Topic 4: Exam Pool D (NEW)
An organization plans to transition the intrusion detection and prevention techniques on a critical subnet to an anomaly-based system. Which of the following does the organization need to determine for this to be successful?
A.
The baseline
B.
The endpoint configurations
C.
The adversary behavior profiles
D.
The IPS signatures
The adversary behavior profiles
A security administrator is setting up a SIEM to help monitor for notable events across the
enterprise. Which of the following control types does this BEST represent?
A.
Preventive
B.
Compensating
C.
Corrective
D.
Detective
Detective
The following are the logs of a successful attack.
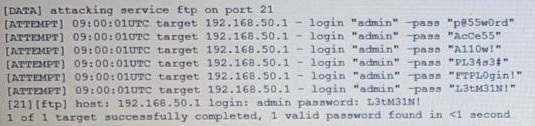
Which of the following controls would be BEST to use to prevent such a breach in the future?
A.
Password history
B.
Account expiration
C.
Password complexity
D.
Account lockout
Account lockout
A web server administrator has redundant servers and needs to ensure failover to the secondary server when the primary server goes down. Which of the following should the administrator implement to avoid disruption?
A.
NIC teaming
B.
High availability
C.
Dual power supply
D.
laaS
High availability
The lessons-learned analysis from a recent incident reveals that an administrative office
worker received a call from someone claiming to be from technical support. The caller
convinced the office worker to visit a website, and then download and install a program
masquerading as an antivirus package. The program was actually a backdoor that an
attacker could later use to remote control the worker's PC. Which of the following would be
BEST to help prevent this type of attack in the future?
A.
Data loss prevention
B.
Segmentation
C.
Application whitelisting
D.
Quarantine
Application whitelisting
An organization recently recovered from a data breach. During the root cause analysis, the
organization determined the source of the breach to be a personal cell phone that had
been reported lost. Which of the following
solutions should the organization implement to reduce the likelihood of future data
breaches?
A.
MDM
B.
MAM
C.
VDI
D.
DLP
MDM
Which of the following often operates in a client-server architecture to act as a service
repository. providing enterprise consumers access to structured threat intelligence data?
A.
STIX
B.
CIRT
C.
OSINT
D.
TAXII
CIRT
A external forensics investigator has been hired to investigate a data breach at a large enterprise with numerous assets. It is known that the breach started in the DMZ and moved to the sensitive information, generating multiple logs as the attacker traversed through the network. Which of the following will BEST assist with this investigation?
A.
Perform a vulnerability scan to identity the weak spots
B.
Use a packet analyzer to Investigate the NetFlow traffic
C.
Check the SIEM to review the correlated logs
D.
Require access to the routers to view current sessions
Check the SIEM to review the correlated logs
Which of the following would a European company interested in implementing a technical,
hands-on set of security standards MOST likely choose?
A.
GOPR
B.
CIS controls
C.
ISO 27001
D.
ISO 37000
GOPR
A user downloaded an extension for a browser, and the uses device later became infected.
The analyst who is investigating the incident saw various logs where the attacker was
hiding activity by deleting data The following was observed running:

Which of the following is the malware using to execute the attack?
A.
PowerShell
B.
Python
C.
Bash
D.
Macros
Macros
| Page 34 out of 89 Pages |
| SY0-601 Practice Test | Previous |
