Topic 5: Exam Pool E (NEW)
An organization would like to remediate the risk associated with its cloud service provider not meeting its advertised 99.999% availability metrics. Which of the following should the
organization consult for the exact requirements for the cloud provider?
A.
SLA
B.
BPA
C.
NDA
D.
MOU
SLA
An organization recently acquired an ISO 27001 certification. Which of the following would
MOST likely be considered a benefit of this certification?
A.
It allows for the sharing of digital forensics data across organizations
B.
It provides insurance in case of a data breach
C.
It provides complimentary training and certification resources to IT security staff.
D.
It certifies the organization can work with foreign entities that require a security
clearance
E.
It assures customers that the organization meets security standards
It assures customers that the organization meets security standards
Joe. a security analyst, recently performed a network discovery to fully understand his
organization's electronic footprint from a "public" perspective. Joe ran a set of commands
and received the following output:
Which of the following can be determined about the organization's public presence and
security posture? (Select TWO).
A.
Joe used Who is to produce this output.
B.
Joe used cURL to produce this output.
C.
Joe used Wireshark to produce this output
D.
The organization has adequate information available in public registration.
E.
The organization has too much information available in public registration.
F.
The organization has too little information available in public registration.
Joe used Who is to produce this output.
D.
The organization has adequate information available in public registration.
An engineer is setting up a VDI environment for a factory location, and the business wants to deploy a low-cost solution to enable users on the shop floor to log in to the VDI environment directly. Which of the following should the
engineer select to meet these requirements?
A.
Laptops
B.
Containers
C.
Thin clients
D.
Workstations
Thin clients
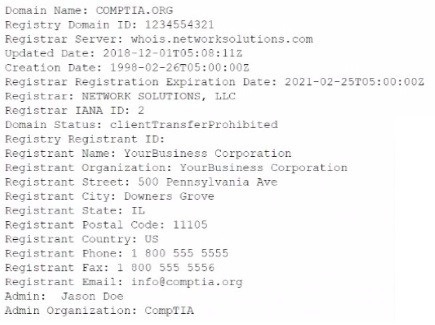
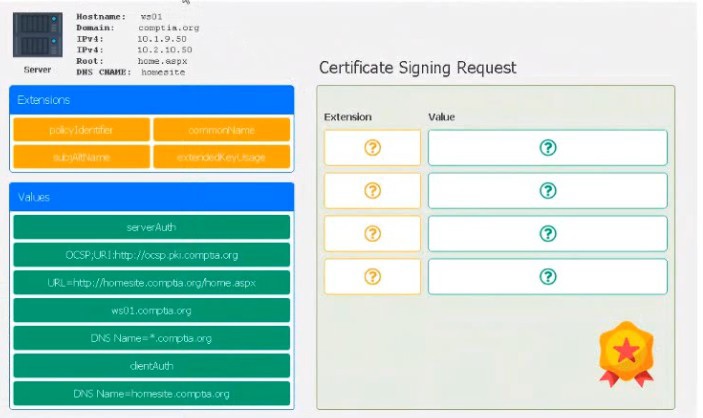
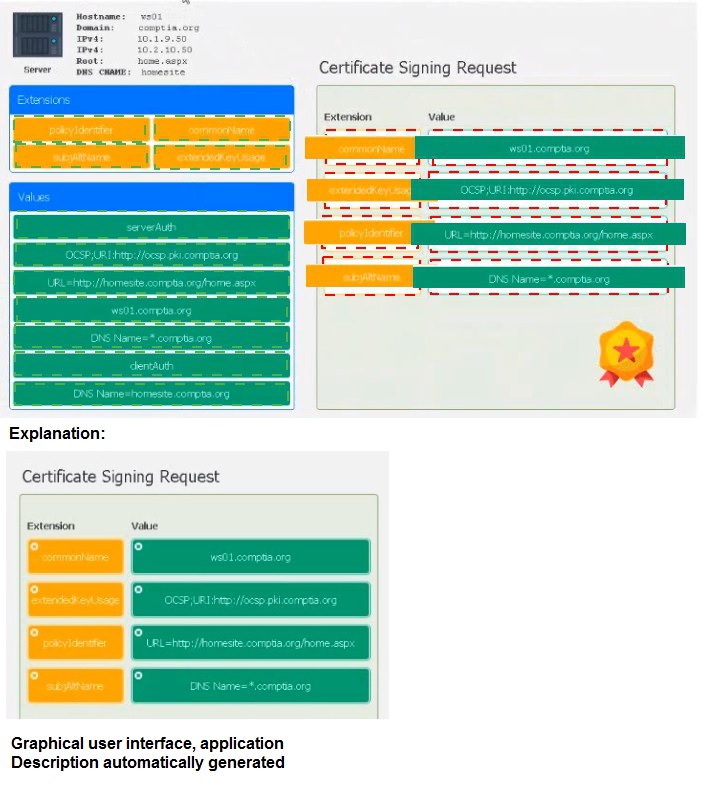
Leveraging the information supplied below, complete the CSR for the server to set up TLS
(HTTPS)
• Hostname: ws01
• Domain: comptia.org
• IPv4: 10.1.9.50
• IPV4: 10.2.10.50
• Root: home.aspx
• DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria
belong in the let hand column and values belong in the corresponding row in the right hand column.
A company just implemented a new telework policy that allows employees to use personal
devices for official email and file sharing while working from home. Some of the
requirements are:
* Employees must provide an alternate work location (i.e., a home address)
* Employees must install software on the device that will prevent the loss of proprietary
data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
A.
Geofencing, content management, remote wipe, containerization, and storage
segmentation
B.
Content management, remote wipe, geolocation, context-aware authentication, and
containerization
C.
Application management, remote wipe, geofencing, context-aware authentication, and
containerization
D.
Remote wipe, geolocation, screen locks, storage segmentation, and full-device
encryption
Remote wipe, geolocation, screen locks, storage segmentation, and full-device
encryption
A security analyst has been reading about a newly discovered cyber attack from a known threat actor. Which of the following would BEST support the analyst's review of the tactics, techniques, and protocols the threat actor was observed using in previous campaigns?
A.
Security research publications
B.
The MITRE ATT&CK framework
C.
The Diamond Model of Intrusion Analysis
D.
The Cyber Kill Chain
The MITRE ATT&CK framework
Entering a secure area requires passing through two doors, both of which require someone
who is already inside to initiate access. Which of the following types of physical security
controls does this describe?
A.
Cameras
B.
Faraday cage
C.
Access control vestibule
D.
Sensors
E.
Guards
Access control vestibule
Developers are writing code and merging it into shared repositories several times a day,
where it is tested automatically. Which of the following concepts does this BEST represent?
A.
Functional testing
B.
Stored procedures
C.
Elasticity
D.
Continuous integration
Elasticity
A bank detects fraudulent activity on user's account. The user confirms transactions completed yesterday on the bank's website at https://www.company.com. A security
analyst then examines the user's
Internet usage logs and observes the following output:
date; username; url;destinationport; responsecode
2020-03-01; userann; http: //www.company.org/;80;302
2020-03-01; userann: http: //www.company.org/secure_login/;80;200
2020-03-01; userann:http: //www.company.org/dashboard/;80;200
Which of the following has MOST likely occurred?
A.
Replay attack
B.
SQL injection
C.
SSL stripping
D.
Race conditions
Replay attack
| Page 32 out of 89 Pages |
| SY0-601 Practice Test | Previous |
