Topic 5: Exam Pool E (NEW)
A large enterprise has moved all its data to the cloud behind strong authentication and encryption. A sales director recently had a laptop stolen and later, enterprise data was round to have been compromised database. Which of the following was the MOST likely cause?
A.
Shadow IT
B.
Credential stuffing
C.
SQL injection
D.
Man-in-the-browser
E.
Bluejacking
Shadow IT
Which of the following is a team of people dedicated testing the effectiveness of
organizational security programs by emulating the techniques of potential attackers?
A.
Red team
B.
While team
C.
Blue team
D.
Purple team
Red team
A smart retail business has a local store and a newly established and growing online
storefront. A recent storm caused a power outage to the business and the local ISP,
resulting in several hours of lost sales and delayed order processing. The business owner
now needs to ensure two things:
* Protection from power outages
* Always-available connectivity In case of an outage
The owner has decided to implement battery backups for the computer equipment Which of
the following would BEST fulfill the owner's second need?
A.
Lease a point-to-point circuit to provide dedicated access.
B.
Connect the business router to its own dedicated UPS.
C.
Purchase services from a cloud provider for high availability
D.
Replace the business's wired network with a wireless network.
Purchase services from a cloud provider for high availability
A document that appears to be malicious has been discovered in an email that was sent to a company's Chief Financial Officer (CFO). Which of the following would be BEST to allow a security analyst to gather information and confirm it is a malicious document without executing any code it may contain?
A.
Open the document on an air-gapped network
B.
View the document's metadata for origin clues
C.
Search for matching file hashes on malware websites
D.
Detonate the document in an analysis sandbox
Detonate the document in an analysis sandbox
A Chief Information Security Officer (CISO) needs to create a policy set that meets
international standards for data privacy and sharing. Which of the following should the CISO read and understand before writing the policies?
A.
PCI DSS
B.
GDPR
C.
NIST
D.
ISO 31000
GDPR
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
A.
SSAE SOC 2
B.
PCI DSS
C.
GDPR
D.
ISO 31000
GDPR
During a routine scan of a wireless segment at a retail company, a security administrator
discovers several devices are connected to the network that do not match the company's
naming convention and are not in the asset Inventory. WiFi access Is protected with 255-
Wt encryption via WPA2. Physical access to the company's facility requires two-factor
authentication using a badge and a passcode Which of the following should the
administrator implement to find and remediate the Issue? (Select TWO).
A.
Check the SIEM for failed logins to the LDAP directory.
B.
Enable MAC filtering on the switches that support the wireless network.
C.
Run a vulnerability scan on all the devices in the wireless network
D.
Deploy multifactor authentication for access to the wireless network
E.
Scan the wireless network for rogue access points.
F.
Deploy a honeypot on the network
Enable MAC filtering on the switches that support the wireless network.
E.
Scan the wireless network for rogue access points.
Explanation: security is pretty good already up to a point, clearly Rogue AP bypass is in the picture MAC filtering on the switch the AP's hang from will ensure the only AP's allowed to touch the core network are approved known AP's and ze "bad guys" will find themselves trapped on an AP island with nowhere to go!
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
A.
Monitoring large data transfer transactions in the firewall logs
B.
Developing mandatory training to educate employees about the removable media policy
C.
Implementing a group policy to block user access to system files
D.
Blocking removable-media devices and write capabilities using a host-based security tool
Blocking removable-media devices and write capabilities using a host-based security tool
A security administrator checks the table of a network switch, which shows the following output: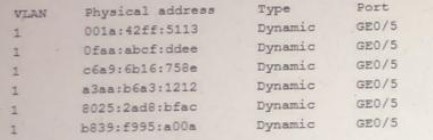
Which of the following is happening to this switch?
A.
MAC Flooding
B.
DNS poisoning
C.
MAC cloning
D.
ARP poisoning
MAC Flooding
Local guidelines require that all information systems meet a minimum-security baseline to
be compliant. Which of the following can security administrators use to assess their system
configurations against the baseline?
A.
SOAR playbook
B.
Security control matrix
C.
Risk management framework
D.
Benchmarks
Benchmarks
| Page 16 out of 89 Pages |
| SY0-601 Practice Test | Previous |
