A security analyst is trying to identify possible network addresses from different source networks belonging to the same company and region. Which of the following shell script functions could help achieve the goal?
A. function w() { a=$(ping -c 1 $1 | awk-F ”/” ’END{print $1}’) &;&; echo “$1 | $a” }
B. function x() { b=traceroute -m 40 $1 | awk ’END{print $1}’) && echo “$1 | $b” }
C. function y() { dig $(dig -x $1 | grep PTR | tail -n 1 | awk -F ”.in-addr” ’{print$1}’).origin.asn.cymru.com TXT +short }
D. function z() { c=$(geoiplookup$1) && echo “$1 | $c” }
Correct Answer:
function y() {dig $(dig -x $1 | grep PTR | tail -n 1 | awk -F ".in-addr" '{print$1}').origin.asn.cymru.com TXT +short}
This function uses DNS-based ASN lookups to identify Autonomous System Numbers (ASNs) and associated information about the IP address:
It first performs a reverse DNS lookup using dig -x $1.
It filters for PTR records to extract the hostname.
Then, it performs another dig query on the domain origin.asn.cymru.com, which is a service provided by Team Cymru for ASN lookups.
Why it's correct:
It helps the analyst determine which ASNs (i.e., network providers or owners) the IPs belong to.
ASN data can be used to group IPs from the same organization or region, even across different ranges.
This is highly useful in attribution, threat hunting, and correlating events tied to a single entity or provider.
Incorrect Options:
function w() {a=$(ping -c 1 $1 | awk -F “/” ’END{print $1}’) &;&; echo “$1 | $a”}
This function uses ping to check host reachability and tries to parse the response.
It is not helpful for identifying network ownership or origin.
Also, the syntax &;&; is invalid in shell scripting.
Ping only tells you latency and availability, not network association or location.
function x() {b=traceroute -m 40 $1 | awk ’END{print $1}’) && echo “$1 | $b”}
This function runs a traceroute and prints the last hop.
While traceroute can provide routing paths, it does not give ownership or ASN data.
This method won't help group IPs under the same organization or region effectively.
function z() {c=$(geoiplookup $1) && echo “$1 | $c”}
This script uses geoiplookup, which returns geographic location (like country/city) of an IP.
While geographic info can be helpful, it’s not sufficient to identify whether networks belong to the same company.
Two IPs can be in the same city but belong to completely unrelated networks.
Reference:
CompTIA CySA+ CS0-003 Objective
Domain 1.1:Apply cyber threat intelligence to support security operations
Several reports with sensitive information are being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
A. Implement step-up authentication for administrators.
B. Improve employee training and awareness
C. Increase password complexity standards.
D. Deploy mobile device management
Explanation
:
The question is part of the Security Operations domain (33% weighting) of the CompTIA CySA+ (CS0-003) exam, aligning with Objective 1.5 (Recommend process improvements to security operations). The scenario involves sensitive information being disclosed via file sharing services, indicating a data leakage issue, likely due to insider threats, poor security practices, or misconfigured systems. The goal is to identify a security control that directly addresses this threat to improve the company’s security posture. The correct answer must focus on mitigating unauthorized sharing of sensitive data, per CS0-003’s emphasis on enhancing security operations and NIST SP 800-53 guidelines for data protection.
Correct Answer:
Improve employee training and awareness.
Improving employee training and awareness is the best security control to address sensitive information disclosure via file sharing services. Many data leaks result from employees inadvertently sharing sensitive files due to lack of awareness about secure practices, such as using unapproved file sharing platforms or mishandling data. Training programs educate staff on recognizing phishing attempts, using approved secure file sharing tools, and following data handling policies. For example, employees can learn to encrypt sensitive files or use company-sanctioned platforms like OneDrive with DLP controls. This aligns with CS0-003 Objective 1.5, as it strengthens the human element of security, a common weak point. NIST SP 800-53 (AT-2) emphasizes security awareness training to mitigate insider threats and improve security posture.
Incorrect Answers:
1)Implement step-up authentication for administrators.
Step-up authentication requires additional verification (e.g., MFA) for sensitive administrative actions. While useful for securing privileged access, it does not directly address employees sharing sensitive information via file sharing services, as most disclosures are not tied to admin accounts. For instance, a regular employee using a personal Dropbox account to share files wouldn’t be impacted by admin-focused authentication. For CS0-003 Objective 1.5, step-up authentication is relevant for access control (NIST SP 800-53 AC-7) but not the primary control for preventing data leaks through file sharing. Training addresses the broader user base, making it more effective for this scenario’s threat.
2)Increase password complexity standards:
Increasing password complexity strengthens authentication by requiring stronger passwords, reducing the risk of credential compromise. However, this control does not directly prevent sensitive information from being shared via file sharing services, as disclosures are often intentional or accidental by authorized users, not due to hacked accounts. For example, an employee with a complex password can still upload sensitive files to an unsecure service. For CS0-003 Objective 1.5, password policies (NIST SP 800-53 IA-5) enhance authentication but are secondary to training, which directly addresses user behavior and awareness, the root cause of most data leakage incidents.
3)Deploy mobile device managemen:
Mobile Device Management (MDM) enforces security policies on mobile devices, such as encryption or app restrictions, to prevent data leaks. While useful for securing devices accessing company data, it does not directly address disclosures via file sharing services, which often occur from desktops or unauthorized platforms. For example, MDM won’t prevent an employee from uploading files to a personal cloud service from a laptop. For CS0-003 Objective 1.5, MDM (NIST SP 800-53 MP-7) is relevant for device security but less effective than training, which educates users on proper data handling across all platforms, directly mitigating the threat.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 1 (Security Operations), Objective 1.5 (Recommend process improvements to security operations).
NIST SP 800-53: Security and Privacy Controls for Information Systems and Organizations, AT-2 (Security Awareness Training) and related controls.
Sybex CompTIA CySA+ Study Guide: Exam CS0-003 by Mike Chapple and David Seidl: Covers security awareness training for data protection.
Udemy: CompTIA CySA+ (CS0-003) Complete Course by Jason Dion: Discusses insider threat mitigation through training.
