Topic 1: Exam Set A
A company has implemented a requirement to encrypt all the hard drives on its servers as part of a data loss prevention strategy. Which of the following should the company also perform as a data loss prevention method?
A. Encrypt all network traffic
B. Implement MFA on all the servers with encrypted data
C. Block the servers from using an encrypted USB
D. Implement port security on the switches
Explanation:
Encrypting all hard drives is an important step in data loss prevention (DLP), as it ensures that data stored on the drives cannot be accessed if a disk or server is stolen or improperly decommissioned. However, encryption alone does not prevent unauthorized access to the system while it is running and the data is decrypted for use. To strengthen data protection, the company should implement Multi-Factor Authentication (MFA) on all servers that store or handle encrypted data.
MFA adds an additional layer of security by requiring more than one method of authentication (for example, a password plus a hardware token, biometric factor, or one-time code). This ensures that even if an attacker gains access to user credentials, they still cannot access sensitive data without the second authentication factor. MFA significantly reduces the risk of data breaches, insider threats, and unauthorized access, complementing the encryption policy effectively.
Why the other options are incorrect:
A. Encrypt all network traffic:
While encrypting network traffic (such as using TLS or VPNs) is a good security practice, it protects data in transit, not at rest. It complements but does not directly reinforce hard drive encryption as part of DLP.
C. Block the servers from using an encrypted USB:
Blocking encrypted USBs does not directly enhance protection for encrypted drives on servers; it relates more to removable media policies.
D. Implement port security on the switches:
Port security helps control network access and mitigate MAC address spoofing but does not address access to encrypted data on the servers themselves.
References:
CompTIA Server+ (SK0-005) Exam Objectives, Domain 4.3– “Given a scenario, implement data security methods.”
CompTIA Server+ Study Guide (Exam SK0-005) – Sections on Data Protection, Encryption, and Access Controls.
NIST SP 800-111 – “Guide to Storage Encryption Technologies for End User Devices,” which recommends strong authentication alongside encryption to ensure comprehensive data protection.
Which of the following BEST describes the concept of right to downgrade?
A. It allows for the return of a new OS license if the newer OS is not compatible with the currently installed software and is returning to the previously used OS
B. It allows a server to run on fewer resources than what is outlined in the minimum requirements document without purchasing a license
C. It allows for a previous version of an OS to be deployed in a test environment for each current license that is purchased
D. It allows a previous version of an OS to be installed and covered by the same license as the newer version
Explanation
The Right to Downgrade is a software licensing benefit, most commonly associated with Microsoft volume and retail licenses, that specifically addresses the ability to use older versions of the software.
Core Concept:
When you purchase a license for a new version of an operating system (e.g., Windows Server 2022), the Right to Downgrade permits you to install and run a previously released version (e.g., Windows Server 2019 or 2016) in its place, while still being covered by the newer license you purchased.
Purpose:
This feature is critical in enterprise environments where:
New hardware is purchased with the latest OS pre-installed, but the company's mission-critical applications are only certified or compatible with an older OS version.
An organization is in the process of a slow migration and needs to standardize on an older, stable OS version across all its new hardware purchases.
Why the Other Options are Incorrect
A. It allows for the return of a new OS license...:
This describes a refund or return policy, not the specific licensing benefit of the "Right to Downgrade." The downgrade right lets you use the older version, not return the license.
B. It allows a server to run on fewer resources...:
This relates to minimum system requirements or possibly license compliance regarding resource allocation, not the version of the OS being run.
C. It allows for a previous version of an OS to be deployed in a test environment...:
While you might use a downgraded version for testing, the core right applies to the installation of the older version in place of the licensed version for production use, not just for a limited testing purpose. The benefit is using the older version for the deployment covered by the new license.
Reference
This concept aligns with CompTIA Server+ (SK0-005) Objective 2.1: Explain the importance of server licensing and compliance, which covers understanding different licensing metrics, policies, and terms like downgrade rights, volume licensing, and legal compliance when deploying server operating systems.
