CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
During an incident, a cybersecurity analyst found several entries in the web server logs that
are related to an IP with a bad reputation . Which of the following would cause the analyst
to further review the incident?
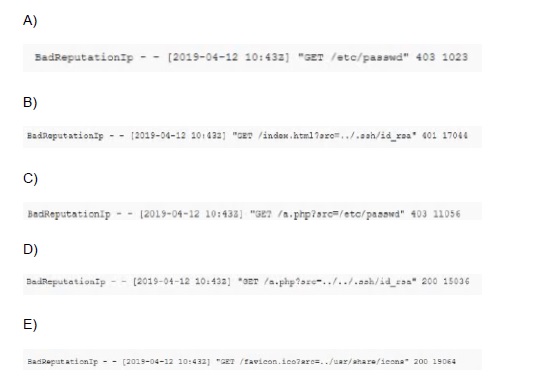
A.
Option A
B.
Option B
C.
Option C
D.
Option D
E.
Option E
Option D
A security analyst discovered a specific series of IP addresses that are targeting an
organization. None of the attacks have been successful. Which of the following should the
security analyst perform NEXT?
A.
Begin blocking all IP addresses within that subnet
B.
Determine the attack vector and total attack surface.
C.
Begin a kill chain analysis to determine the impact
D.
Conduct threat research on the IP addresses
Conduct threat research on the IP addresses
Which of the following technologies can be used to house the entropy keys for disk
encryption on desktops and laptops?
A.
Self-encrypting drive
B.
Bus encryption
C.
TPM
D.
HSM
Self-encrypting drive
A developer wrote a script to make names and other Pll data unidentifiable before loading a
database export into the testing system Which of the following describes the type of control
that is being used?
A.
Data encoding
B.
Data masking
C.
Data loss prevention
D.
Data classification
Data loss prevention
A security analyst has discovered suspicious traffic and determined a host is connecting to
a known malicious website. The MOST appropriate action for the analyst to take would be
lo implement a change request to:
A.
update the antivirus software
B.
configure the firewall to block traffic to the domain
C.
add the domain to the blacklist
D.
create an IPS signature for the domain
configure the firewall to block traffic to the domain
A team of security analysis has been alerted to potential malware activity. The initial
examination indicates one of the affected workstations on beaconing on TCP port 80 to five
IP addresses and attempting to spread across the network over port 445. Which of the
following should be the team's NEXT step during the detection phase of this response
process?
A.
Escalate the incident to management ,who will then engage the network infrastructure
team to keep them informed
B.
Depending on system critically remove each affected device from the network by
disabling wired and wireless connections
C.
Engage the engineering team to block SMB traffic internally and outbound HTTP traffic
to the five IP addresses Identify potentially affected systems by creating a correlation
D.
Identify potentially affected system by creating a correlation search in the SIEM based
on the network traffic.
Identify potentially affected system by creating a correlation search in the SIEM based
on the network traffic.
A security analyst is conducting a post-incident log analysis to determine which indicators
can be used to detect further occurrences of a data exfiltration incident. The analyst
determines backups were not performed during this time and reviews the following:
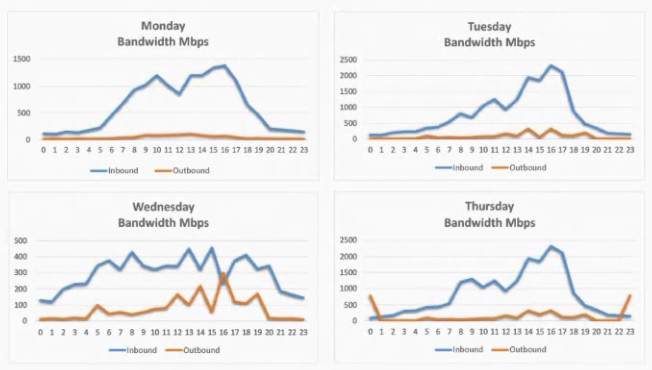
Which of the following should the analyst review to find out how the data was exfilltrated?
A.
Monday's logs
B.
Tuesday's logs
C.
Wednesday's logs
D.
Thursday's logs
Thursday's logs
A large amount of confidential data was leaked during a recent security breach. As part of a
forensic investigation, the security team needs to identify the various types of traffic that
were captured between two
compromised devices.
Which of the following should be used to identify the traffic?
A.
Carving
B.
Disk imaging
C.
Packet analysis
D.
Memory dump
E.
Hashing
Packet analysis
A security analyst gathered forensics from a recent intrusion in preparation for legal
proceedings. The analyst used EnCase to gather the digital forensics. cloned the hard
drive, and took the hard drive home for further analysis. Which of the following of the
security analyst violate?
A.
Cloning procedures
B.
Chain of custody
C.
Hashing procedures
D.
Virtualization
Chain of custody
A development team signed a contract that requires access to an on-premises physical
server. Access must be restricted to authorized users only and cannot be connected to the
Internet.
Which of the following solutions would meet this requirement?
A.
Establish a hosted SSO
B.
Implement a CASB
C.
Virtualize the server
D.
Air gap the server
Air gap the server
| Page 4 out of 49 Pages |
| CS0-002 Practice Test | Previous |