Topic 5: Exam Pool E (NEW)
An analyst Is generating a security report for the management team. Security guidelines
recommend disabling all listening unencrypted services. Given this output from Nmap:
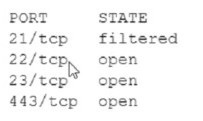
Which of the following should the analyst recommend to disable?
A.
21/tcp
B.
22/tcp
C.
23/tcp
D.
443/tcp
23/tcp
Which of the following would cause a Chief Information Security Officer (CISO) the MOST
concern regarding newly installed Internet-accessible 4K surveillance cameras?
A.
An inability to monitor 100%, of every facility could expose the company to unnecessary
risk.
B.
The cameras could be compromised if not patched in a timely manner.
C.
Physical security at the facility may not protect the cameras from theft.
D.
Exported videos may take up excessive space on the file servers.
An inability to monitor 100%, of every facility could expose the company to unnecessary
risk.
A desktop support technician recently installed a new document-scanning software program on a computer However, when the end user tried to launch the program, it did not
respond. Which of the following is MOST likely the cause?
A.
A new firewall rule is needed to access the application
B.
The system was quarantined for missing software updates
C.
The software was not added to the application whitelist
D.
The system was isolated from the network due to infected software
The software was not added to the application whitelist
A scurity analyst must enforce policies to harden an MDM infrastructure. The requirements are as follows:
* Ensure mobile devices can be tracked and wiped.
* Confirm mobile devices are encrypted.
Which of the following should the analyst enable on all the devices to meet these requirements?
A.
Geofencing
B.
Biometric authentication
C.
Geolocation
D.
Geotagging
Geofencing
Which of the following represents a biometric FRR?
A.
Authorized users being denied access
B.
Users failing to enter the correct PIN
C.
The denied and authorized numbers being equal
D.
The number of unauthorized users being granted access
Authorized users being denied access
Which of the following holds staff accountable while escorting unauthorized personnel?
A.
Locks
B.
Badges
C.
Cameras
D.
Visitor logs
Badges
A security analyst must determine if either SSH or Telnet is being used to log in to servers. Which of the following should the analyst use?
A.
logger
B.
Metasploit
C.
tcpdump
D.
netstat
netstat
An engineer needs to deploy a security measure to identify and prevent data tampering within the enterprise. Which of the following will accomplish this goal?
A.
Antivirus
B.
IPS
C.
FTP
D.
FIM
FIM
Data tampering prevention can include simple security measures such as the
encryption of data, and can include lengths such as using file integrity monitoring (FIM)
systems for better security.
https://www.cypressdatadefense.com/blog/data-tampering-prevention/
The SIEM at an organization has detected suspicious traffic coming a workstation in its
internal network. An analyst in the SOC the workstation and discovers malware that is
associated with a botnet is installed on the device A review of the logs on the workstation
reveals that the privileges of the local account were escalated to a local administrator. To
which of the following groups should the analyst report this real-world event?
A.
The NOC team
B.
The vulnerability management team
C.
The CIRT
D.
The read team
The CIRT
A recent security assessment revealed that an actor exploited a vulnerable workstation
within an organization and has persisted on the network for several months. The
organization realizes the need to reassess Its security.
Strategy for mitigating risks within the perimeter Which of the following solutions would
BEST support the organization's strategy?
A.
FIM
B.
DLP
C.
EDR
D.
UTM
FIM
Explanation: The best solution to support the organization's security strategy in this situation is File Integrity Monitoring (FIM). FIM is a technique used to detect and monitor unauthorized changes to critical files and system configurations on a computer or network. It is used to detect malicious activity such as malware, unauthorized modifications, and malicious user activity. FIM can also be used to detect and monitor compliance with security policies and procedures.
| Page 26 out of 89 Pages |
| SY0-601 Practice Test | Previous |
