Which of the following phases of the Cyber Kill Chain involves the adversary attempting to establish communication with a successfully exploited target?
A. Command and contro
B. Actions on objectives
C. Exploitation
D. Delivery
Explanation:
In the Cyber Kill Chain — a model developed by Lockheed Martin to describe the stages of a cyberattack — the "Command and Control" (C2) phase is where the attacker attempts to establish communication with the compromised target system after successful exploitation.
This phase enables the adversary to:
Maintain remote access to the target.
Issue commands, download malware, or exfiltrate data.
Create a persistent connection for later stages, such as data theft or sabotage.
Example: Once malware is successfully installed on a victim’s system, it often attempts to reach out to the attacker’s server to receive further instructions — this is Command and Control.
Why the other options are incorrect:
Exploitation:
This is when the adversary executes code to take advantage of a vulnerability. Communication hasn't been established yet.
Delivery:
Involves the transmission of the attack payload (e.g., email, USB, malicious website). No system has been compromised yet.
Actions on objectives:
Happens after C2 is established — this is where the attacker achieves their goal, such as data theft or destruction.
Summary:
The Command and Control (C2) phase is specifically responsible for establishing and maintaining communication between the adversary and the exploited system, making it the correct answer.
Reference:
Lockheed Martin’s Cyber Kill Chain®
Explain the relationship between frameworks, common attack models, and the Cyber Kill Chain.
A security analyst has received an incident case regarding malware spreading out of control on a customer's network. The analyst is unsure how to respond. The configured EDR has automatically obtained a sample of the malware and its signature. Which of the following should the analyst perform next to determine the type of malware, based on its telemetry?
A. Cross-reference the signature with open-source threat intelligence.
B. Configure the EDR to perform a full scan.
C. Transfer the malware to a sandbox environment.
D. Log in to the affected systems and run necstat.
Explanation:
The analyst is trying to identify the type of malware based on telemetry. The best method to analyze malware behavior in a controlled and isolated manner is to transfer it to a sandbox environment.
A sandbox is a secure, isolated environment designed for observing malware behavior without risking production systems. It allows the analyst to:
Observe network activity, file changes, registry modifications, persistence mechanisms, etc.
Determine if the malware is a worm, ransomware, backdoor, trojan, etc.
Correlate observed behavior with known threat intelligence to confirm malware family or campaign.
This step helps in classifying the malware and making informed response decisions.
Why the other options are incorrect:
Cross-reference the signature with open-source threat intelligence:
This can be useful after analyzing behavior, but on its own, it may not provide enough context, especially for new or polymorphic malware.
Configure the EDR to perform a full scan:
A full scan helps find infections, but it doesn’t identify the malware type or its behavior.
Log in to the affected systems and run netstat:
netstat shows current network connections, but it's reactive, limited, and risky if the malware is still active — it may even alert the attacker.
Summary:
To determine the type of malware based on its behavior and telemetry, the analyst should first transfer it to a sandbox environment. This is a best-practice approach in malware analysis and threat classification.
Reference:
CompTIA CySA+ CS0-003 Objective 3.3 – Analyze potential indicators to determine the type of attack.
MITRE ATT&CK – Execution & Command and Control techniques commonly observed in sandbox analysis.
Which of the following would likely be used to update a dashboard that integrates.
A. Webhooks
B. Extensible Markup Language
C. Threat feed combination
D. JavaScript Object Notation
Explanation:
Webhooks are a method for automatically sending real-time data from one application to another. They are commonly used to update dashboards, trigger workflows, or notify systems when new data is available.
In the context of a dashboard integration, webhooks are ideal because they:
Push data instantly when an event occurs (rather than relying on periodic polling).
Are lightweight and efficient.
Can deliver data in formats like JSON, allowing the dashboard to refresh or update in real-time.
For example, if a threat detection system identifies a new incident, it can use a webhook to immediately update a security dashboard with relevant info.
Why the other options are incorrect:
Extensible Markup Language (XML):
XML is a data format, not a mechanism for triggering updates. It may be used within webhooks or APIs but doesn't perform the integration itself.
Threat feed combination:
This is a concept, not a specific tool or method. Combining threat feeds might require webhooks or APIs but isn’t a means of updating a dashboard on its own.
JavaScript Object Notation (JSON):
Like XML, JSON is a data format. It’s often used within webhooks or APIs, but again, it’s not the mechanism that performs the update.
Summary:
When you need to automatically update a dashboard when new data or events occur, webhooks are the most appropriate and commonly used mechanism.
Reference:
CompTIA CySA+ CS0-003 Objective 1.5 – Explain the importance of leveraging threat intelligence sources.
OWASP Webhooks Cheat Sheet – Best practices for secure integration using webhooks.
A security analyst is trying to validate the results of a web application scan with Burp Suite.