SANS Institute: Resources on security awareness training to prevent data leakage.
Additional Notes:
Insider Threats: Data leakage via file sharing often stems from insider actions (intentional or accidental). CS0-003 emphasizes training to mitigate these risks.
Data Loss Prevention (DLP): While not an option here, DLP tools complement training by monitoring and blocking unauthorized file sharing, often tested in PBQs.
Security Awareness: NIST SP 800-53 (AT-2) highlights training as a foundational control to reduce human-related security incidents.
An end-of-life date was announced for a widely used OS. A business-critical function is performed by some machinery that is controlled by a PC, which is utilizing the OS that is approaching the end-of- life date. Which of the following best describes a security analyst's concern?
A. Any discovered vulnerabilities will not be remediated.
B. An outage of machinery would cost the organization money.
C. Support will not be available for the critical machinery
D. There are no compensating controls in place for the OS.
Correct Answer:
Explanation:
Any discovered vulnerabilities will not be remediated is the best description of a security analyst’s concern when an operating system (OS) reaches its end-of-life (EOL).
When an OS reaches EOL, the vendor stops providing security updates and patches, leaving the system exposed to newly discovered vulnerabilities.
These unpatched vulnerabilities can be exploited by threat actors, especially if the system is still connected to a network or has internet exposure.
The lack of vendor support effectively means that any exploit found after the EOL date will remain unaddressed, creating a significant security risk.
For business-critical systems like the one described, continued use of an EOL OS increases the attack surface, especially for zero-day vulnerabilities that remain permanently unpatched.
In risk terms, this is known as increased vulnerability exposure due to absence of remediation options.
Incorrect Answer Explanations:
An outage of machinery would cost the organization money
This is a valid business continuity concern but not the primary security concern.
The question is from a security analyst’s perspective, not an operations manager.
The issue isn’t about downtime—it's about security risks from unpatched vulnerabilities.
While machinery outages are important, they're a secondary issue here.
Support will not be available for the critical machinery
:
This refers to technical support, which might still be available from the machinery vendor.
The question specifically targets the OS, not the machinery.
A security analyst’s main concern isn’t support contracts but the security posture—which is compromised by the lack of security patches.
There are no compensating controls in place for the OS
This may or may not be true, and it's speculative.
The scenario doesn’t say whether compensating controls (e.g., network segmentation, host-based firewalls) are present.
While a lack of controls is certainly a concern, the most immediate and direct risk is the OS being left unpatched.
Also, compensating controls reduce risk; they don't eliminate the core issue, which is the lack of vendor patches for new vulnerabilities.
References:
1)NIST SP 800-40 Rev. 3 – Guide to Enterprise Patch Management Technologies
Describes the critical importance of timely patching and risks associated with unsupported software.
2)CompTIA CySA+ CS0-003 Objectives
Domain 2.4: Apply security solutions for infrastructure management
Domain 3.4: Apply risk mitigation techniques to secure the enterprise environment
A security analyst needs to provide evidence of regular vulnerability scanning on the company's network for an auditing process. Which of the following is an example of a tool that can produce such evidence?
A. OpenVAS
B. Burp Suite
C. Nmap
D. Wireshark
Explanation
:
The question pertains to the Vulnerability Management domain (30% weighting) of the CompTIA CySA+ (CS0-003) exam, aligning with Objective 2.1 (Given a scenario, implement vulnerability scanning methods and techniques). The task requires identifying a tool that can provide evidence of regular vulnerability scanning on a company’s network for an audit. The tool must be capable of detecting vulnerabilities across network assets and generating reports suitable for audit purposes. The correct answer should align with CS0-003’s focus on vulnerability scanning tools and their role in compliance, as per frameworks like NIST SP 800-53.
Correct Answer:
OpenVAS:
OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanning tool that can produce evidence of regular vulnerability scanning for an audit. It scans network hosts for known vulnerabilities, such as outdated software or misconfigurations, and generates detailed reports listing identified issues, severity levels, and remediation steps. For example, an OpenVAS report can document scan dates, scanned IP ranges, and vulnerabilities found, meeting audit requirements for compliance. This aligns with CS0-003 Objective 2.1, which emphasizes implementing vulnerability scanning methods. OpenVAS is widely used for network-wide scans, supports compliance needs (e.g., PCI DSS), and provides auditable evidence, as recommended by NIST SP 800-53 (RA-5) for vulnerability management.
Incorrect Answers:
1)Burp Suite:Burp Suite is a web application security testing tool used for identifying vulnerabilities like XSS or SQL injection in web applications. While powerful for targeted web scans, it is not designed for comprehensive network vulnerability scanning, focusing instead on application-layer issues. Its reports are specific to web vulnerabilities, not broad network scans required for audits. For CS0-003 Objective 2.1, Burp Suite is relevant for web-focused assessments but not for producing evidence of regular network-wide vulnerability scanning. NIST SP 800-53 (RA-5) emphasizes tools like OpenVAS for network scans, making Burp Suite unsuitable for this audit-focused scenario.
2)Nmap Long:Nmap is a network scanning tool used for discovery, port scanning, and service enumeration, identifying open ports, services, and operating systems. While it can detect some vulnerabilities using scripts (e.g., NSE), it is primarily a reconnaissance tool, not a dedicated vulnerability scanner. Its output lacks the detailed vulnerability reports needed for audits, focusing on network mapping instead. For CS0-003 Objective 2.1, Nmap supports initial discovery but not comprehensive vulnerability scanning. NIST SP 800-53 (RA-5) requires tools like OpenVAS for auditable vulnerability reports, making Nmap inadequate for producing the required evidence.
3)Wireshark:Wireshark is a network protocol analyzer used for capturing and inspecting network traffic to troubleshoot or detect anomalies. It does not perform vulnerability scanning or generate reports on network vulnerabilities, focusing instead on packet-level analysis. For example, Wireshark can identify suspicious traffic but not software vulnerabilities or misconfigurations needed for audit evidence. For CS0-003 Objective 2.1, Wireshark is relevant for network monitoring (Objective 1.4), not vulnerability scanning. NIST SP 800-53 (RA-5) emphasizes dedicated vulnerability scanners like OpenVAS for audit purposes, making Wireshark unsuitable for this scenario’s requirements
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 2 (Vulnerability Management), Objective 2.1 (Given a scenario, implement vulnerability scanning methods and techniques).
