Topic 3: Exam Pool C
Which of the following will provide the BEST physical security countermeasures to stop intruders? (Select TWO.)
A.
Alarms
B.
Signage
C.
Lighting
D.
Mantraps
E.
Fencing
F.
Sensors
Mantraps
E.
Fencing
A financial organization has adopted a new secure, encrypted document-sharing
application to help with its customer loan process. Some important PII needs to be shared across this new platform, but it is getting blocked by the DLP systems. Which of the following actions will BEST allow the PII to be shared with the secure application without compromising the organization’s security posture?
A.
Configure the DLP policies to allow all PII
B.
Configure the firewall to allow all ports that are used by this application
C.
Configure the antivirus software to allow the application
D.
Configure the DLP policies to whitelist this application with the specific PII
E.
Configure the application to encrypt the PII
Configure the DLP policies to whitelist this application with the specific PII
A development team employs a practice of bringing all the code changes from multiple team members into the same development project through automation. A tool is utilized to validate the code and track source code through version control. Which of the following BEST describes this process?
A.
Continuous delivery
B.
Continuous integration
C.
Continuous validation
D.
Continuous monitoring
Continuous integration
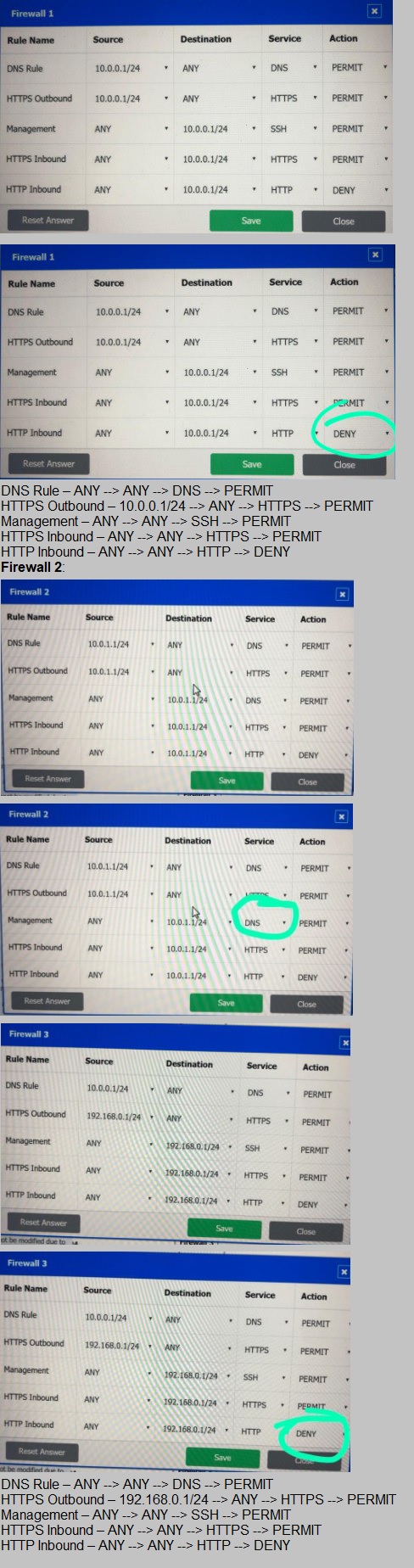
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
Deny cleartext web traffic.
Ensure secure management protocols are used.
Resolve issues at the DR site.
A large industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
A.
Segmentation
B.
Firewall whitelisting
C.
Containment
D.
isolation
Segmentation
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:
Which of the following is the router experiencing?
A.
DDoS attack
B.
Memory leak
C.
Buffer overflow
D.
Resource exhaustion
Resource exhaustion
A network administrator would like to configure a site-to-site VPN utilizing iPSec. The administrator wants the tunnel to be established with data integrity encryption, authentication and anti- replay functions Which of the following should the administrator use when configuring the VPN?
A.
AH
B.
EDR
C.
ESP
D.
DNSSEC
ESP
A network administrator needs to build out a new datacenter, with a focus on resiliency and uptime. Which of the following would BEST meet this objective? (Choose two.)
A.
Dual power supply
B.
Off-site backups
C.
Automatic OS upgrades
D.
NIC teaming
E.
Scheduled penetration testing
F.
Network-attached storage
Dual power supply
B.
Off-site backups
A client sent several inquiries to a project manager about the delinquent delivery status of
some critical reports. The project manager darned the reports were previously sent via
email but then quickly generated and backdated the reports before submitting them via a
new email message Which of the following actions MOST likely supports an investigation
for fraudulent submission?
A.
Establish chain of custody
B.
Inspect the file metadata
C.
Reference the data retention policy
D.
Review the email event logs
Review the email event logs
After consulting with the Chief Risk Officer (CRO). a manager decides to acquire
cybersecurity insurance for the company Which of the following risk management
strategies is the manager adopting?
A.
Risk acceptance
B.
Risk avoidance
C.
Risk transference
D.
Risk mitigation
Risk transference
| Page 19 out of 89 Pages |
| SY0-601 Practice Test | Previous |