The security analyst performs the following:
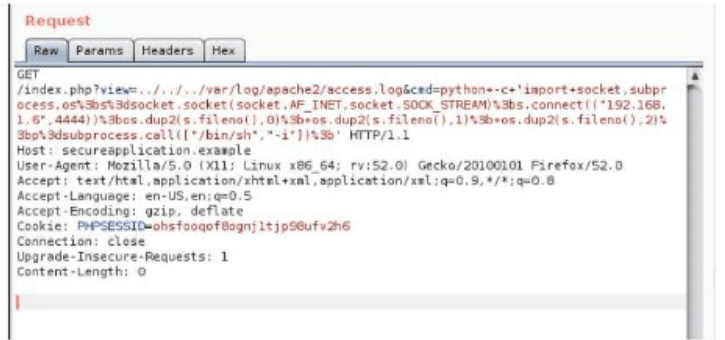
Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
A. SQL injection
B. LFI
C. XSS
D. CSRF
Explanation:
The question asks which vulnerability a security analyst is trying to validate by performing a web application scan with Burp Suite, given a provided code snippet (<script>alert("test");</script>). The snippet is a classic example of a Cross-Site Scripting (XSS) payload, designed to execute JavaScript in a user’s browser. By injecting this script, the analyst is likely testing whether the web application is vulnerable to XSS, as Burp Suite is commonly used to identify such vulnerabilities by injecting and observing payloads. This aligns with the CS0-003 exam’s Vulnerability Management (Domain 2) and Security Operations (Domain 1) objectives, which emphasize validating vulnerabilities in web applications.
Why C is Correct:
XSS Overview: XSS vulnerabilities allow attackers to inject malicious scripts (e.g., JavaScript) into a web application, which execute in the context of a user’s browser. The provided snippet <script>alert("test");</script> is a standard XSS test payload that triggers a pop-up alert if executed, confirming the presence of an XSS vulnerability.
Burp Suite Usage: Burp Suite is a web application testing tool used to intercept, manipulate, and replay HTTP requests. Analysts use it to inject payloads like <script>alert("test");</script> into input fields (e.g., forms, URL parameters) to check if the application fails to sanitize or encode user input, allowing the script to execute.
Validation Process: By injecting the payload and observing if the alert triggers or if the script appears unfiltered in the response, the analyst validates whether the application is susceptible to XSS. This matches the actions described in the question.
CS0-003 Alignment: The exam tests skills in conducting vulnerability scans and validating findings (Domain 2), including identifying XSS through tools like Burp Suite.
Why Other Options Are Wrong:
A. SQL Injection
Reason: SQL injection involves injecting malicious SQL queries (e.g., 1' OR '1'='1) into input fields to manipulate a database. The provided snippet <script>alert("test");</script> is a JavaScript payload, not a SQL query, and is unrelated to database manipulation. SQL injection testing with Burp Suite would involve payloads targeting database errors or unauthorized data access, not JavaScript execution.
B. LFI (Local File Inclusion)
Reason: LFI vulnerabilities allow attackers to include local server files (e.g., /etc/passwd) by manipulating input parameters (e.g., ?file=../../etc/passwd). The snippet <script>alert("test");</script> is a client-side script, not a file path or server-side include attempt, making it irrelevant to LFI. Burp Suite LFI tests would use file path payloads, not JavaScript.
D. CSRF (Cross-Site Request Forgery)
Reason: CSRF exploits a user’s authenticated session to perform unauthorized actions via forged requests (e.g., a malicious tag triggering a POST request). The snippet <script>alert("test");</script> is designed to execute in the browser, not to forge requests. CSRF testing with Burp Suite would involve crafting requests to mimic user actions, not injecting JavaScript alerts.
Additional Context:
Burp Suite Workflow: The analyst likely used Burp Suite’s Proxy or Scanner to inject the payload into a form, URL parameter, or header, then checked the response for the unfiltered script or an alert pop-up, confirming XSS.
XSS Types: The payload suggests testing for reflected or stored XSS, where user input is improperly rendered in the response. Persistent XSS might involve checking if the script is stored and executed for other users.
CS0-003 Relevance: The exam includes performance-based questions (PBQs) on using tools like Burp Suite to validate vulnerabilities, emphasizing XSS due to its prevalence in web applications.
Reference:
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 2 (Vulnerability Management)covering web application vulnerability testing and validation.
CompTIA CySA+ Study Guide: Exam CS0-003 by Chapple and Seidl, discussing Burp Suite and XSS identification techniques.
An organization's email account was compromised by a bad actor. Given the following
Information:
Which of the following is the length of time the team took to detect the threat?
A. 25 minutes
B. 40 minutes
C. 45 minutes
D. 2 hours
Explanation:
The question asks for the length of time the team took to detect a threat related to a compromised email account, with answer options of 25 minutes, 40 minutes, 45 minutes, or 2 hours. However, no specific information (e.g., logs, timelines, or incident details) is provided to calculate the detection time, making it impossible to determine the correct answer. For the CS0-003 exam’s Incident Response and Management (Domain 3) and Security Operations (Domain 1) objectives, detecting a threat involves identifying the time from the initial compromise to when the security team becomes aware of it (Mean Time to Detect, MTTD). Below, I explain the process of calculating detection time and why the options cannot be evaluated without data.
Why No Option Can Be Selected:
Threat Detection Time:
The time to detect a threat is the duration between the compromise (e.g., when the bad actor gains access to the email account) and the moment the security team detects it
Compromise Time:
When the bad actor accessed the account (e.g., via phishing or credential theft).