NIST SP 800-53: Security and Privacy Controls for Information Systems and Organizations, RA-5 (Vulnerability Monitoring and Scanning).
Sybex CompTIA CySA+ Study Guide: Exam CS0-003 by Mike Chapple and David Seidl: Covers vulnerability scanning tools like OpenVAS.
Udemy: CompTIA CySA+ (CS0-003) Complete Course by Jason Dion: Discusses tools for vulnerability management and audit compliance.
OpenVAS Documentation: Details reporting capabilities for vulnerability scans.
Additional Notes:
Vulnerability Scanning Tools: CS0-003 tests knowledge of tools like OpenVAS, Nessus, and Qualys for network vulnerability scanning, often in PBQs requiring report interpretation.
Audit Evidence: Audits require documented evidence, such as scan schedules and reports, to demonstrate compliance with standards like PCI DSS or NIST SP 800-53.
Tool Selection: Choosing the right tool for the task (e.g., network vs. web scanning) is critical for CS0-003 scenarios, emphasizing practical application.
While a security analyst for an organization was reviewing logs from web servers. the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks. Which of the following combinations of configuration changes should the organization make to remediate this issue? (Select two).
A. Configure the server to prefer TLS 1.3.
B. Remove cipher suites that use CBC.
C. Configure the server to prefer ephemeral modes for key exchange.
D. Require client browsers to present a user certificate for mutual authentication.
E. Configure the server to require HSTS.
F. Remove cipher suites that use GCM.
B. Remove cipher suites that use CBC.
Correct Answer:
1. Configure the server to prefer TLS 1.3
TLS 1.3 removes support for older, insecure cipher suites, including those that are vulnerable to padding oracle attacks
It also removes static RSA and Diffie-Hellman key exchanges, further improving security.
TLS 1.3 enforces stronger forward secrecy and eliminates insecure features like renegotiation.
Upgrading to TLS 1.3 helps mitigate downgrade attacks and ensures only modern, secure algorithms are used.
Why it matters: Padding oracle attacks exploit weaknesses in how CBC (Cipher Block Chaining) padding is validated. TLS 1.3 doesn’t support CBC, so it avoids the vulnerability altogether.
2. Remove cipher suites that use CBC
CBC (Cipher Block Chaining) modes are susceptible to padding oracle attacks, such as BEAST, POODLE, and Lucky13.
Removing CBC-based ciphers ensures the server won’t offer insecure options that clients can be tricked into using.
Instead, you should use AEAD cipher modes like GCM (Galois/Counter Mode), which are not vulnerable to padding attacks.
Why it matters: Even if TLS 1.2 is in use, removing CBC suites reduces the attack surface and mitigates vulnerabilities in older protocol versions.
Incorrect Answer:
Configure the server to prefer ephemeral modes for key exchange
This is related to forward secrecy, not padding oracle vulnerabilities.
While good for security, it does not directly mitigate padding oracle attacks.
Ephemeral key exchange protects past sessions in case of key compromise—not relevant to the padding issues in CBC.
Require client browsers to present a user certificate for mutual authentication
This is about client authentication, not cipher selection or encryption mode.
Mutual TLS (mTLS) increases security but doesn't prevent padding oracle or downgrade attacks.
Also, it adds complexity and is rarely used for public-facing web servers.
Configure the server to require HSTS
HSTS (HTTP Strict Transport Security) ensures browsers use HTTPS, preventing SSL stripping.
It does not affect the choice of cipher suites or TLS version used.
HSTS improves overall transport security but doesn’t mitigate padding oracle vulnerabilities.
References:
OWASP: Padding Oracle Attacks
NIST SP 800-52 Rev. 2: Guidelines for the Selection, Configuration, and Use of TLS
RFC 8446: TLS 1.3 Specification
A manufacturer has hired a third-party consultant to assess the security of an OT network that includes both fragile and legacy equipment Which of the following must be considered to ensure the consultant does no harm to operations?
A. Employing Nmap Scripting Engine scanning techniques
B. Preserving the state of PLC ladder logic prior to scanning
C. Using passive instead of active vulnerability scans
D. Running scans during off-peak manufacturing hours
Explanation
:
Operational Technology (OT) environments often include legacy systems and fragile equipment that are highly sensitive to network disruptions. CompTIA’s CySA+ CS0-003 exam emphasizes the importance of non-intrusive assessment techniques when evaluating such environments. The goal is to ensure security assessments do not interfere with production or damage critical systems.
Correct Answer:
Using passive instead of active vulnerability scans:
Passive vulnerability scanning is the safest method for assessing OT networks with fragile or legacy equipment. Unlike active scans, which send probes and packets that may disrupt operations, passive scans observe existing network traffic without interacting directly with devices. This approach minimizes the risk of crashing systems or interfering with industrial processes. According to CompTIA’s guidance, passive scanning is preferred in sensitive environments because it allows analysts to gather security insights without introducing instability or downtime.
Incorrect Answer:
Employing Nmap Scripting Engine scanning techniques:
The Nmap Scripting Engine (NSE) is a powerful tool for active scanning and vulnerability detection. However, it sends crafted packets and executes scripts that can be intrusive. In OT environments, this can lead to unexpected behavior or system crashes. CompTIA advises caution when using active tools like Nmap in fragile networks, as they may cause harm to legacy equipment or disrupt operations.
Preserving the state of PLC ladder logic prior to scanning:
While preserving PLC (Programmable Logic Controller) ladder logic is a good practice before making changes or conducting deeper investigations, it does not directly address the risk posed by scanning techniques. It’s more relevant to configuration management and recovery planning than to the initial assessment phase. CompTIA focuses on non-disruptive scanning methods as the primary concern when dealing with fragile systems.
