Topic 4: Exam Pool D (NEW)
A Chief Security Officer (CSO) was notified that a customer was able to access confidential
internal company files on a commonly used file-sharing service. The
file-sharing service is the same one used by company staff as one of its approved thirdparty
applications. After further investigation, the security team
determines the sharing of confidential files was accidental and not malicious. However, the
CSO wants to implement changes to minimize this type of incident
from reoccurring but does not want to impact existing business processes. Which of the
following would BEST meet the CSO's objectives?
A.
DLP
B.
SWG
C.
CASB
D.
Virtual network segmentation
E.
Container security
DLP
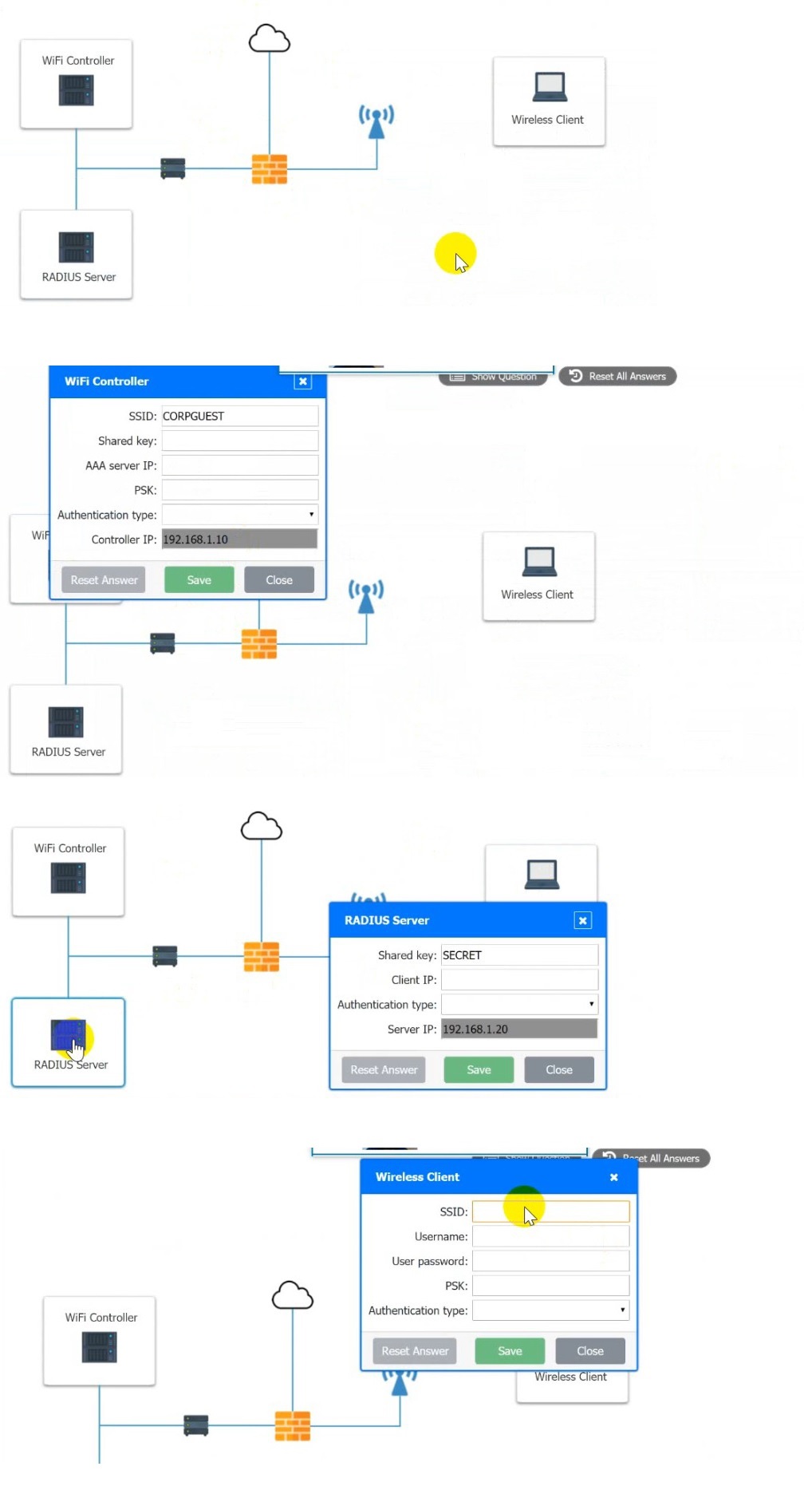
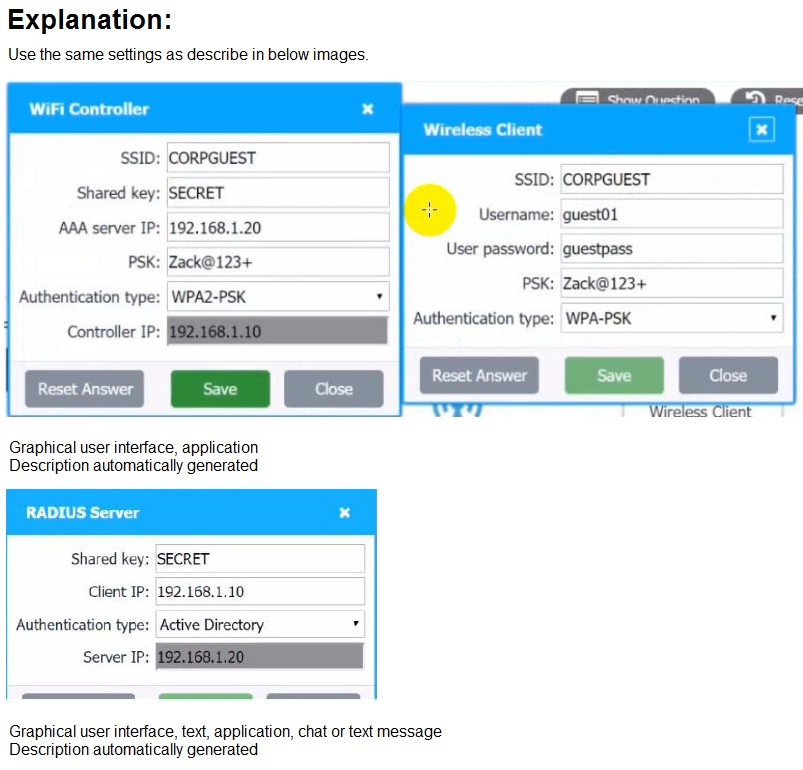
A systems administrator needs to install a new wireless network for authenticated guest
access. The wireless network should support 802. IX using the most secure encryption and
protocol available.
Perform the following slops:
1. Configure the RADIUS server.
2. Configure the WiFi controller.
3. Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01
Password: guestpass
A security researching is tracking an adversary by noting its attack and techniques based
on its capabilities, infrastructure, and victims. Which of the following is the researcher
MOST likely using?
A.
The Diamond Model of intrusion Analysis
B.
The Cyber Kill Chain\
C.
The MITRE CVE database
D.
The incident response process
The Diamond Model of intrusion Analysis
While reviewing pcap data, a network security analyst is able to locate plaintext usernames
and passwords being sent from workstations to network witches. Which of the following is
the security analyst MOST likely observing?
A.
SNMP traps
B.
A Telnet session
C.
An SSH connection
D.
SFTP traffic
A Telnet session
A network manager is concerned that business may be negatively impacted if the firewall in
its datacenter goes offline. The manager would like to Implement a high availability pair to:
A.
decrease the mean ne between failures
B.
remove the single point of failure
C.
cut down the mean tine to repair
D.
reduce the recovery time objective
