Topic 4: Exam Pool D (NEW)
A security analyst is reviewing the following command-line output:
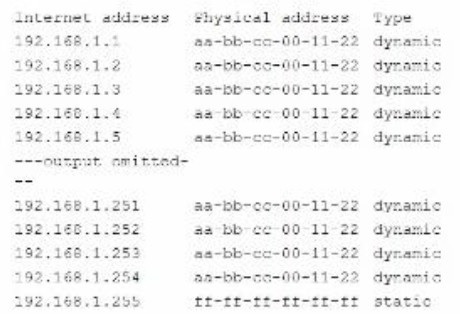
Which of the following Is the analyst observing?
A.
IGMP spoofing
B.
URL redirection
C.
MAC address cloning
D.
DNS poisoning
MAC address cloning
A Chief Security Officer (CSO) is concerned about the volume and integrity of sensitive information that is exchanged between the organization and a third party through email.
The CSO is particularly concerned about an unauthorized party who is intercepting information that is in transit between the two organizations. Which of the following would address the CSO's concerns?
A.
SPF
B.
DMARC
C.
SSL
D.
DKIM
E.
TLS
TLS
A SOC is implementing an in sider-threat-detection program. The primary concern is that
users may be accessing confidential data without authorization. Which of the following
should be deployed to detect a potential insider threat?
A.
A honeyfile
B.
ADMZ
C.
DLP
D.
File integrity monitoring
A honeyfile
An organization is having difficulty correlating events from its individual AV. EDR. DLP. SWG. WAF. MOM. HIPS, and CASB systems. Which of the following is the BEST way to improve the situation?
A.
Remove expensive systems that generate few alerts.
B.
Modify the systems to alert only on critical issues
C.
Utilize a SIEM to centralize togs and dashboards
D.
Implement a new syslog/NetFlow appliance
Modify the systems to alert only on critical issues
An organization's corporate offices were destroyed due to a natural disaster, so the
organization is now setting up offices in a temporary work space. Which of the following will
the organization MOST likely consult?
A.
The business continuity plan
B.
The disaster recovery plan
C.
The communications plan
D.
The incident response plan
The business continuity plan