Running scans during off-peak manufacturing hours:
Timing scans during off-peak hours may reduce operational impact, but it does not eliminate the risk of disrupting fragile or legacy equipment. Active scans can still cause failures regardless of timing. CompTIA recommends passive scanning as the safest approach, regardless of when the scan is performed. Timing is a secondary consideration compared to the scanning method itself.
Reference:
CompTIA CySA+ CS0-003 Official Study Guide
CompTIA CySA+ CS0-003 Exam Objectives – Domain 2.2: Implement vulnerability management activities
CompTIA CertMaster Learn for CySA+ CS0-003
Which of the following is the appropriate phase in the incident response process to perform a vulnerability scan to determine the effectiveness of corrective actions?
A. Lessons learned
B. Reporting
C. Recovery
D. Root cause analysis
Correct Answer:
Recovery Phase:
The Recovery phase of the incident response process is where systems and operations are brought back to a fully functional state after containment and eradication. It’s during this phase that a vulnerability scan should be conducted to ensure that:
All known vulnerabilities or exploited weaknesses have been effectively remediate
d
No remaining backdoors, malware, or misconfigurations exist
The system is safe to return to production
A post-remediation scan provides assurance that the corrective actions taken (patches, configurations, etc.) are effective and no additional vulnerabilities are present before restoring normal operations.
Key reason: Performing the scan during recovery helps validate that the environment is secure before resuming full operations, minimizing the risk of reinfection or repeated compromise.
Incorrect Answer Explanations:
Lessons Learned:
This is the final phase after the incident has been fully handled.
It involves reviewing what went well, what failed, and how to improve processes going forward.
No technical actions like scanning are typically performed here—just documentation and analysis.
Reporting:
Reporting involves documenting findings, impact, indicators of compromise (IOCs), and outcomes for internal and possibly external stakeholders.
It’s focused on communication and record-keeping, not technical validation of remediations.