After configuring IP networking on a newly commissioned server, a server administrator
installs a straight- through network cable from the patch panel to the switch. The
administrator then returns to the server to test network connectivity using the ping
command. The partial output of the ping and ipconfig commands are displayed below: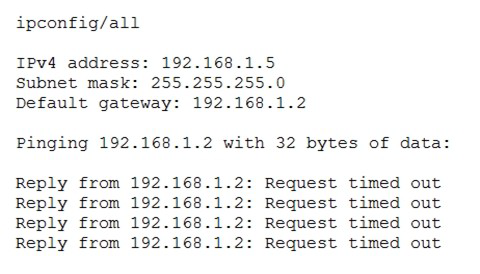
The administrator returns to the switch and notices an amber link light on the port where
the server is connected. Which of the following is the MOST likely reason for the lack of
network connectivity?
A. Network port security
B. An improper VLAN configuration
C. A misconfigured DHCP server
D. A misconfigured NIC on the server
Explanation:
An amber link light on a switch port typically indicates that a physical connection exists but that there is a logical or configuration issue preventing proper communication. In this case, since the server’s network settings appear correct (as shown by the IP configuration) and the physical connection has been verified with a straight-through cable, the most likely cause is an improper VLAN configuration on the switch port.
In managed switches, ports are often assigned to specific VLANs to segment network traffic. If the port connected to the server is placed in the wrong VLAN or left untagged while the rest of the network expects tagging, the server will not be able to communicate with other devices or reach the gateway, resulting in failed ping tests even though the physical link light is active. The amber light supports this diagnosis because many switches use it to indicate limited connectivity or a VLAN mismatch rather than a complete link failure.
To resolve the issue, the administrator should verify that the server’s switch port is assigned to the correct VLAN and that the VLAN configuration matches network design requirements (for example, ensuring access ports are assigned to the correct VLAN or trunk ports are correctly tagged).
Why the other options are incorrect:
A. Network port security:
Port security typically disables the port entirely if a violation occurs, resulting in no link light at all, rather than an amber light.
C. A misconfigured DHCP server:
A DHCP issue would result in an incorrect or missing IP address (such as an APIPA address), but the scenario indicates the IP configuration appears valid.
D. A misconfigured NIC on the server:
If the NIC were misconfigured (e.g., wrong speed or duplex setting), you might see performance issues or intermittent connectivity, but not a VLAN-related amber indicator on the switch.
References:
CompTIA Server+ (SK0-005) Exam Objectives, Domain 2.2 – “Given a scenario, configure network services and networking features.”
CompTIA Server+ Study Guide (SK0-005) – Chapter on Network Configuration and Troubleshooting, section on VLAN setup and port configurations.
Cisco Networking Academy: Switch Port and VLAN Troubleshooting – notes that an amber light often indicates VLAN or spanning tree mismatches.
An administrator is configuring a host-based firewall tor a server. The server needs to allow SSH, FTP, and LDAP traffic. Which of the following ports must be configured so this traffic will be allowed? (Select THREE).
A. 21
B. 22
C. 53
D. 67
E. 69
F. 110
G. 123
H. 389
B. 22
H. 389
Explanations
Port 21 (FTP)
Port 21 is the standard, well-known port used by the File Transfer Protocol (FTP) for the control channel. This channel handles commands, logins, and management of the connection. While the data itself may transfer over a different port (like 20 for Active FTP or a random high port for Passive FTP), Port 21 must be open to initiate and manage any FTP communication.
Port 22 (SSH)
Port 22 is the standard, well-known port used by the Secure Shell (SSH) protocol. This port allows administrators to establish a secure, encrypted remote command-line connection to the server. SSH also underpins other secure file transfer protocols, such as Secure File Transfer Protocol (SFTP) and Secure Copy Protocol (SCP), meaning opening port 22 allows for these secure file transfers as well.
Port 389 (LDAP)
Port 389 is the standard, well-known port used by the Lightweight Directory Access Protocol (LDAP). This protocol is used by client applications and services to query and modify directory services, such as Microsoft Active Directory, to look up user accounts, computer objects, and other network resources. It operates as the unencrypted port for LDAP. (The secure version, LDAPS, uses port 636).
Why the Other Ports are Not Required
C. 53:
This is the port for DNS (Domain Name System), which is used for resolving hostnames to IP addresses. It is not required for the listed services.
D. 67:
This is the port for a DHCP (Dynamic Host Configuration Protocol) server, which is used to automatically assign IP addresses to clients on a network.
E. 69:
This is the port for TFTP (Trivial File Transfer Protocol), a simple, lock-step file transfer protocol without the features of FTP.