A security assessment found that several embedded systems are running unsecure protocols. These Systems were purchased two years ago and the company that developed them is no longer in business Which of the following constraints BEST describes the reason the findings cannot be remediated?
A.
inability to authenticate
B.
Implied trust
C.
Lack of computing power
D.
Unavailable patch
Unavailable patch
A company is required to continue using legacy software to support a critical service.
Which of the following BEST explains a risk of this practice?
A.
Default system configuration
B.
Unsecure protocols
C.
Lack of vendor support
D.
Weak encryption
Lack of vendor support
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
- WAP
- DHCP Server
- AAA Server
- Wireless Controller
- LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.
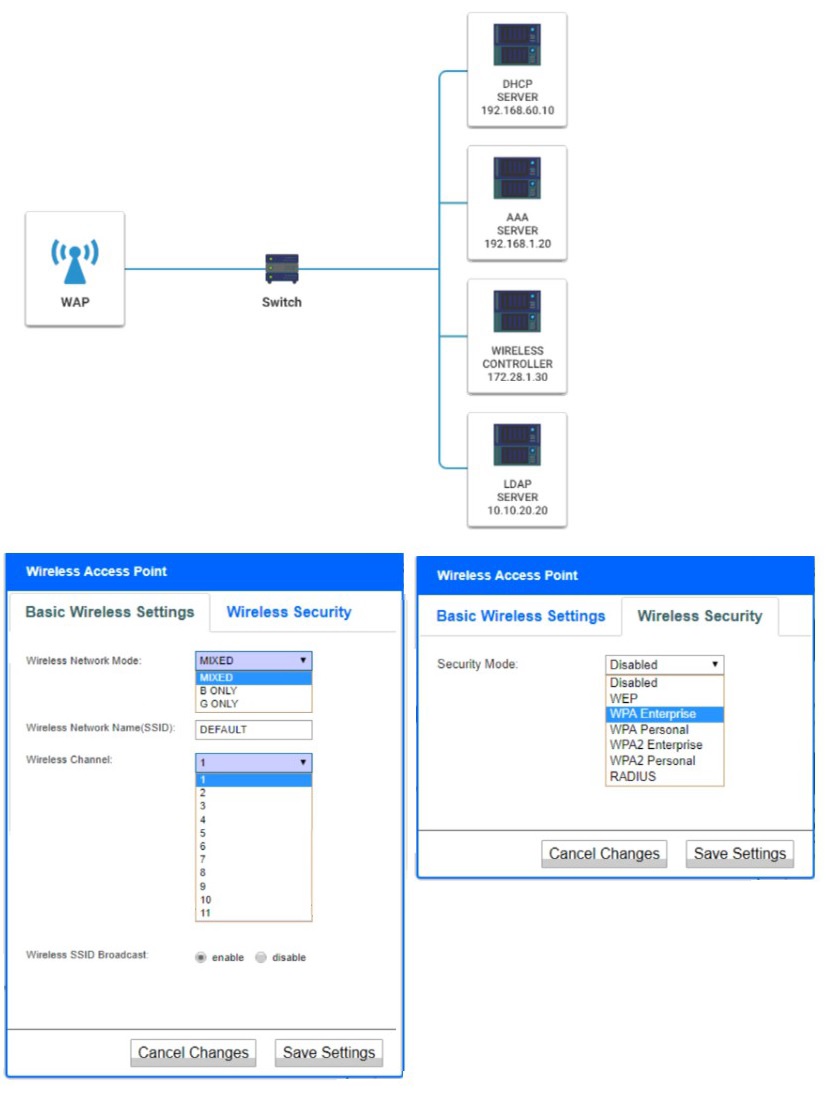
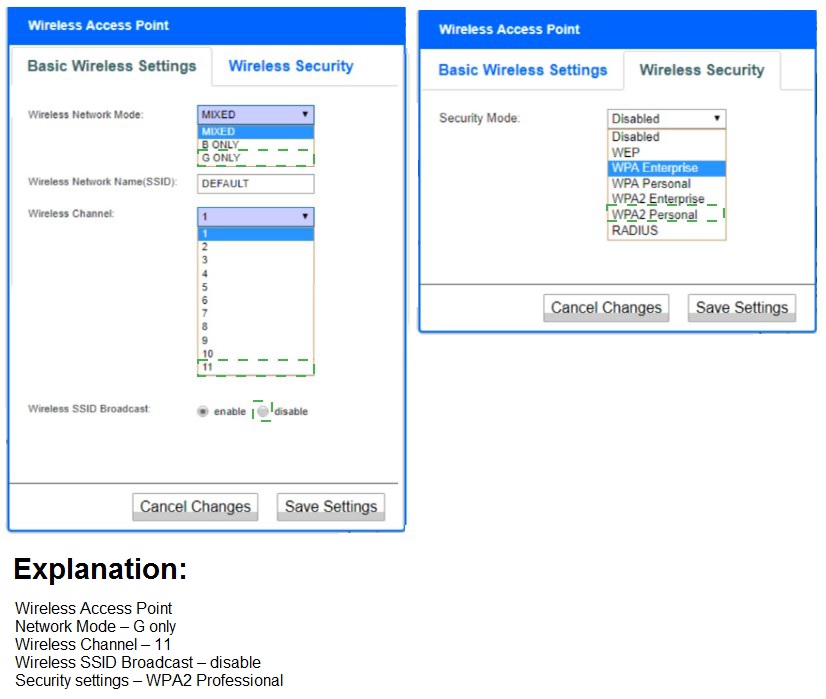
An organization regularly scans its infrastructure for missing security patches but is
concerned about hackers gaining access to the scanner's account. Which of the following
would be BEST to minimize this risk?
A.
Require a complex, eight-character password that is updated every 90 days.
B.
Perform only non-intrusive scans of workstations.
C.
Use non-credentialed scans against high-risk servers.
D.
Log and alert on unusual scanner account logon times.
Log and alert on unusual scanner account logon times.
Which of the following is the correct order of volatility from MOST to LEAST volatile?
A.
Memory, temporary filesystems, routing tables, disk, network storage
B.
Cache, memory, temporary filesystems, disk, archival media
C.
Memory, disk, temporary filesystems, cache, archival media
D.
Cache, disk, temporary filesystems, network storage, archival media
Cache, memory, temporary filesystems, disk, archival media
| Page 33 out of 89 Pages |
| SY0-601 Practice Test | Previous |