Detection Time: When the team identified the breach (e.g., through SIEM alerts, unusual login logs, or email activity).
Missing Information:
The question references “the following information,” but no details (e.g., logs, incident timeline, or event descriptions) are provided. Without timestamps or events, the detection time cannot be calculated.
CS0-003 Context:
The exam tests incident response metrics like MTTD, often through performance-based questions (PBQs) requiring log analysis or timeline reconstruction. For example, a log showing a login at 10:00 AM and a SIEM alert at 10:45 AM would indicate a 45-minute detection time.
Hypothetical Analysis:
If details were provided, the detection time would be calculated as:
Example:
Compromise:
Bad actor logs in at 10:00 AM (e.g., log entry: 2025-07-25 10:00:00 [LOGIN] user@example.com from IP 192.168.1.100).
Detection:
SIEM alert at 10:45 AM (e.g., log entry: 2025-07-25 10:45:00 [ALERT] Suspicious login from unauthorized IP).
Detection Time:
10:45 AM - 10:00 AM = 45 minutes.
Without such data, none of the options (25 minutes, 40 minutes, 45 minutes, 2 hours) can be confirmed.
Why Options Cannot Be Evaluated:
A. 25 minutes
Reason: No evidence confirms the team detected the threat in 25 minutes. This would require logs showing the compromise and detection events 25 minutes apart, which aren’t provided.
B. 40 minutes
Reason: Lacking details, there’s no basis to select 40 minutes. The timeline of the compromise and detection is unknown.
C. 45 minutes
Reason: While 45 minutes could be plausible in a typical incident response scenario, no logs or timeline confirm this duration.
D. 2 hours
Reason: Without specific information, 2 hours cannot be verified as the detection time. It could be too long or too short depending on the incident.
Detection Process for Email Compromise:
ndicators: Common signs include unusual logins (e.g., from unfamiliar IPs or locations), suspicious email activity (e.g., unauthorized forwards or rules), or user reports.
Tools: SIEM systems (e.g., Splunk, QRadar), email security solutions (e.g., Microsoft Defender for Office 365), or logs (e.g., Exchange audit logs) help detect compromises.
