a minimum of 15 minutes after three unsuccessful attempts.
While reviewing the log files, the analyst discovers the following:
Which of the following attacks MOST likely occurred?
A. Dictionary
B. Credential-stuffing
C. Password-spraying
D. Brute-force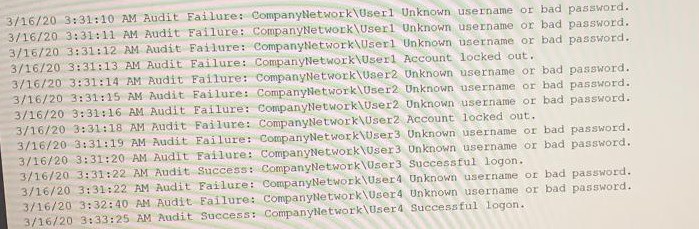
Which of the following attacks MOST likely occurred?
A.
Dictionary
B.
Credential-stuffing
C.
Password-spraying
D.
Brute-force
Brute-force
Which of the following relets to applications and systems that are used within an
organization without consent or approval?
A.
Shadow IT
B.
ONT
C.
Dark web
D.
Insider threats
Shadow IT
A Chief Executive Officer's (CEO) personal information was stolen in a social engineering attack. Which of the following sources would reveal if the CEO's personal information is for sale?
A.
Automated information sharing
B.
Open-source intelligence
C.
The dark web
D.
Vulnerability databases
The dark web
A security administrator currently spends a large amount of time on common security tasks, such aa report generation, phishing investigations, and user provisioning and
deprovisioning This prevents the administrator from spending time on other security
projects. The business does not have the budget to add more staff members. Which of the
following should the administrator implement?
A.
A. DAC
B.
B. ABAC
C.
C. SCAP
D.
SOAR
SOAR
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site Upon investigation, a security analyst the identifies the following:
• The legitimate websites IP address is 10.1.1.20 and eRecruit local resolves to the IP
• The forged website's IP address appears to be 10.2.12.99. based on NetFtow records
• AH three at the organization's DNS servers show the website correctly resolves to the
legitimate IP
• DNS query logs show one of the three DNS servers returned a result of 10.2.12.99
(cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
A.
A reverse proxy was used to redirect network traffic
B.
An SSL strip MITM attack was performed
C.
An attacker temporarily pawned a name server
D.
An ARP poisoning attack was successfully executed
An SSL strip MITM attack was performed
Which of the following scenarios BEST describes a risk reduction technique?
A.
A security control objective cannot be met through a technical change, so the company
purchases insurance and is no longer concerned about losses from data breaches.
B.
A security control objective cannot be met through a technical change, so the company
implements a policy to train users on a more secure method of operation
C.
A security control objective cannot be met through a technical change, so the company
changes as method of operation
D.
A security control objective cannot be met through a technical change, so the Chief
Information Officer (CIO) decides to sign off on the risk.
A security control objective cannot be met through a technical change, so the company
implements a policy to train users on a more secure method of operation
An organization with a low tolerance for user inconvenience wants to protect laptop hard drives against loss or data theft. Which of the following would be the MOST acceptable?
A.
SED
B.
HSM
C.
DLP
D.
TPM
SED
A vulnerability assessment report will include the CVSS score of the discovered
vulnerabilities because the score allows the organization to better.
A.
validate the vulnerability exists in the organization's network through penetration testing
B.
research the appropriate mitigation techniques in a vulnerability database
C.
find the software patches that are required to mitigate a vulnerability
D.
prioritize remediation of vulnerabilities based on the possible impact.
prioritize remediation of vulnerabilities based on the possible impact.
The Chief Executive Officer (CEO) of an organization would like staff members to have the flexibility to work from home anytime during business hours, incident during a pandemic or crisis, However, the CEO is concerned that some staff members may take advantage of the of the flexibility and work from high-risk countries while on holidays work to a third-party organization in another country. The Chief information Officer (CIO) believes the company can implement some basic to mitigate the majority of the risk. Which of the following would be BEST to mitigate CEO’s concern? (Select TWO).
A.
Geolocation
B.
Time-of-day restrictions
C.
Certificates
D.
Tokens
E.
Geotagging
F.
Role-based access controls
Geolocation
E.
Geotagging
A security analyst reviews the datacenter access logs for a fingerprint scanner and notices
an abundance of errors that correlate with users' reports of issues accessing the facility.
Which of the following MOST likely the cause of the cause of the access issues?
A.
False rejection
B.
Cross-over error rate
C.
Efficacy rale
D.
Attestation
Cross-over error rate
| Page 5 out of 89 Pages |
| SY0-601 Practice Test | Previous |
