Topic 4: Exam Pool D (NEW)
A security engineer at an offline government facility is concerned about the validity of an
SSL certificate. The engineer wants to perform the fastest check with the least delay to
determine if the certificate has been revoked. Which of the following would BEST these
requirement?
A.
RA
B.
OCSP
C.
CRL
D.
CSR
CRL
The Chief Financial Officer (CFO) of an insurance company received an email from Ann, the company’s Chief Executive Officer (CEO), requesting a transfer of $10,000 to an account. The email states Ann is on vacation and has lost her purse, containing cash and credit cards. Which of the following social-engineering techniques is the attacker using?
A.
Phishing
B.
Whaling
C.
Typo squatting
D.
Pharming
Whaling
An engineer wants to access sensitive data from a corporate-owned mobile device.
Personal data is not allowed on the device. Which of the following MDM configurations
must be considered when the engineer travels for business?
A.
Screen locks
B.
Application management
C.
Geofencing
D.
Containerization
Containerization
A security analyst sees the following log output while reviewing web logs:
Which of the following mitigation strategies would be BEST to prevent this attack from
being successful?
A.
Secure cookies
B.
Input validation
C.
Code signing
D.
Stored procedures
Input validation
Which of the following would be BEST to establish between organizations that have agreed cooperate and are engaged in early discussion to define the responsibilities of each party, but do not want to establish a contractually binding agreement?
A.
An SLA
B.
AnNDA
C.
ABPA
D.
AnMOU
AnMOU
A security analyst is reviewing a new website that will soon be made publicly available. The analyst sees the following in the URL:
http://dev-site.comptia.org/home/show.php?sessionID=77276554&loc=usThe analyst then sends an internal user a link to the new website for testing purposes, and when the user clicks the link, the analyst is able to browse the website with the following
URL:
http://dev-site.comptia.org/home/show.php?sessionID=98988475&loc=us
Which of the following application attacks is being tested?
A.
Pass-the-hash
B.
Session replay
C.
Object deference
D.
Cross-site request forgery
Session replay
The analyst then sends an internal user a link to the new website for testing purposes, and when the user clicks the link, the analyst is able to browse the website with the following
URL:
http://dev-site.comptia.org/home/show.php?sessionID=98988475&loc=us
Which of the following application attacks is being tested?
A.
Pass-the-hash
B.
Session replay
C.
Object deference
D.
Cross-site request forgery
Session replay
A company is setting up a web server on the Internet that will utilize both encrypted and
unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:

Which of the following steps would be best for the security engineer to take NEXT?
A.
Allow DNS access from the internet.
B.
Block SMTP access from the Internet
C.
The SIP traffic logs
D.
The SNMP logs
Allow DNS access from the internet.
While checking logs, a security engineer notices a number of end users suddenly downloading files with the
.tar.gz extension. Closer examination of the files reveals they are PE32 files. The end users
state they did not initiate any of the downloads. Further investigation reveals the end users
all clicked on an external email containing an infected MHT file with an href link a week
prior. Which of the following is MOST likely occurring?
A.
A RAT was installed and is transferring additional exploit tools.
B.
The workstations are beaconing to a command-and-control server.
C.
A logic bomb was executed and is responsible for the data transfers.
D.
A fireless virus is spreading in the local network environment.
A RAT was installed and is transferring additional exploit tools.
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following: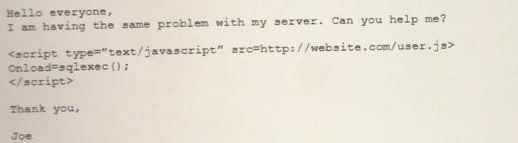
Which of the following BEST describes the attack that was attempted against the forum readers?
A.
SOU attack
B.
DLL attack
C.
XSS attack
D.
API attack
XSS attack
| Page 22 out of 89 Pages |
| SY0-601 Practice Test | Previous |
