CompTIA SY0-601 Practice Test
Prepare smarter and boost your chances of success with our CompTIA SY0-601 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use SY0-601 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA SY0-601 certified.
18860 already prepared
Updated On : 13-Jan-2026886 Questions
CompTIA Security+ Exam 2021
4.8/5.0
Topic 3: Exam Pool C
An incident response technician collected a mobile device during an investigation. Which of the following should the technician do to maintain chain of custody?
A.
Document the collection and require a sign-off when possession changes.
B.
Lock the device in a safe or other secure location to prevent theft or alteration.
C.
Place the device in a Faraday cage to prevent corruption of the data.
D.
Record the collection in a blockchain-protected public ledger
Document the collection and require a sign-off when possession changes.
An organization that is located in a flood zone is MOST likely to document the concerns associated with the restoration of IT operation in a:
A.
business continuity plan
B.
communications plan.
C.
disaster recovery plan.
D.
continuity of operations plan
disaster recovery plan.
A security analyst is reviewing the output of a web server log and notices a particular
account is attempting to transfer large amounts of money: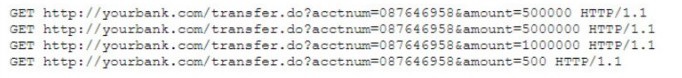
Which of the following types of attack is MOST likely being conducted?
A.
SQLi
B.
CSRF
C.
Session replay
D.
API
CSRF
Which of the following is the BEST reason to maintain a functional and effective asset management policy that aids in ensuring the security of an organization?
A.
To provide data to quantity risk based on the organization's systems.
B.
To keep all software and hardware fully patched for known vulnerabilities
C.
To only allow approved, organization-owned devices onto the business network
D.
To standardize by selecting one laptop model for all users in the organization
To provide data to quantity risk based on the organization's systems.
An effective asset management policy helps an organization understand and manage the systems, hardware, and software it uses, and how they are used, including their
vulnerabilities and risks. This information is crucial for accurately identifying and assessing
risks to the organization, and making informed decisions about how to mitigate those risks.
This is the best reason to maintain an effective asset management policy.
Reference: CompTIA Security+ Study Guide (SY0-601) 7th Edition by Emmett Dulaney,
Chuck Easttom
Which of the following scenarios would make a DNS sinkhole effective in thwarting an attack?
A.
An attacker is sniffing traffic to port 53, and the server is managed using unencrypted usernames and passwords
B.
An organization is experiencing excessive traffic on port 53 and suspects an attacker is
trying to DoS the domain name server.
C.
Malware trying to resolve an unregistered domain name to determine if it is running in an
isolated sandbox
D.
Routing tables have been compromised, and an attacker is rerouting traffic to malicious
websites
An attacker is sniffing traffic to port 53, and the server is managed using unencrypted usernames and passwords
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly. Which of the following technologies should the IT manager use when implementing MFA?
A.
One-time passwords
B.
Email tokens
C.
CPush notifications
D.
Hardware authentication
CPush notifications
An attacker has successfully exfiltrated several non-salted password hashes from an online
system. Given the logs below:
Which of the following BEST describes the type of password attack the attacker is performing?
A.
Dictionary
B.
Pass-the-hash
C.
Brute-force
D.
Password spraying
Dictionary
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log: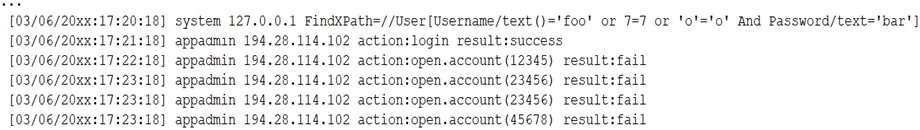
Which of the following can the security analyst conclude?
A.
A replay attack is being conducted against the application.
B.
An injection attack is being conducted against a user authentication system.
C.
A service account password may have been changed, resulting in continuous failed logins within the application.
D.
A credentialed vulnerability scanner attack is testing several CVEs against the
application
A service account password may have been changed, resulting in continuous failed logins within the application.
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
A.
Nmap
B.
Wireshark
C.
Autopsy
D.
DNSEnum
DNSEnum
Which of the following describes the ability of code to target a hypervisor from inside
A.
Fog computing
B.
VM escape
C.
Software-defined networking
D.
Image forgery
E.
Container breakout
VM escape
| Page 1 out of 89 Pages |