F. 110:
This is the port for POP3 (Post Office Protocol version 3), which is used by email clients to retrieve email from a server.
G. 123:
This is the port for NTP (Network Time Protocol), which is used to synchronize the clocks of computers over a network.
Reference
This question aligns with Domain 5.0: Security.
5.4: Given a scenario, implement proper server security controls.
A key part of implementing server security is configuring a host-based firewall. This requires knowledge of common port numbers to create rules that follow the Principle of Least Privilege, opening only the ports that are absolutely necessary for the server's function.
An administrator needs to perform bare-metal maintenance on a server in a remote datacenter. Which of the following should the administrator use to access the server’s console?
A. IP KVM
B. VNC
C. A crash cart
D. RDP
E. SSH
Explanation:
When an administrator needs to perform bare-metal maintenance on a remote server—meaning maintenance at the hardware or firmware level, before the operating system loads—the appropriate tool is an IP-based KVM (Keyboard, Video, Mouse) switch or console.
An IP KVM allows remote access to a server’s physical console over a network connection, providing the same functionality as if the administrator were physically present with a keyboard, monitor, and mouse connected directly to the server. This access includes viewing BIOS/UEFI settings, reinstalling the operating system, or performing diagnostics even when the OS is not running.
This capability is essential in remote datacenters where physical access is limited. Many enterprise servers (such as Dell iDRAC, HPE iLO, or Lenovo IMM) provide IP KVM or similar out-of-band management features built into the hardware for this exact purpose.
Why the other options are incorrect:
B. VNC (Virtual Network Computing):
VNC allows remote control of a server’s graphical desktop environment, but it requires a functioning operating system and network stack. It cannot access hardware-level controls or BIOS settings.
C. A crash cart: A crash cart provides physical access with a monitor, keyboard, and mouse but requires being on-site, which contradicts the “remote datacenter” requirement.
D. RDP (Remote Desktop Protocol):
Like VNC, RDP works at the operating system level and cannot be used when the OS is down or the server is unbootable.
E. SSH (Secure Shell):
SSH is a command-line remote access protocol for networked systems that already have an OS running. It does not provide access to BIOS or hardware-level functions.
References:
CompTIA Server+ (SK0-005) Exam Objectives, Domain 1.4 – “Summarize server hardware installation and maintenance procedures.”
CompTIA Server+ Study Guide (Exam SK0-005) – Chapter on Remote Access and Out-of-Band Management Tools.
Vendor documentation: Dell iDRAC, HPE iLO, Lenovo XClarity – all describe IP KVM as the recommended method for remote console access and bare-metal maintenance.
A server administrator has configured a web server. Which of the following does the administrator need to install to make the website trusted?
A. PKI
B. SSL
C. LDAP
D. DNS
Explanation
The administrator needs to install SSL (Secure Sockets Layer), or more accurately, its modern successor, TLS (Transport Layer Security), to make a website trusted.
SSL/TLS Certificate:
To establish a trusted and encrypted connection (HTTPS) between a web server and a user's browser, the server must have an SSL/TLS certificate. This certificate contains the public key and identity information of the website.
Trust Chain:
This certificate is issued by a trusted Certificate Authority (CA), which is part of a larger Public Key Infrastructure (PKI). When a user's browser connects to the website, it verifies that the certificate is valid, not expired, and issued by a CA it trusts.
Encrypted Communication:
The primary function of SSL/TLS is to use this certificate to negotiate an encrypted connection (e.g., using algorithms like AES) so that all data transmitted (passwords, credit card numbers, etc.) between the user and the server is secure from eavesdropping. The presence of a valid certificate and the use of HTTPS is what signals to the user (via a padlock icon in the browser) that the site is trusted and secure.
Why the other options are incorrect:
A. PKI (Public Key Infrastructure):
PKI is the framework (policies, procedures, and systems, including CAs) that issues and manages the SSL/TLS certificates. While an SSL certificate is part of a PKI, the administrator installs the certificate (SSL/TLS), not the entire infrastructure.
C. LDAP (Lightweight Directory Access Protocol):
LDAP is a protocol used for accessing and maintaining distributed directory information services (like user accounts and group information). It is irrelevant to establishing trust and encryption for a public-facing website.
D. DNS (Domain Name System):
DNS translates human-readable domain names (like google.com) into IP addresses. It is essential for the website to be reachable, but it has no direct role in trusting or encrypting the connection.