Steps:
Review authentication logs for unauthorized access.
Check email activity logs for malicious actions (e.g., sent phishing emails).
Identify the time of the first compromise and the detection alert.
Calculate the time difference for MTTD.
Reference:
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 3 (Incident Response and Management), www.comptia.org, covering threat detection and incident response metrics like MTTD.
CompTIA CySA+ Study Guide: Exam CS0-003 by Chapple and Seidl, discussing log analysis for email compromise and incident response timelines.
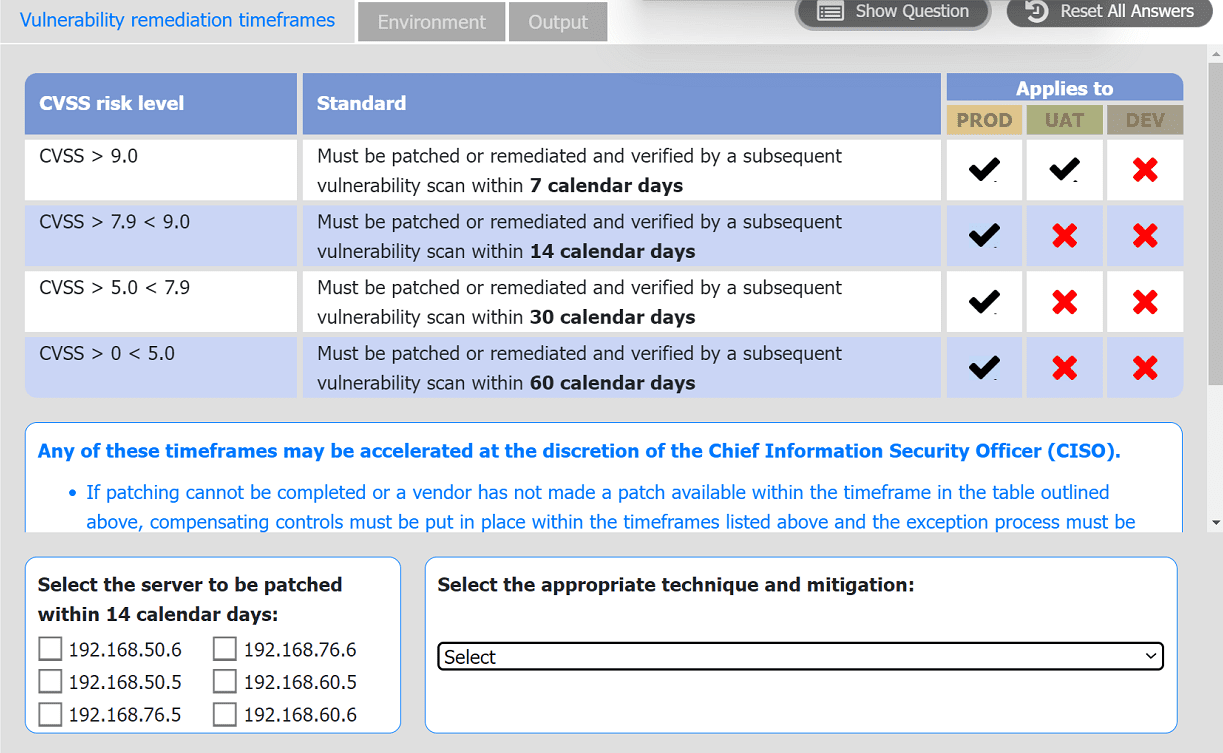
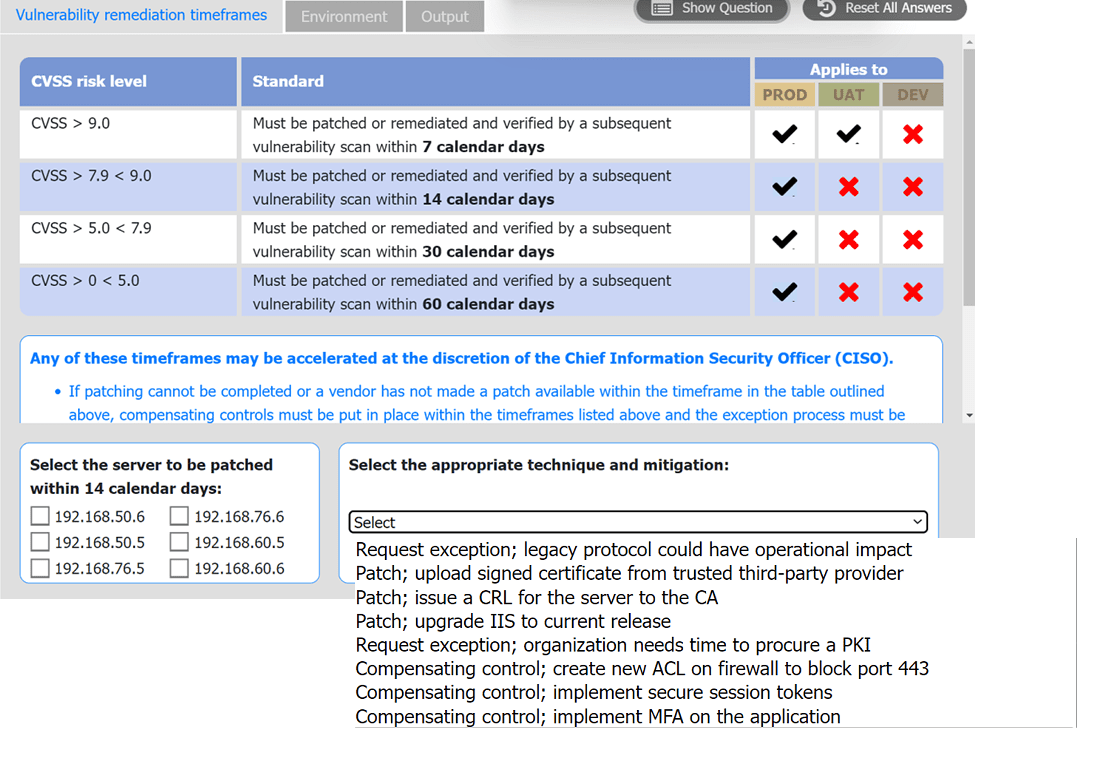
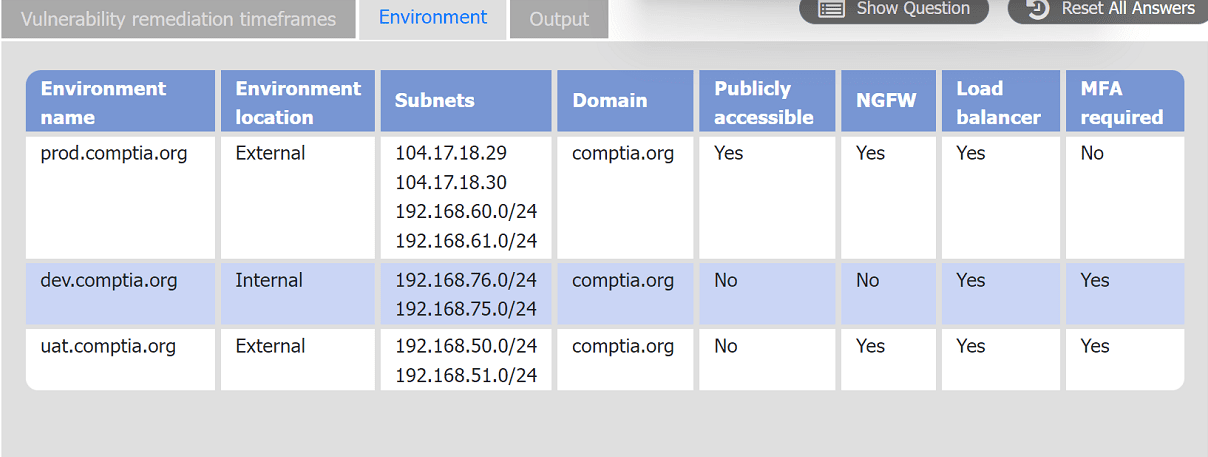
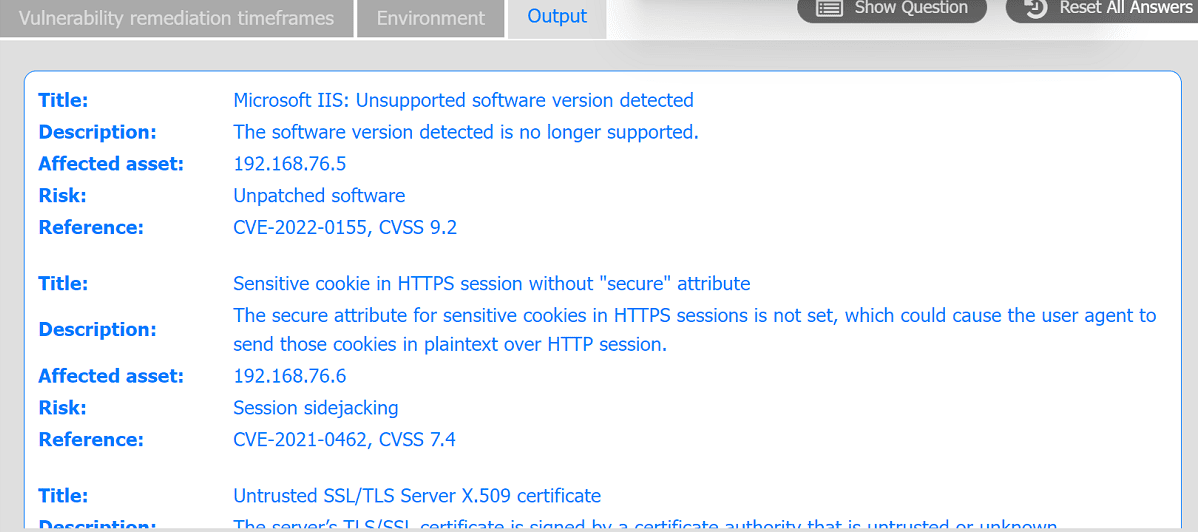
A systems administrator is reviewing the output of a vulnerability scan.
INSTRUCTIONS
Review the information in each tab.
Based on the organization's environment architecture and remediation standards,
select the server to be patched within 14 days and select the appropriate technique
and mitigation.
Explanation:
The question requires reviewing vulnerability scan output to identify which server needs patching within 14 days and selecting the appropriate technique and mitigation based on the organization’s environment architecture and remediation standards. Since no specific tabs or details (e.g., scan results, server roles, CVSS scores, or remediation policies) are provided, I’ll outline the general approach for prioritizing patching and selecting mitigation techniques, as expected in a CS0-003 performance-based question (PBQ).
General Approach to Prioritizing Patching and Mitigation:
Step 1: Review Vulnerability Scan Output:
Identify vulnerabilities, including their severity (e.g., CVSS scores: Critical >9, High 7–8.9, Medium 4–6.9, Low <4)
Note affected servers, their roles (e.g., web server, database server), and network placement (e.g., DMZ, internal).
Check exploitability (e.g., public exploits, zero-day status) and business impact (e.g., critical systems like customer-facing servers).
Step 2: Apply Remediation Standards:
