CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
An organization wants to move non-essential services into a cloud computing environment.
Management has a cost focus and would like to achieve a recovery time objective of 12
hours. Which of the following cloud recovery strategies would work BEST to attain the
desired outcome?
A.
Duplicate all services in another instance and load balance between the instances
B.
Establish a hot site with active replication to another region within the same cloud
provider
C.
Set up a warm disaster recovery site with the same cloud provider in a different region
D.
Configure the systems with a cold site at another cloud provider that can be used for
failover.
Set up a warm disaster recovery site with the same cloud provider in a different region
A security analyst, who is working for a company that utilizes Linux servers, receives the
following results from a vulnerability scan:
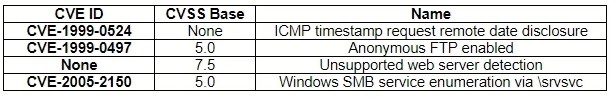
Which of the following is MOST likely a false positive?
A.
ICMP timestamp request remote date disclosure
B.
Windows SMB service enumeration via \srvsvc
C.
Anonymous FTP enabled
D.
Unsupported web server detection
Windows SMB service enumeration via \srvsvc
A web developer wants to create a new web part within the company website that
aggregates sales from individual team sites. A cybersecurity analyst wants to ensure
security measurements are implemented during this process. Which of the following
remediation actions should the analyst take to implement a vulnerability management
process?
A.
Personnel training
B.
Vulnerability scan
C.
Change management
D.
Sandboxing
Change management
Which of the following would a security engineer recommend to BEST protect sensitive
system data from being accessed on mobile devices?
A.
Use a UEFl boot password.
B.
Implement a self-encrypted disk
C.
Configure filesystem encryption
D.
Enable Secure Boot using TPM
Configure filesystem encryption
A security analyst is reviewing the following web server log:
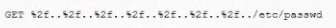
Which of the following BEST describes the issue?
A.
Directory traversal exploit
B.
Cross-site scripting
C.
SQL injection
D.
Cross-site request forgery
Directory traversal exploit
An analyst performs a routine scan of a host using Nmap and receives the following output:
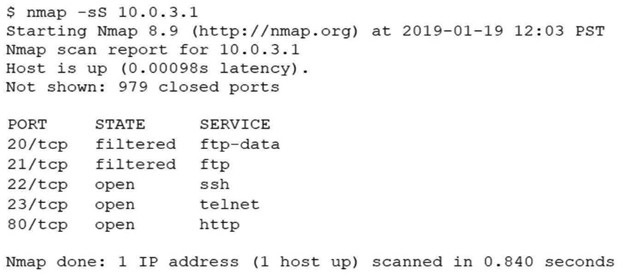
Which of the following should the analyst investigate FIRST?
A.
Port 21
B.
Port 22
C.
Port 23
D.
Port 80
Port 21
A user's computer has been running slowly when the user tries to access web pages. A
security analyst runs the command netstat -aon from the command line and receives the
following output:
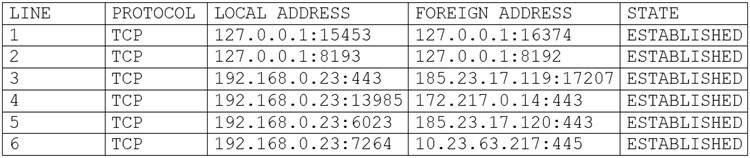
Which of the following lines indicates the computer may be compromised?
A.
Line 1
B.
Line 2
C.
Line 3
D.
Line 4
E.
Line 5
F.
Line 6
Line 4
An information security analyst observes anomalous behavior on the SCADA devices in a
power plant. This behavior results in the industrial generators overheating and destabilizing
the power supply.
Which of the following would BEST identify potential indicators of compromise?
A.
Use Burp Suite to capture packets to the SCADA device's IP.
B.
Use tcpdump to capture packets from the SCADA device IP.
C.
Use Wireshark to capture packets between SCADA devices and the management
system.
D.
Use Nmap to capture packets from the management system to the SCADA devices.
Use Wireshark to capture packets between SCADA devices and the management
system.
A company recently experienced a break-in whereby a number of hardware assets were
stolen through unauthorized access at the back of the building. Which of the following
would BEST prevent this type of theft from occurring in the future?
A.
Motion detection
B.
Perimeter fencing
C.
Monitored security cameras
D.
Badged entry
Motion detection
A security analyst is reviewing packet captures from a system that was compromised. The
system was already isolated from the network, but it did have network access for a few
hours after being compromised. When viewing the capture in a packet analyzer, the analyst
sees the following:

Which of the following can the analyst conclude?
A.
Malware is attempting to beacon to 128.50.100.3.
B.
The system is running a DoS attack against ajgidwle.com
C.
The system is scanning ajgidwle.com for PII.
D.
Data is being exfiltrated over DNS.
Data is being exfiltrated over DNS.
| Page 1 out of 49 Pages |