Topic 4: Exam Pool D (NEW)
The process of passively gathering information poor to launching a cyberattack is called:
A.
tailgating
B.
reconnaissance
C.
pharming
D.
prepending
reconnaissance
A remote user recently took a two-week vacation abroad and brought along a corporateowned
laptop. Upon returning to work, the user has been unable to connect the laptop to
the VPN. Which of the following is the MOST likely reason for the user’s inability to connect
the laptop to the VPN? (Select TWO).
A.
Due to foreign travel, the user’s laptop was isolated from the network.
B.
The user’s laptop was quarantined because it missed the latest path update.
C.
The VPN client was blacklisted.
D.
The user’s account was put on a legal hold
Due to foreign travel, the user’s laptop was isolated from the network.
B.
The user’s laptop was quarantined because it missed the latest path update.
A security analyst is configuring a large number of new company-issued laptops. The
analyst received the following requirements:
• The devices will be used internationally by staff who travel extensively.
• Occasional personal use is acceptable due to the travel requirements.
• Users must be able to install and configure sanctioned programs and productivity suites.
• The devices must be encrypted
• The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the
devices?
A.
Configuring an always-on VPN
B.
Implementing application whitelisting
C.
Requiring web traffic to pass through the on-premises content filter
D.
Setting the antivirus DAT update schedule to weekly
Configuring an always-on VPN
An end user reports a computer has been acting slower than normal for a few weeks.
During an investigation, an analyst determines the system is sending the user's email
address and a ten-digit number to an IP address once a day. The only recent log entry
regarding the user's computer is the following: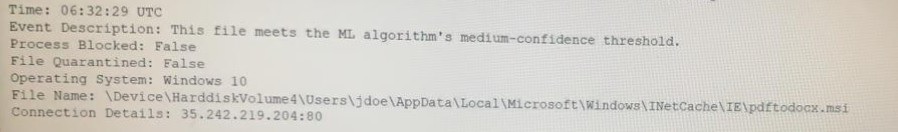
Which of the following is the MOST likely cause of the issue?
A.
The end user purchased and installed a PUP from a web browser
B.
A bot on the computer is brute forcing passwords against a website
C.
A hacker is attempting to exfiltrate sensitive data
D.
Ransomware is communicating with a command-and-control server.
The end user purchased and installed a PUP from a web browser
Which of the following would MOST likely support the integrity of a voting machine?
A.
Asymmetric encryption
B.
Blockchain
C.
Transport Layer Security
D.
Perfect forward secrecy
Perfect forward secrecy
Some laptops recently went missing from a locked storage area that is protected by
keyless RFID-enabled locks. There is no obvious damage to the physical space. The
security manager identifies who unlocked the door, however, human resources confirms
the employee was on vacation at the time of the incident. Which of the following describes
what MOST likely occurred?
A.
The employee's physical access card was cloned.
B.
The employee is colluding with human resources
C.
The employee's biometrics were harvested
D.
A criminal used lock picking tools to open the door.
The employee's physical access card was cloned.
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would BEST support the policy?
A.
Mobile device management
B.
Full-device encryption
C.
Remote wipe
D.
Biometrics
Mobile device management
A network engineer needs to create a plan for upgrading the wireless infrastructure in a
large office Priority must be given to areas that are currently experiencing latency and
connection issues. Which of the following would be the BEST resource for determining the
order of priority?
A.
Nmapn
B.
Heat maps
C.
Network diagrams
D.
Wireshark
Network diagrams
A privileged user at a company stole several proprietary documents from a server. The
user also went into the log files and deleted all records of the incident. The systems
administrator has Just informed investigators that other log files are available for review.
Which of the following did the administrator MOST likely configure that will assist the
investigators?
A.
Memory dumps
B.
The syslog server
C.
The application logs
D.
The log retention policy
The syslog server
A security analyst discovers several .jpg photos from a cellular phone during a forensics
investigation involving a compromised system. The analyst runs a forensics tool to gather
file metadata. Which of the following would be part of the images if all the metadata is still
intact?
A.
The GPS location
B.
When the file was deleted
C.
The total number of print jobs
D.
The number of copies made
The GPS location
| Page 10 out of 89 Pages |
| SY0-601 Practice Test | Previous |