Most organizations prioritize based on severity and SLA timelines (e.g., Critical/High within 14 days, Medium within 30 days).
A 14-day timeline suggests focusing on Critical or High-severity vulnerabilities, especially on exposed or critical servers.
Step 3: Consider Environment Architecture:
Prioritize servers in the DMZ or external-facing systems (e.g., web servers) due to higher exposure.
Account for segmentation, dependencies, or redundancy (e.g., avoid patching all redundant servers simultaneously).
Step 4: Select Patching Technique:
Patch Deployment: Apply vendor-supplied patches to fix the vulnerability (e.g., OS updates, application patches).
Staged Rollout: Test patches in a non-production environment, then apply to production with minimal downtime (e.g., using load balancers).
Automated Tools: Use tools like WSUS, SCCM, or Ansible for efficient patch deployment across servers.
Step 5: Select Mitigation:
Temporary Mitigations: If patching within 14 days isn’t feasible, apply workarounds (e.g., firewall rules, WAF policies, disabling vulnerable services).
Compensating Controls: Use IDS/IPS, network segmentation, or access controls to reduce risk until patching is complete.
Configuration Changes: Adjust settings (e.g., disable unused ports, harden configurations) to mitigate specific vulnerabilities.
Hypothetical Example:
If the scan output (in the missing tabs) showed:
Server A (Web Server, DMZ): Critical vulnerability (CVSS 9.5), exploitable over port 80, public exploit available.
Server B (Internal Database): Medium vulnerability (CVSS 5.0), no public exploit.
Server C (File Server): Low vulnerability (CVSS 3.0).
Server D (Backup Server): High vulnerability (CVSS 8.0), internal network.
Selection:
Server to Patch: Server A (Web Server, DMZ) due to its Critical severity, external exposure, and public exploit, aligning with a 14-day remediation SLA for high-risk systems.
Technique: Deploy the vendor patch (e.g., Apache update) using an automated tool like Ansible, testing in a staging environment first to ensure stability.
Mitigation: Configure the WAF to block exploit attempts on port 80 until the patch is applied, reducing immediate risk.
