CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 3: Exam Pool C
A security analyst found an old version of OpenSSH running on a DMZ server and
determined the following piece of code could have led to a command execution through an integer overflow;

Which of the following controls must be in place to prevent this vulnerability?
A.
Convert all integer numbers in strings to handle the memory buffer correctly.
B.
Implement float numbers instead of integers to prevent integer overflows.
C.
Use built-in functions from libraries to check and handle long numbers properly.
D.
Sanitize user inputs, avoiding small numbers that cannot be handled in the memory.
Use built-in functions from libraries to check and handle long numbers properly.
When attempting to do a stealth scan against a system that does not respond to ping,
which of the following Nmap commands BEST accomplishes that goal?
A.
nmap –sA –O <system> -noping
B.
nmap –sT –O <system> -P0
C.
nmap –sS –O <system> -P0
D.
nmap –sQ –O <system> -P0
nmap –sS –O <system> -P0
During the security assessment of a new application, a tester attempts to log in to the application but receives the following message incorrect password for given username.
Which of the following can the tester recommend to decrease the likelihood that a
malicious attacker will receive helpful information?
A.
Set the web page to redirect to an application support page when a bad password is entered.
B.
Disable error messaging for authentication
C.
Recognize that error messaging does not provide confirmation of the correct element of authentication
D.
Avoid using password-based authentication for the application
Disable error messaging for authentication
Which of me following BEST articulates the benefit of leveraging SCAP in an organization's
cybersecurity analysis toolset?
A.
It automatically performs remedial configuration changes lo enterprise security services
B.
It enables standard checklist and vulnerability analysis expressions for automaton
C.
It establishes a continuous integration environment for software development operations
D.
It provides validation of suspected system vulnerabilities through workflow orchestration
It enables standard checklist and vulnerability analysis expressions for automaton
The help desk noticed a security analyst that emails from a new email server are not being
sent out. The new email server was recently added to the existing ones. The analyst runs
the following command on the new server.
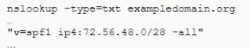
Given the output, which of the following should the security analyst check NEXT?
A.
The DNS name of the new email server
B.
The version of SPF that is being used
C.
The IP address of the new email server
D.
The DMARC policy
The DNS name of the new email server
An analyst is responding to an incident within a cloud infrastructure Based on the logs and
traffic analysis, the analyst thinks a container has been compromised Which of the
following should Ihe analyst do FIRST?
A.
Perform threat hunting in other areas of the cloud infrastructure
B.
Contact law enforcement to report the incident
C.
Perform a root cause analysis on the container and the service logs
D.
Isolate the container from production using a predefined policy template
Perform threat hunting in other areas of the cloud infrastructure
security analyst received an email with the following key:
Xj3XJ3LLc
A second security analyst received an email with following key:
3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key
that allows access to the company’s financial segment for maintenance. This is an example
of:
A.
dual control
B.
private key encryption
C.
separation of duties
D.
public key encryption
E.
two-factor authentication
dual control
An online gaming company was impacted by a ransomware attack. An employee opened
an attachment that was received via an SMS attack on a company-issue firewall. Which
following actions would help during the forensic analysis of the mobile device? (Select
TWO).
A.
Resetting the phone to factory settings
B.
Rebooting the phone and installing the latest security updates
C.
Documenting the respective chain of custody
D.
Uninstalling any potentially unwanted programs
E.
Performing a memory dump of the mobile device for analysis
F.
Unlocking the device by blowing the eFuse
Resetting the phone to factory settings
E.
Performing a memory dump of the mobile device for analysis
Which of the following sets of attributes BEST illustrates the characteristics of an insider
threat from a security perspective?
A.
Unauthorized, unintentional, benign
B.
Unauthorized, intentional, malicious
C.
Authorized, intentional, malicious
D.
Authorized, unintentional, benign
Authorized, intentional, malicious
A company is experiencing a malware attack within its network. A security engineer notices
many of the impacted assets are connecting outbound to a number of remote destinations
and exfiltrating data. The security engineer also see that deployed, up-to-date antivirus
signatures are ineffective. Which of the following is the BEST approach to prevent any
impact to the company from similar attacks in the future?
A.
IDS signatures
B.
Data loss prevention
C.
Port security
D.
Sinkholing
IDS signatures
| Page 9 out of 49 Pages |
| CS0-002 Practice Test | Previous |