Topic 4: Exam Pool D (NEW)
Which of the following terms should be included in a contract to help a company monitor
the ongoing security maturity of a new vendor?
A.
A right-to-audit clause allowing for annual security audits
B.
Requirements for event logs to be kept for a minimum of 30 days
C.
Integration of threat intelligence in the company's AV
D.
A data-breach clause requiring disclosure of significant data loss
A right-to-audit clause allowing for annual security audits
A network administrator is concerned about users being exposed to malicious content
when accessing company cloud applications. The administrator wants to be able to block
access to sites based on
the AUP. The users must also be protected because many of them work from home or at
remote locations, providing on-site customer support. Which of the following should the
administrator employ to meet these criteria?
meet these criteria?
A.
Implement NAC.
B.
Implement an SWG.
C.
Implement a URL filter.
D.
Implement an MDM.
Implement an SWG.
A security researcher is attempting to gather data on the widespread use of a Zero-day
exploit. Which of the following will the researcher MOST likely use to capture this data?
A.
A DNS sinkhole
B.
A honeypot
C.
A vulnerability scan
D.
cvss
A honeypot
A company has discovered unauthorized devices are using its WiFi network, and it wants
to harden the access point to improve security. Which of the following configuration should
an analyst enable to improve security? (Select Two)
A.
RADIUS
B.
PEAP
C.
WPS
D.
WEP-TKIP
E.
SSL
F.
WPA2-PSK
WEP-TKIP
F.
WPA2-PSK
A SECURITY ANALYST NEEDS TO FIND REAL-TIME DATA ON THE LATEST
MALWARE AND loCs WHICH OF THE FOLLOWING BEST DESCRIBE THE SOLUTION
THE ANALYST SHOULD PERSUE?
A.
ADVISORIES AND BULLETINS
B.
THREAT FEEDS
C.
SECURITY NEWS ARTICLES
D.
PEER-REVIEWED CONTENT
THREAT FEEDS
A Chief Executive Officer (CEO) is dissatisfied with the level of service from the company's
new service provider. The service provider is preventing the CEO from sending email from
a work account to a personal account. Which of the following types of service providers is
being used?
A.
Telecommunications service provider
B.
Cloud service provider
C.
Master managed service provider
D.
Managed security service provider
Cloud service provider
When implementing automation with loT devices, which of the following should be
considered FIRST to keep the network secure?
A.
Z-Wave compatibility
B.
Network range
C.
Zigbee configuration
D.
Communication protocols
Communication protocols
An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls?
(Select TWO).
A.
ISO
B.
PCI DSS
C.
SOC
D.
GDPR
E.
CSA
F.
NIST
PCI DSS
D.
GDPR
A security engineer is installing a WAF to protect the company’s website from malicious
web requests over SSL. Which of the following is needed to meet the objective?
A.
A reverse proxy
B.
A decryption certificate
C.
A split-tunnel VPN
D.
Load-balanced servers
A reverse proxy
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:
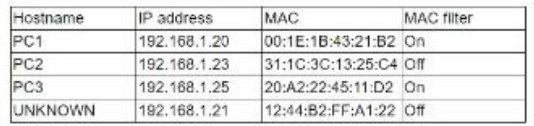
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
A.
Conduct a ping sweep
B.
Physically check each system
C.
Deny Internet access to the "UNKNOWN" hostname
D.
Apply MAC filtering
Apply MAC filtering
| Page 27 out of 89 Pages |
| SY0-601 Practice Test | Previous |