Why Other Options Would Be Incorrect:
Server B: Medium severity doesn’t typically require patching within 14 days unless specified by the organization’s standards.
Server C: Low severity is lower priority and likely falls outside the 14-day SLA.
Server D: High severity is concerning, but its internal placement reduces exposure compared to Server A’s DMZ location.
Why Options Cannot Be Evaluated:
No Specific Data: The question references tabs with scan output, but without details (e.g., vulnerability severity, server roles, or remediation policies), I cannot select a specific server or confirm the technique and mitigation.
Possible Techniques:
Patch deployment (most common for vulnerabilities).
Configuration hardening (e.g., disabling services).
Virtual patching via WAF/IPS.
Possible Mitigations:
Firewall rules to block vulnerable ports.
Network segmentation to isolate affected servers.
Monitoring with IDS/IPS for exploit attempts.
CS0-003 Context:
The exam tests vulnerability prioritization and remediation (Domain 2), often through PBQs requiring analysis of scan outputs (e.g., Nessus reports) to select servers and mitigations based on risk.
Tools like Nessus, Qualys, or OpenVAS provide CVSS scores, exploitability data, and remediation recommendations to guide decisions.
Remediation standards often follow frameworks like NIST SP 800-53, prioritizing based on severity and system criticality.
Reference:
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 2 (Vulnerability Management), www.comptia.org, covering vulnerability prioritization and remediation strategies.
CompTIA CySA+ Study Guide: Exam CS0-003 by Chapple and Seidl, discussing patch management and mitigation techniques for vulnerability scans.
A security analyst scans a host and generates the following output:
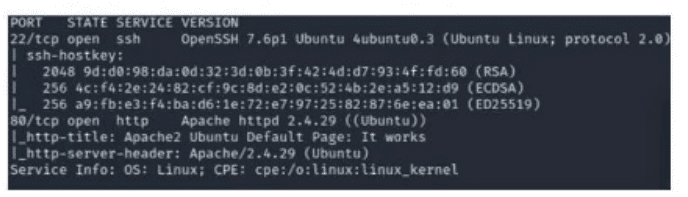
Which of the following best describes the output?
A. The host is unresponsive to the ICMP request.
B. The host Is running a vulnerable mall server.
C. The host Is allowlng unsecured FTP connectlons
D. The host is vulnerable to web-based exploits.
Explanation:
The question asks which option best describes the output of a host scan performed by a security analyst, with choices indicating various vulnerabilities or conditions (unresponsive to ICMP, vulnerable mail server, unsecured FTP connections, or web-based exploits). However, the scan output is not provided, making it impossible to determine the correct answer. For the CS0-003 exam’s Vulnerability Management (Domain 2) and Security Operations (Domain 1) objectives, I’ll outline how to analyze scan output and evaluate each option based on typical scan results, explaining what each option would imply if supported by the output.
General Approach to Analyzing Scan Output:
Scan Output: Vulnerability scans (e.g., Nessus, Qualys, OpenVAS) provide details like open ports, running services, identified vulnerabilities, CVSS scores, and exploitability. The analyst would review:
Open Ports/Services: To identify protocols (e.g., ICMP, SMTP, FTP, HTTP) and their configurations.
Vulnerabilities: Specific issues like outdated software, misconfigurations, or known exploits.
Host Status: Whether the host responds to probes (e.g., ICMP ping) or is filtered.
CS0-003 Context: The exam tests the ability to interpret scan results to identify vulnerabilities and prioritize remediation, often through performance-based questions (PBQs) involving scan output analysis.
Evaluating Each Option:
A. The host is unresponsive to the ICMP request
What It Means: The host doesn’t respond to ICMP (e.g., ping) requests, possibly due to a firewall blocking ICMP or the host being offline.
Expected Output: Scan results showing “Host Unreachable” or “ICMP Request Timed Out” for ping attempts, with no open ports or services listed if the host is completely unresponsive.
Why Uncertain: Without scan output, we can’t confirm if ICMP is blocked or if the host is unresponsive. If the scan lists open ports (e.g., 80, 21), the host is likely responsive, ruling out this option.
B. The host is running a vulnerable mail server
What It Means: The host runs a mail server (e.g., SMTP on port 25, POP3 on 110, or IMAP on 143) with vulnerabilities (e.g., outdated software like old Postfix or Exchange versions, or known exploits).
Expected Output: Scan output showing port 25/110/143 open, with vulnerabilities like “SMTP Server Outdated” or CVSS scores for specific mail server exploits.
Why Uncertain: No output confirms a mail server or related vulnerabilities. The scan would need to explicitly list SMTP-related issues.
C. The host is allowing unsecured FTP connections:
What It Means: The host runs an FTP server (port 21) without encryption (e.g., using plain FTP instead of FTPS/SFTP), allowing unencrypted data transfers that risk interception.
Expected Output: Scan output indicating port 21 open with details like “FTP Anonymous Login Allowed” or “Unencrypted FTP Detected.”
Why Uncertain: Without output, we can’t verify if port 21 is open or if FTP is unsecured. Secure FTP (e.g., SFTP on port 22) wouldn’t qualify for this option.
