Topic 3: Exam Pool C
A security analyst is investigating an incident to determine what an attacker was able to do
on a compromised laptop. The analyst reviews the following SIEM log: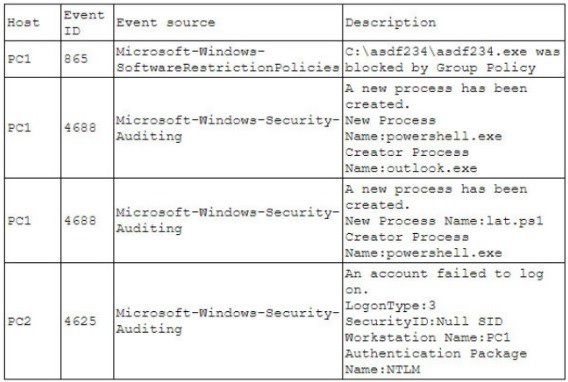
Which of the following describes the method that was used to compromise the laptop?
A.
An attacker was able to move laterally from PC1 to PC2 using a pass-the-hash attack
B.
An attacker was able to bypass application whitelisting by emailing a spreadsheet
attachment with an embedded PowerShell in the file
C.
An attacker was able to install malware to the CAasdf234 folder and use it to gam administrator nights and launch Outlook
D.
An attacker was able to phish user credentials successfully from an Outlook user profile
An attacker was able to move laterally from PC1 to PC2 using a pass-the-hash attack
A security analyst has received an alert about being sent via email. The analyst’s Chief information Security Officer (CISO) has made it clear that PII must be handle with extreme care From which of the following did the alert MOST likely originate?
A.
S/MIME
B.
DLP
C.
IMAP
D.
HIDS
DLP
Explanation: Network-based DLP monitors outgoing data looking for sensitive data. Network-based DLP systems monitor outgoing email to detect and block unauthorized data transfers and monitor data stored in the cloud.
A pharmaceutical sales representative logs on to a laptop and connects to the public WiFi to check emails and update reports. Which of the following would be BEST to prevent other devices on the network from directly accessing the laptop? (Choose two.)
A.
Trusted Platform Module
B.
Ahost-based firewall
C.
A DLP solution
D.
Full disk encryption
E.
A VPN
F.
Antivirus software
Trusted Platform Module
B.
Ahost-based firewall
Which of the following technical controls is BEST suited for the detection and prevention of buffer overflows on hosts?
A.
DLP
B.
HIDS
C.
EDR
D.
NIPS
EDR
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst http://selfexamtraining.com/uploadimages/SY0-601-Q-39.jpgMOST likely seeing?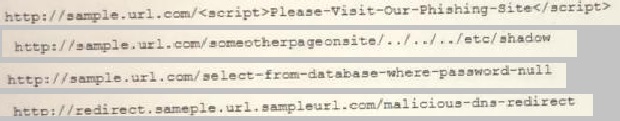
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option B
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be BEST to help the organization’s executives determine the next course of action?
A.
An incident response plan
B.
A communications plan
C.
A disaster recovery plan
D.
A business continuity plan
A business continuity plan
Joe, a user at a company, clicked an email link led to a website that infected his
workstation. Joe, was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and It has continues to evade detection. Which of the following should administrator implement to protect the environment from this malware?
A.
Install a definition-based antivirus.
B.
Implement an IDS/IPS
C.
Implement a heuristic behavior-detection solution.
D.
Implement CASB to protect the network shares.
Implement a heuristic behavior-detection solution.
A Chief Security Office's (CSO's) key priorities are to improve preparation, response, and recovery practices to minimize system downtime and enhance organizational resilience to ransomware attacks. Which of the following would BEST meet the CSO's objectives?
A.
Use email-filtering software and centralized account management, patch high-risk
systems, and restrict administration privileges on fileshares.
B.
Purchase cyber insurance from a reputable provider to reduce expenses during an incident.
C.
Invest in end-user awareness training to change the long-term culture and behavior of
staff and executives, reducing the organization's susceptibility to phishing attacks.
D.
Implement application whitelisting and centralized event-log management, and perform
regular testing and validation of full backups.
Implement application whitelisting and centralized event-log management, and perform
regular testing and validation of full backups.
A cybersecurity manager has scheduled biannual meetings with the IT team and
department leaders to discuss how they would respond to hypothetical cyberattacks. During these meetings, the manager presents a scenario and injects additional information throughout the session to replicate what might occur in a dynamic cybersecurity event involving the company, its facilities, its data, and its staff. Which of the following describes what the manager is doing?
A.
Dveloping an incident response plan
B.
Building a disaster recovery plan
C.
Conducting a tabletop exercise
D.
Running a simulation exercise
Conducting a tabletop exercise
A security analyst is logged into a Windows file server and needs to see who is accessing
files and from which computers Which of the following tools should the analyst use?
A.
netstt
B.
net share
C.
netcat
D.
nbtstat
E.
net session
netstt
| Page 4 out of 89 Pages |
| SY0-601 Practice Test | Previous |
