CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
A company wants to establish a threat-hunting team. Which of the following BEST
describes the rationale for integration intelligence into hunt operations?
A.
It enables the team to prioritize the focus area and tactics within the company’s
environment.
B.
It provide critically analyses for key enterprise servers and services.
C.
It allow analysis to receive updates on newly discovered software vulnerabilities.
D.
It supports rapid response and recovery during and followed an incident.
It enables the team to prioritize the focus area and tactics within the company’s
environment.
Which of the following is the use of tools to simulate the ability for an attacker to gain
access to a specified network?
A.
Reverse engineering
B.
Fuzzing
C.
Penetration testing
D.
Network mapping
Penetration testing
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities The type
of vulnerability that should be disseminated FIRST is one that:
A.
enables remote code execution that is being exploited in the wild.
B.
enables data leakage but is not known to be in the environment
C.
enables lateral movement and was reported as a proof of concept
D.
affected the organization in the past but was probably contained and eradicated
enables lateral movement and was reported as a proof of concept
A security analyst on the threat-hunting team has developed a list of unneeded, benign
services that are currently running as part of the standard OS deployment for workstations.
The analyst will provide this list to the operations team to create a policy that will
automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
A.
To create a system baseline
B.
To reduce the attack surface
C.
To optimize system performance
D.
To improve malware detection
To reduce the attack surface
Which of the following attacks can be prevented by using output encoding?
A.
Server-side request forgery
B.
Cross-site scripting
C.
SQL injection
D.
Command injection
E.
Cross-site request forgery
F.
Directory traversal
Cross-site scripting
An employee in the billing department accidentally sent a spreadsheet containing payment
card data to a recipient outside the organization The employee intended to send the
spreadsheet to an internal staff member with a similar name and was unaware of the
mistake until the recipient replied to the message In addition to retraining the employee,
which of the following would prevent this from happening in the future?
A.
Implement outgoing filter rules to quarantine messages that contain card data
B.
Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
C.
Remove all external recipients from the employee's address book
D.
Set the outgoing mail filter to strip spreadsheet attachments from all messages.
Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
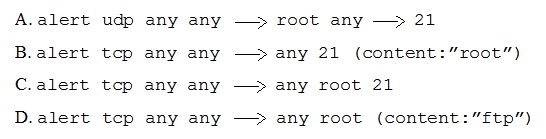
A security administrator needs to create an IDS rule to alert on FTP login attempts by root.
Which of the following rules is the BEST solution?
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option B
An analyst is performing penetration testing and vulnerability assessment activities against
a new vehicle automation platform.
Which of the following is MOST likely an attack vector that is being utilized as part of the
testing and assessment?
A.
FaaS
B.
RTOS
C.
SoC
D.
GPS
E.
CAN bus
CAN bus
A security analyst is reviewing a firewall usage report that contains traffic generated over
the last 30 minutes in order to locate unusual traffic patterns:
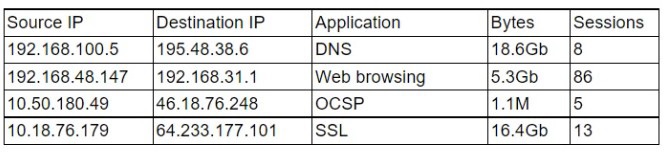
Which of the following source IP addresses does the analyst need to investigate further?
A.
10.18.76.179
B.
10.50.180.49
C.
192.168.48.147
D.
192.168.100.5
192.168.48.147
An information security analyst is reviewing backup data sets as part of a project focused
on eliminating archival data sets.
Which of the following should be considered FIRST prior to disposing of the electronic
data?
A.
Sanitization policy
B.
Data sovereignty
C.
Encryption policy
D.
Retention standards
Retention standards
| Page 6 out of 49 Pages |
| CS0-002 Practice Test | Previous |