Root Cause Analysis:
This phase aims to determine how and why the incident occurred, identifying the initial vector of compromise.
It is performed before recovery, typically during containment or eradication, and focuses on forensic analysis—not verifying fixes.
References:
NIST SP 800-61 Rev. 2 – Computer Security Incident Handling Guide
See Section 3.2: Recovery – includes validation and system monitoring.
CompTIA CySA+ (CS0-003) Objectives
Domain 4.3: Apply the appropriate incident response procedure or tool
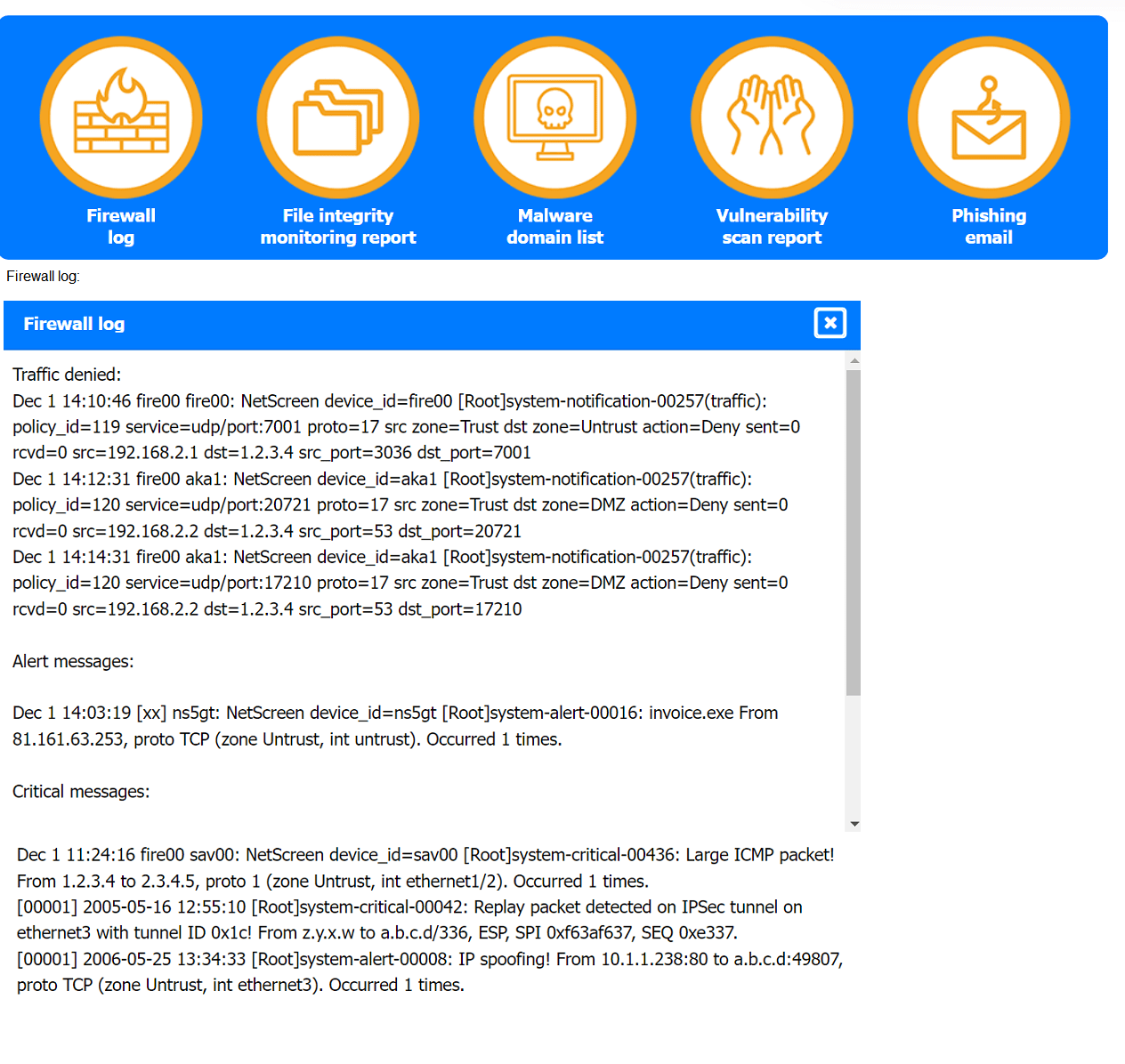
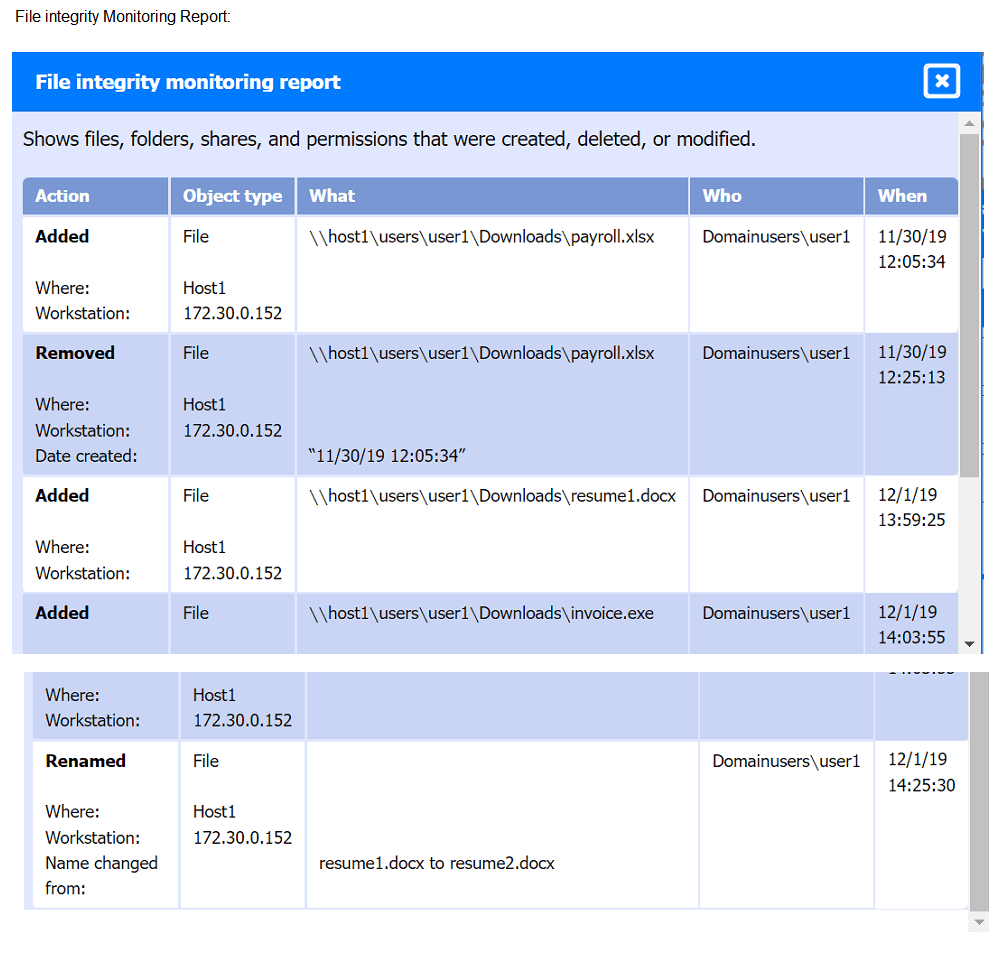
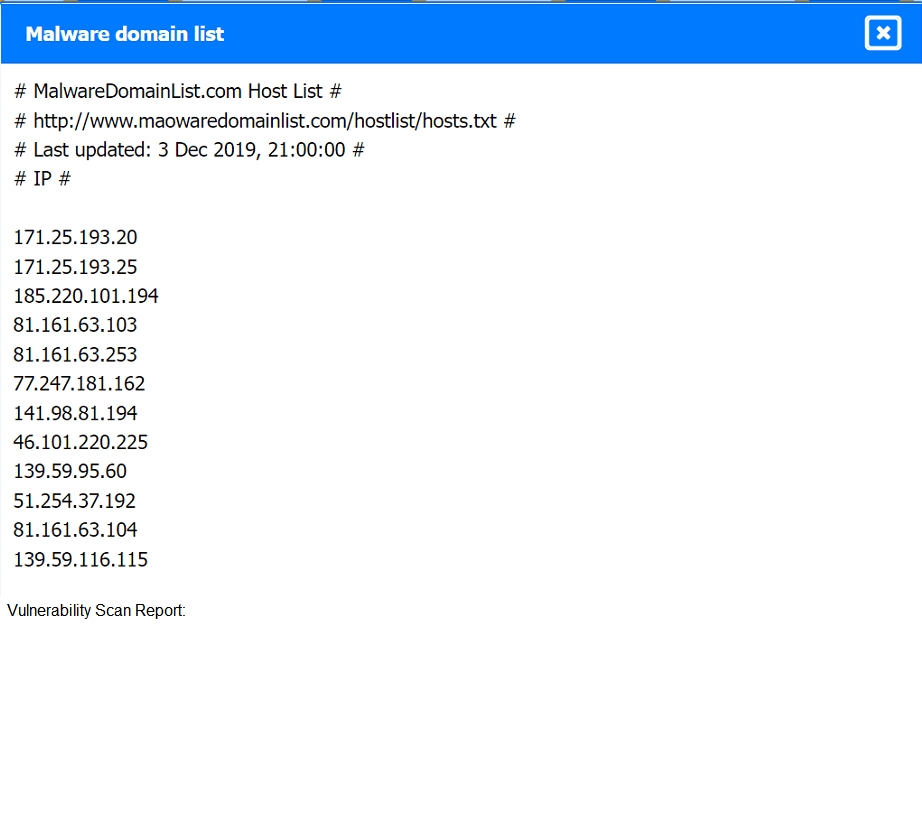
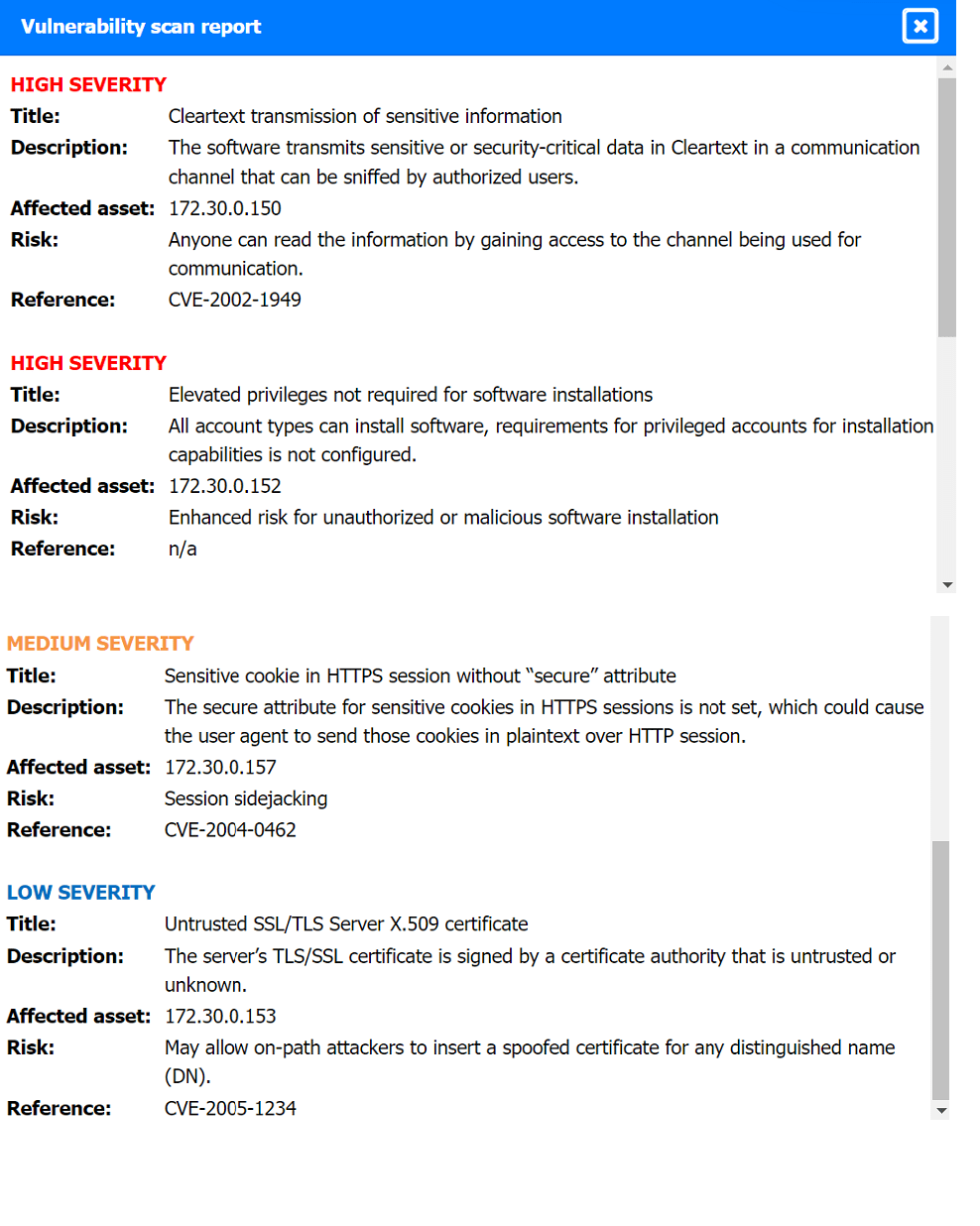
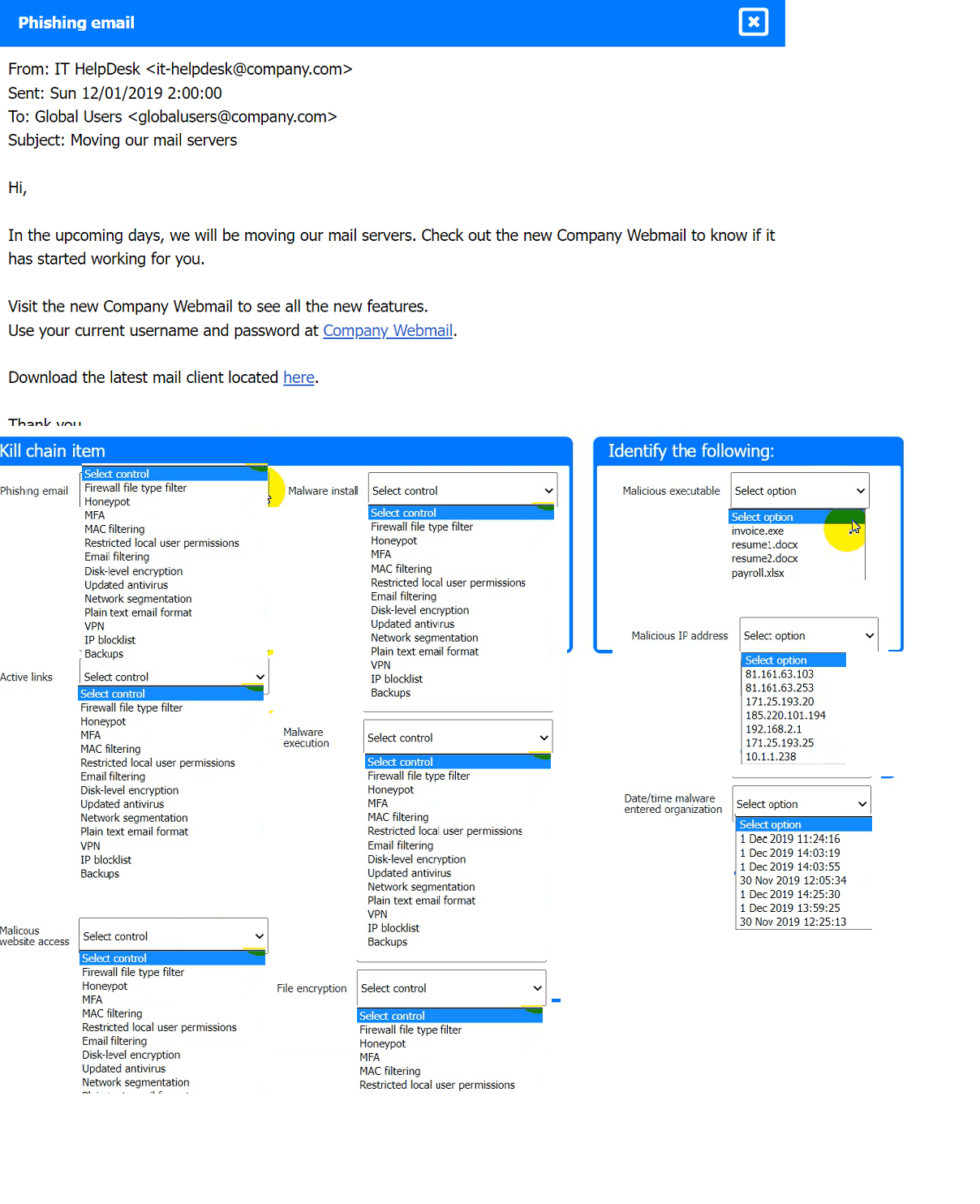
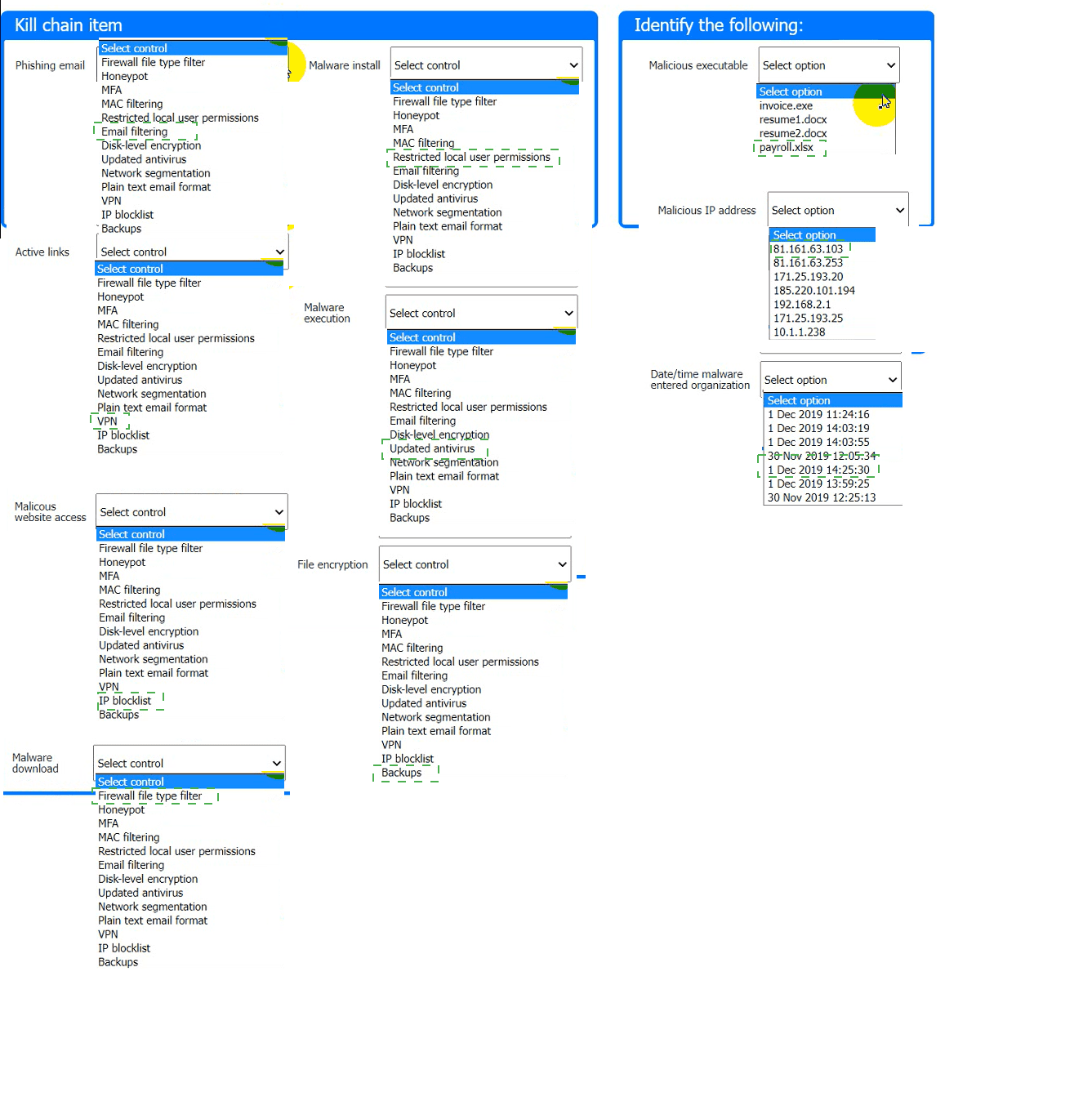
An analyst has received an IPS event notification from the SIEM stating an IP address, which is known to be malicious, has attempted to exploit a zero-day vulnerability on several web servers. The exploit contained the following snippet:
/wp-json/trx_addons/V2/get/sc_layout?sc=wp_insert_user&role=administrator
Which of the following controls would work best to mitigate the attack represented by this
snippet?
A. Limit user creation to administrators only.
B. Limit layout creation to administrators only.
C. Set the directory trx_addons to read only for all users.
D. Set the directory v2 to read only for all users.
Explanation:
The question is part of the Security Operations domain (33% weighting) of the CompTIA CySA+ (CS0-003) exam, aligning with Objective 1.3 (Analyze indicators of potentially malicious activity) and Objective 1.5 (Recommend process improvements to security operations). The scenario involves an Intrusion Prevention System (IPS) event notification in a Security Information and Event Management (SIEM) system, indicating a malicious IP attempting to exploit a zero-day vulnerability on web servers using the URL snippet /wp-json/trx_addons/v2/get/sc_layout?sc=wp_insert_user&role=administrator. This suggests an attempt to create an unauthorized administrator account via a WordPress plugin (trx_addons). The correct control must mitigate this specific attack, focusing on preventing unauthorized user creation, per CS0-003’s emphasis on mitigating exploits and NIST SP 800-53 guidelines.