D. The host is vulnerable to web-based exploits
What It Means: The host runs a web server (e.g., HTTP on port 80, HTTPS on 443) with vulnerabilities like XSS, SQL injection, or outdated web server software (e.g., Apache, IIS).
Expected Output: Scan output showing port 80/443 open, with vulnerabilities like “Apache 2.4.x XSS Vulnerability” or “Web Application Misconfiguration.”
Why Uncertain: No output confirms a web server or web-specific vulnerabilities. The scan would need to list HTTP-related issues.
Why No Option Can Be Selected:
Missing Output: The question references scan output but provides no details (e.g., ports, services, vulnerabilities, or CVSS scores). Without this, we can’t determine if the host is unresponsive, running a vulnerable mail server, allowing unsecured FTP, or vulnerable to web exploits.
Hypothetical Example:
If the output showed: Port 21 open, FTP Service, Anonymous Login Enabled, option C would be correct.
If it showed: Port 25 open, SMTP Postfix 2.10, CVE-2023-1234, option B would be correct.
it showed: ICMP Request Timed Out, No Ports Detected, option A would be correct.
If it showed: Port 80 open, Apache 2.4.29, XSS Vulnerability, option D would be correct.
Without such details, no option can be confirmed.
CS0-003 Analysis Process:
Steps:
Review Scan Output: Check for open ports, services, and vulnerabilities using tools like Nessus or Qualys.
Correlate Findings: Match findings to options (e.g., port 21 for FTP, port 80 for web exploits).
Prioritize: Use CVSS scores or exploitability to assess severity (Domain 2).
Document: Note findings for remediation or reporting (Domain 4).
Tools: Nessus, Qualys, OpenVAS, or Nmap for host scanning.
Reference:
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 2 (Vulnerability Management), www.comptia.org, covering scan output analysis and vulnerability identification.
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 2 (Vulnerability Management), www.comptia.org, covering scan output analysis and vulnerability identification.
CompTIA CySA+ Study Guide: Exam CS0-003 by Chapple and Seidl, discussing how to interpret vulnerability scan results.
Which of the following is the best reason to implement an MOU?
A. To create a business process for configuration management
B. To allow internal departments to understand security responsibilities
C. To allow an expectation process to be defined for legacy systems
D. To ensure that all metrics on service levels are properly reported
Explanation:
The question asks for the best reason to implement a Memorandum of Understanding (MOU) in the context of the CompTIA CySA+ (CS0-003) exam, which focuses on cybersecurity operations, incident response, and vulnerability management. An MOU is a formal agreement between parties that outlines roles, responsibilities, and expectations, typically without being legally binding. Among the given options, allowing internal departments to understand security responsibilities is the most aligned with the purpose of an MOU, as it clarifies how different departments within an organization collaborate on security-related tasks. This aligns with the CS0-003 exam’s Reporting and Communication (Domain 4) and Security Operations (Domain 1) objectives, which emphasize effective communication and coordination of security roles.
Why B is Correct:
MOU Purpose: An MOU is used to document mutual agreements between internal departments or entities, specifying roles, responsibilities, and expectations. In a cybersecurity context, it clarifies who is responsible for tasks like monitoring, incident response, or vulnerability management.
Security Responsibilities: Internal departments (e.g., IT, HR, legal) often have overlapping or unclear security roles. An MOU helps define these (e.g., IT manages endpoint security, HR ensures compliance training), reducing confusion and improving coordination.
CS0-003 Alignment: The exam emphasizes communication and collaboration within organizations to support security operations and incident response. An MOU supports this by ensuring departments understand their security obligations, such as who escalates incidents or implements controls.
Other Options Are Wrong:
A. To create a business process for configuration management
Reason: Configuration management processes are typically defined in formal policies or procedures, not an MOU. An MOU outlines high-level agreements between parties, not detailed operational processes like change control or configuration baselines. While configuration management is critical for security (Domain 1), it’s not the primary purpose of an MOU.
C. To allow an expectation process to be defined for legacy systems
Reason: An MOU could include expectations for managing legacy systems (e.g., who maintains them), but this is too specific and not the primary purpose. MOUs focus on broader agreements about responsibilities, not system-specific processes. Legacy system management would be addressed in technical policies or risk assessments, not an MOU.
D. To ensure that all metrics on service levels are properly reported
Reason: Service level metrics are typically managed through Service Level Agreements (SLAs), which are more formal and specific about performance and reporting (e.g., uptime, response times). An MOU is less about metrics and more about clarifying roles and responsibilities, making this option incorrect.
Additional Context:
MOU in Cybersecurity: An MOU might outline how the SOC collaborates with IT for incident response or how compliance teams work with security for audits. For example, it could specify that IT deploys patches while the SOC monitors for exploits.
CS0-003 Relevance: Domain 4 (Reporting and Communication) emphasizes clear documentation and communication of security roles, which an MOU facilitates. It supports cross-departmental alignment in complex organizations.
Example: An MOU between the SOC and IT might state: “SOC monitors SIEM alerts; IT implements firewall rules within 24 hours of notification.”
Reference:
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 4 (Reporting and Communication), www.comptia.org, covering collaboration and documentation of security responsibilities.
CompTIA CySA+ Study Guide: Exam CS0-003 by Chapple and Seidl, discussing MOUs as tools for clarifying roles in security operations.
