CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
After receiving reports latency, a security analyst performs an Nmap scan and observes the
following output:
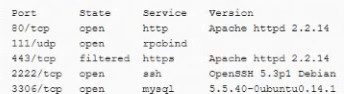
Which of the following suggests the system that produced output was compromised?
A.
Secure shell is operating of compromise on this system
B.
There are no indicators of compromise on this system
C.
MySQL services is identified on a standard PostgreSQL port
D.
Standard HTP is open on the system and should be closed
Secure shell is operating of compromise on this system
A cybersecurity analyst is responding to an incident. The company’s leadership team wants
to attribute the incident to an attack group. Which of the following models would BEST
apply to the situation?
A.
Intelligence cycle
B.
Diamond Model of Intrusion Analysis
C.
Kill chain
D.
MITRE ATT&CK
Diamond Model of Intrusion Analysis
A Chief Information Security Officer (CISO) wants to upgrade an organization's security
posture by improving proactive activities associated with attacks from internal and external
threats.
Which of the following is the MOST proactive tool or technique that feeds incident response
capabilities?
A.
Development of a hypothesis as part of threat hunting
B.
Log correlation, monitoring, and automated reporting through a SIEM platform
C.
Continuous compliance monitoring using SCAP dashboards
D.
Quarterly vulnerability scanning using credentialed scans
Development of a hypothesis as part of threat hunting
A security analyst has observed several incidents within an organization that are affecting
one specific piece of hardware on the network. Further investigation reveals the equipment
vendor previously released a patch.
Which of the following is the MOST appropriate threat classification for these incidents?
A.
Known threat
B.
Zero day
C.
Unknown threat
D.
Advanced persistent threat
Advanced persistent threat
An organization has not had an incident for several month. The Chief information Security
Officer (CISO) wants to move to proactive stance for security investigations. Which of the
following would BEST meet that goal?
A.
Root-cause analysis
B.
Active response
C.
Advanced antivirus
D.
Information-sharing community
E.
Threat hunting
Threat hunting
A security analyst is reviewing the following log from an email security service.
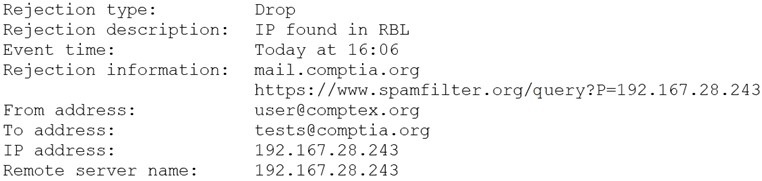
Which of the following BEST describes the reason why the email was blocked?
A.
The To address is invalid
B.
The email originated from the www.spamfilter.org URL
C.
The IP address and the remote server name are the same
D.
The IP address was blacklisted
E.
The From address is invalid
The IP address and the remote server name are the same
An analyst is investigating an anomalous event reported by the SOC. After reviewing the
system logs the analyst identifies an unexpected addition of a user with root-level privileges
on the endpoint. Which of the following data sources will BEST help the analyst to
determine whether this event constitutes an incident?
A.
Patching logs
B.
Threat feed
C.
Backup logs
D.
Change requests
E.
Data classification matrix
Change requests
A Chief Information Security Officer (CISO) is concerned the development team, which
consists of contractors, has too much access to customer datA. Developers use personal
workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO's concern?
A.
DLP
B.
Encryption
C.
Test data
D.
NDA
NDA
A security analyst is investigating malicious traffic from an internal system that attempted to
download proxy avoidance software as identified from the firewall logs but the destination
IP is blocked and not captured. Which of the following should the analyst do?
A.
Shut down the computer
B.
Capture live data using Wireshark
C.
Take a snapshot
D.
Determine if DNS logging is enabled.
E.
Review the network logs
Determine if DNS logging is enabled.
Explanation: The DNS debug log provides extremely detailed data about all DNS
information that is sent and received by the DNS server, similar to the data that can be
gathered using packet capture tools such as network monitor.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-
r2-and-
2012/dn800669(v=ws.11)#:~:text=The-DNS-debug-log-provides,tools-su
ch-as-network-monitor.
An organization needs to limit its exposure to accidental disclosure when employees send
emails that contain personal information to recipients outside the company Which of the
following technical controls would BEST accomplish this goal?
A.
DLP
B.
Encryption
C.
Data masking
D.
SPF
Data masking
| Page 2 out of 49 Pages |
| CS0-002 Practice Test |