Correct Answer:
Limit user creation to administrators only.
Limiting user creation to administrators only is the best control to mitigate the attack represented by the snippet /wp-json/trx_addons/v2/get/sc_layout?sc=wp_insert_user&role=administrator. The snippet attempts to exploit a zero-day vulnerability in the trx_addons WordPress plugin, specifically targeting the wp_insert_user function to create an administrator account. By restricting user creation (e.g., via WordPress settings or server-side controls) to only authorized administrators, the attack is blocked, as unauthorized attempts to invoke wp_insert_user will fail. This aligns with CS0-003 Objective 1.5, emphasizing process improvements to secure systems, and NIST SP 800-53 (AC-6), which advocates least privilege to prevent unauthorized access. For example, configuring WordPress to require admin authentication for user creation stops the exploit, regardless of the vulnerability’s specifics.
Incorrect Answers:
1)Limit layout creation to administrators only.
Limiting layout creation to administrators restricts access to the sc_layout parameter in the snippet, which relates to the trx_addons plugin’s layout functionality. However, the attack’s primary goal is to exploit the wp_insert_user function to create an administrator account, not to manipulate layouts. Restricting layout creation does not address the user creation vulnerability, allowing the exploit to succeed. For CS0-003 Objective 1.3, analyzing the snippet shows the attack targets user management, not layout functions. NIST SP 800-53 (AC-6) emphasizes controls specific to the threat, making user creation restrictions more effective than layout restrictions for this zero-day exploit.
2)Set the directory trx_addons to read only for all users.
Setting the trx_addons directory to read-only for all users could prevent modifications to the plugin’s files, such as unauthorized code injection. However, the snippet targets a web-based API endpoint (/wp-json/trx_addons/v2/get), not direct file system modifications. The zero-day exploit likely leverages a flaw in the plugin’s code execution, which read-only permissions on the directory won’t block, as the API processes requests dynamically. For CS0-003 Objective 1.5, file system permissions are relevant but not specific to this web-based attack. NIST SP 800-53 (SC-7) suggests application-level controls, like restricting user creation, are more effective than file permissions here.
3)Set the directory v2 to read only for all users.
Setting the v2 directory to read-only aims to restrict access to the API version path in the snippet (/wp-json/trx_addons/v2). However, this does not prevent the exploit, as the attack targets a vulnerability in the trx_addons plugin’s API processing (wp_insert_user), not file modifications in the v2 directory. Read-only settings on the directory won’t stop the API from executing malicious requests. For CS0-003 Objective 1.3, the snippet indicates a functional exploit, not a file write issue. NIST SP 800-53 (AC-6) prioritizes application-level controls, like limiting user creation, over directory permissions for this type of attack.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 1 (Security Operations), Objective 1.3 (Analyze indicators of potentially malicious activity) and Objective 1.5 (Recommend process improvements to security operations).
NIST SP 800-53: Security and Privacy Controls for Information Systems and Organizations, AC-6 (Least Privilege) and SC-7 (Boundary Protection).
Sybex CompTIA CySA+ Study Guide: Exam CS0-003 by Mike Chapple and David Seidl: Covers analyzing exploits and mitigation strategies.
Udemy: CompTIA CySA+ (CS0-003) Complete Course by Jason Dion: Discusses WordPress vulnerabilities and access control mitigations.
OWASP: Resources on securing WordPress plugins and APIs against unauthorized access.
Additional Notes:
Zero-Day Exploits: These are unpatched vulnerabilities, requiring immediate mitigation focused on the exploit’s impact (e.g., unauthorized user creation). CS0-003 tests this in PBQs involving log or snippet analysis.
WordPress Security: The wp-json API is a common attack vector. Restricting sensitive functions like wp_insert_user is a key defense, often tested in CS0-003 scenarios.
SIEM and IPS: The scenario highlights SIEM/IPS integration for detecting exploits, emphasizing the need to analyze IoCs (e.g., malicious IPs, URL patterns)
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve this issue?
A. Credentialed scan
B. External scan
C. Differential scan
D. Network scan
Correct Answer:
Credentialed Scan:
A credentialed scan uses valid credentials (such as SSH or Windows admin accounts) to log into systems and perform a deeper, more accurate assessment of vulnerabilities.
In this scenario, the vulnerability reports are incomplete, which strongly suggests that the current scans are non-credentialed (external or limited internal views), and therefore cannot access detailed system information like:
Installed patches
Software versions
Registry values (Windows)
Running services and configurations
By using credentialed scans, the scanner gains insider access—just like an administrator would—and can thoroughly evaluate the system. This results in more comprehensive findings in reports.
Use case: Ensures that the vulnerability scan has visibility into areas that require elevated access—eliminating blind spots that may lead to incomplete results.
Incorrect Answer:
External Scan:
Conducted outside the network (e.g., from the internet).
Only detects externally exposed vulnerabilities, such as open ports and outdated web servers.
Cannot detect internal misconfigurations or patch statuses.
Will result in limited findings compared to internal or credentialed scans.
Differential Scan:
Compares new scan results to previous results to show what changed.
Doesn’t increase scan depth or accuracy—it just highlights deltas.
If the base scan was incomplete, the differential scan will also be incomplete.
Network Scan:
A broad term that typically refers to scanning the network for hosts, open ports, and services.
It is not inherently credentialed and usually lacks depth regarding host-level vulnerabilities.
May identify devices and surface-level issues but miss internal vulnerabilities.
References:
NIST SP 800-115 – Technical Guide to Information Security Testing and Assessment See sections on credentialed vs non-credentialed scanning.
CompTIA CySA+ CS0-003 Exam Objective 2.3:
"Given a scenario, analyze output from security technologies including vulnerability scans..."
| Page 11 out of 45 Pages |