Reference
This question relates to Domain 2.0: Server Security and specifically the objective covering security controls and protocols, including the implementation and understanding of PKI and SSL/TLS for secure communications.
A systems administrator is setting up a server on a LAN that uses an address space that follows the RFC 1918 standard. Which of the following IP addresses should the administrator use to be in compliance with the standard?
A. 11.251.196.241
B. 171.245.198.241
C. 172.16.19.241
D. 193.168.145.241
Explanation:
RFC 1918, "Address Allocation for Private Internets," defines specific ranges of IP addresses that are reserved for use on private internal networks (LANs). These addresses are not routable on the public Internet, which helps with security and conserves public IP address space.
The RFC 1918 standard reserves the following three ranges for private use:
10.0.0.0 to 10.255.255.255 (a single Class A network, prefix 10.0.0.0/8)
172.16.0.0 to 172.31.255.255 (16 contiguous Class B networks, prefix 172.16.0.0/12)
192.168.0.0 to 192.168.255.255 (256 contiguous Class C networks, prefix 192.168.0.0/16)
Let's analyze the options:
A. 11.251.196.241:
This address falls within the public range of 11.0.0.0/8, which is owned and routable on the Internet. It is not an RFC 1918 address.
B. 171.245.198.241:
This address is within the public range of 171.0.0.0/8. The private range for the 172.x.x.x space is specifically 172.16.x.x to 172.31.x.x. 171.x.x.x and 172.32.x.x and above are public.
C. 172.16.19.241:
This address falls within the second RFC 1918 range (172.16.0.0 to 172.31.255.255). This is the correct choice.
D. 193.168.145.241:
This address is a public IP address. The private range in the 192.x.x.x space is specifically 192.168.x.x. 193.x.x.x is a publicly routable range.
Why the other options are incorrect:
They all fall outside of the three blocks of IP addresses specifically designated by RFC 1918 for private network use. Using them on a LAN could cause routing conflicts if the server ever needed to communicate with those actual public IP addresses on the Internet.
Reference
This question aligns with Domain 2.0: Networking.
2.2: Given a scenario, configure servers to use network infrastructure services.
A fundamental part of configuring servers is understanding IP addressing, including the difference between public and private (RFC 1918) address spaces. This knowledge is critical for planning a network that will use Network Address Translation (NAT) to communicate with the Internet.
A company is building a new datacenter next to a busy parking lot. Which of the following is the BEST strategy to ensure wayward vehicle traffic does not interfere with datacenter operations?
A. Install security cameras
B. Utilize security guards
C. Install bollards
D. Install a mantrap
Explanation:
When a datacenter is located near a busy parking lot or roadway, one of the primary physical security concerns is accidental or intentional vehicle intrusion. The most effective way to prevent vehicles from crashing into the building or damaging critical infrastructure is to install bollards.
Bollards are short, sturdy vertical posts made of reinforced materials such as steel or concrete. They are typically installed around building perimeters, entrances, and loading docks to act as physical barriers that stop or deflect vehicles while still allowing foot traffic to pass. In a datacenter environment, bollards protect not only the facility itself but also critical systems such as generators, fuel tanks, and external HVAC or cooling units.
Bollards are part of perimeter defense measures, which are the first layer of physical security in a multi-layered datacenter protection strategy.
Why the other options are incorrect:
A. Install security cameras:
Cameras help with surveillance and incident recording but do not prevent vehicles from physically entering or damaging the facility.
B. Utilize security guards:
Security guards enhance deterrence and can respond to incidents, but they cannot physically stop an oncoming vehicle. Guards are a secondary measure, not a physical barrier.
D. Install a mantrap:
A mantrap controls pedestrian access inside the building but provides no protection against vehicle threats outside the facility.
References:
CompTIA Server+ (SK0-005) Exam Objectives, Domain 4.4 – “Summarize physical security concepts.”
CompTIA Server+ Study Guide (Exam SK0-005) – Section on Physical Security Controls, describing bollards as barriers to prevent vehicle intrusion.
NIST SP 800-53, PE-3 (Physical Access Control) – recommends physical barriers such as fences and bollards for facility protection against vehicle threats.
Which of the following is typical of software licensing in the cloud?