remove the single point of failure
The security team received a report of copyright infringement from the IP space of lire corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted files. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again. Which of the following is MOST capable of accomplishing both tasks?
A.
HIDS
B.
Allow list
C.
TPM
D.
NGFW
TPM
A company Is concerned about is security after a red-team exercise. The report shows the team was able to reach the critical servers due to the SMB being exposed to the Internet and running NTLMV1, Which of the following BEST explains the findings?
A.
Default settings on the servers
B.
Unsecured administrator accounts
C.
Open ports and services
D.
Weak Data encryption
Open ports and services
A Chief Security Officer (CSO) has asked a technician to devise a solution that can detect unauthorized execution privileges from the OS in both executable and data files, and can work in conjunction with proxies or UTM. Which of the following would BEST meet the CSO's requirements?
A.
Fuzzing
B.
Sandboxing
C.
Static code analysis
D.
Code review
Sandboxing
A security analyst is reviewing a penetration-testing report from a third-party contractor.
The penetration testers used the organization's new API to bypass a driver to perform
privilege escalation on the organization's web servers. Upon looking at the API, the security
analyst realizes the particular API call was to a legacy system running an outdated OS.
Which of the following is the MOST likely attack type?
A.
Request forgery
B.
Session replay
C.
DLL injection
D.
Shimming
Request forgery
A security analyst has received several reports of an issue on an internal web application.
Users stale they are having to provide their credential twice lo log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several loos the analyst decades to run some commands on the gateway and obtains the following output
Internet address

Which of the following BEST describes the attack the company is experiencing?
A.
MAC flooding
B.
URL redirection
C.
ARP poisoning
D.
DNS hijacking
ARP poisoning
| Page 31 out of 89 Pages |
| SY0-601 Practice Test | Previous |