A systems administrator needs to gather security events with repeatable patterns from Linux log files. Which of the following would the administrator most likely use for this task?
A. A regular expression in Bash
B. Filters in the vi editor
C. Filters in the vi editor
D. Filters in the vi editor
Explanation:
The question asks which tool a systems administrator would most likely use to gather security events with repeatable patterns from Linux log files. The task involves identifying specific patterns (e.g., error messages, failed logins) in log files, which is best accomplished using regular expressions (regex) in a Bash environment. This aligns with the CS0-003 exam’s Security Operations (Domain 1) and Incident Response and Management (Domain 3) objectives, which emphasize log analysis and pattern matching for security event identification.
Why A is Correct:
Regular Expressions in Bash: Regex is a powerful tool for pattern matching in text, ideal for extracting security events with repeatable patterns (e.g., IP addresses, timestamps, or error codes) from Linux log files (e.g., /var/log/auth.log). Tools like grep, awk, or sed in Bash use regex to filter and extract relevant lines.
Linux Log Analysis: Common security events (e.g., failed SSH logins: sshd.*Failed password) are identified by searching logs with regex patterns. For example, grep "Failed password" /var/log/auth.log extracts failed login attempts.
Efficiency and Flexibility: Bash regex is widely used in Linux for scripting and automation, allowing administrators to create repeatable, automated searches for security events across multiple log files.
CS0-003 Alignment: The exam tests skills in analyzing logs for security events using command-line tools, with regex being a standard method for pattern matching in Linux environments.
Why Other Options Are Wrong:
B. Filters in the vi editor
Reason: The vi/vim editor supports basic search and filtering (e.g., :/pattern to search for a pattern), but it’s designed for interactive text editing, not bulk log analysis. It’s impractical for processing large log files or extracting repeatable patterns across multiple files, unlike Bash regex with grep or awk. The vi editor lacks automation and scalability for this task.
C. Filters in the vi editor
Reason: This option is identical to B and incorrect for the same reasons. Vi/vim filters are not suited for systematic log analysis or extracting security events with repeatable patterns, as they require manual interaction and are less efficient than Bash regex tools
D. Filters in the vi editor
Reason: Again, identical to B and C. The repetition of this option in the question appears to be an error, but vi/vim filters remain unsuitable for gathering security events from logs due to their interactive nature and lack of automation compared to regex in Bash.
Additional Context:
Example Use Case: To find failed SSH login attempts in /var/log/auth.log, an administrator might use: grep -E "sshd.*Failed password.*from [0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}" /var/log/auth.log, which uses regex to match IP addresses and specific error patterns.
Tools: Common Bash tools for regex include:
grep -E for extended regex.
awk for complex pattern extraction.
sed for pattern-based text manipulation.
CS0-003 Relevance: The exam includes performance-based questions (PBQs) testing log analysis skills, often requiring commands like grep or awk to identify security events in Linux logs.
Reference:
CompTIA CySA+ (CS0-003) Exam Objectives, Domains 1 (Security Operations) and 3 (Incident Response and Management), www.comptia.org, covering log analysis and command-line tools for security event identification.
CompTIA CySA+ Study Guide: Exam CS0-003 by Chapple and Seidl, discussing regex and Linux log analysis for security operations.
A security analyst is viewing a recorded session that captured suspicious activity:
scanning 192.168.10.10...
scan timing: about 10% done...
...
scan completed (4 host up); scanned 4 hosts in 1348 sec.
HOSt Port State Service
192.168.10.10 1 closed unknown
192.168.10.20 1 closed unknown
192.168.10.30 1 closed unknown
192.168.10.40 1 closed unknown
Which of the following best describes the activity shown?
A. UDP scan
B. SYN scan
C. XMAS tree scan
D. Half-open scan
Explanation:
The output shows that:
The scan ran across 4 hosts.
Port 1 is reported as "closed" on all of them.
The service is listed as "unknown".
No open or filtered ports are reported.
The scan took a long time (1348 seconds) for just 4 hosts.
These are strong indicators of a UDP scan.
Why It’s a UDP Scan:
UDP scans use the nmap -sU option and typically take longer because:
UDP is connectionless, so no three-way handshake like TCP.
The scanner waits for timeouts or ICMP port unreachable messages.
When a UDP port is closed, the host often replies with ICMP Port Unreachable, which matches the "Closed Unknown" response.
Open UDP ports may not respond at all, and Nmap might report them as open|filtered.
"Unknown" service suggests it’s a port with no identifiable service signature, which is typical on port 1.
Why the Other Options Are Incorrect:
SYN scan / Half-open scan (nmap -sS):
A TCP scan that sends SYN packets to initiate a connection but doesn't complete the handshake.
Results would mention open/filtered/closed TCP ports, not just "unknown" service on port 1.
XMAS tree scan:
Sends TCP packets with FIN, URG, and PSH flags set.
Used to bypass firewalls and IDS systems.
Only works on TCP, not UDP, and usually shows no response for open ports or RST for closed.
Summary:
Because of the slow timing, "closed unknown" status, and lack of service identification, this scan behavior is most consistent with a UDP scan.
| Page 4 out of 45 Pages |