A. Per socket
B. Perpetual
C. Subscription-based
D. Site-based
Explanation
C. Subscription-based licensing is the dominant model for software consumption in cloud environments because it directly aligns with the fundamental principles of cloud computing: utility pricing, elasticity, and operational expenditure (OpEx) budgeting.
Alignment with Cloud Economics (Pay-as-you-go):
Cloud providers (like AWS, Azure, and Google Cloud) offer resources—including software—as a service (SaaS, PaaS, or IaaS). Customers are only billed for the resources they actually consume over a set period. Subscription licensing, often billed monthly or annually, perfectly mirrors this pay-as-you-go model, contrasting sharply with the large upfront capital expenditures (CapEx) of traditional software.
Scalability and Elasticity:
Cloud workloads are designed to scale up or down rapidly based on demand. A subscription model accommodates this elasticity. For instance, a license might be tied to the number of virtual CPUs (vCPUs), the number of active users, or the data throughput. As the server administrator scales the deployment, the software subscription fee automatically adjusts, ensuring compliance and efficiency.
Software as a Service (SaaS):
For many cloud applications, the user is effectively "renting" the functionality. The software vendor maintains the code, applies patches, and handles updates, and the customer pays a recurring fee (the subscription) for access and maintenance.
Why the other options are generally not typical in the cloud:
A. Per socket:
This is a traditional hardware-centric metric tied to the physical CPU sockets on a server. In a virtualized, multi-tenant cloud environment, the customer does not have visibility into or control over the physical hardware (sockets) their virtual machine is running on. Licensing must be based on virtualized resources (vCPUs, cores, users, etc.) that the administrator can control and measure.
B. Perpetual:
This model involves a one-time upfront purchase granting ownership of the license rights indefinitely. Cloud deployment favors OpEx (operating expenses) over CapEx (capital expenses). Perpetual licensing creates a CapEx burden that undermines the financial flexibility offered by the cloud. While some legacy software may be brought to the cloud under a Bring Your Own License (BYOL) model, the native cloud model is subscription-based.
D. Site-based:
This is another geography- or location-based model common in traditional enterprise licensing where usage is limited to a single physical office or facility. Cloud services are inherently geographically distributed and accessed remotely, making the concept of a single "site" irrelevant for defining license scope. Cloud licensing is tied to the customer's tenant or account, which can span multiple cloud regions globally.
Reference
This topic is critical for understanding Domain 5.0: Server Virtualization and Cloud Computing, particularly Objective 5.4: Explain cloud concepts and their impact on server administration. A server administrator must recognize how cloud deployment changes operational concerns, including the fundamental shift from traditional asset management to utility-based consumption and subscription licensing.
Hosting data in different regional locations but not moving it for long periods of time describes:
A. a cold site.
B. data at rest.
C. on-site retention.
D. off-site storage.
Explanation:
The question is describing the fundamental state of data, not a location or a disaster recovery strategy.
"Hosting data in different regional locations" implies the data is stored in a fixed place.
"but not moving it for long periods of time" is the key phrase that defines the state of the data. It is inactive and not being transmitted over a network.
The term "data at rest" specifically refers to data that is not actively moving from device to device or network to network. It is data in a persistent storage state, residing on media such as hard drives, tapes, or in cloud storage buckets. The description in the question is a perfect match for this concept.
Why the other options are incorrect:
A. a cold site:
A cold site is a type of disaster recovery facility that has power and connectivity but contains no pre-configured hardware or current data. It is a physical location, not a description of the state of data.
C. on-site retention:
This refers to a policy of keeping data backups or archives within the company's primary physical location. The question specifies "different regional locations," which is the opposite of on-site.
D. off-site storage:
While "hosting data in different regional locations" is a form of off-site storage, this term describes the location of the data, not its state. The core of the question's description is about the data not moving, which is the definition of "at rest." Off-site storage contains data at rest, but the term itself does not describe the data's inactive state.
Reference
This question falls under Domain 5.0: Security.
5.2: Summarize security concepts.
A critical security concept is understanding the three states of digital data:
Data in transit (or in motion): Data moving across a network.
Data in use: Data being actively processed by a CPU.
Data at rest: Data that is stored on a physical or logical medium and is not actively moving.
Each state requires different security controls. For data at rest, common controls include encryption, strict access controls, and physical security for the storage media. The scenario in the question is a textbook description of data at rest.
| Page 12 out of 50 Pages |
