CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
An organization is moving its infrastructure to the cloud in an effort to meet the budget and
reduce staffing requirements. The organization has three environments: development,
testing, and production. These environments have interdependencies but must remain
relatively segmented.
Which of the following methods would BEST secure the company's infrastructure and be
the simplest to manage and maintain?
A.
Create three separate cloud accounts for each environment. Configure account peering
and security rules to allow access to and from each environment
B.
Create one cloud account with one VPC for all environments. Purchase a virtual firewall
and create granular security rules
C.
Create one cloud account and three separate VPCs for each environment. Create
security rules to allow access to and from each environment
D.
Create three separate cloud accounts for each environment and a single core account
for network services. Route all traffic through the core account
Create one cloud account and three separate VPCs for each environment. Create
security rules to allow access to and from each environment
Bootloader malware was recently discovered on several company workstations. All the
workstations run Windows and are current models with UEFI capability.
Which of the following UEFI settings is the MOST likely cause of the infections?
A.
Compatibility mode
B.
Secure boot mode
C.
Native mode
D.
Fast boot mode
Compatibility mode
A security analyst needs to assess the web server versions on a list of hosts to determine
which are running a vulnerable version of the software and output that list into an XML file
named webserverlist.xml. The host list is provided in a file named webserverlist.txt. Which
of the following Nmap commands would BEST accomplish this goal?
A.
nmap -iL webserverlist.txt -sC -p 443 -oX webserverlist.xml
B.
nmap -iL webserverlist.txt -sV -p 443 -oX webserverlist.xml
C.
nmap -iL webserverlist.txt -F -p 443 -oX webserverlist.xml
D.
nmap --takefile webserverlist.txt --outputfileasXML webserverlist.xml –scanports 443
nmap -iL webserverlist.txt -sV -p 443 -oX webserverlist.xml
A pharmaceutical company's marketing team wants to send out notifications about new
products to alert users of recalls and newly discovered adverse drug reactions. The team
plans to use the names and mailing addresses that users have provided.
Which of the following data privacy standards does this violate?
A.
Purpose limitation
B.
Sovereignty
C.
Data minimization
D.
Retention
Purpose limitation
A security analyst is supporting an embedded software team. Which of the following is the
BEST recommendation to ensure proper error handling at runtime?
A.
Perform static code analysis
B.
Require application fuzzing.
C.
Enforce input validation
D.
Perform a code review
Require application fuzzing.
A small electronics company decides to use a contractor to assist with the development of
a new FPGA-based device. Several of the development phases will occur off-site at the
contractor's labs.
Which of the following is the main concern a security analyst should have with this
arrangement?
A.
Making multiple trips between development sites increases the chance of physical damage to the FPGAs
B.
Moving the FPGAs between development sites will lessen the time that is available for
security testing.
C.
Development phases occurring at multiple sites may produce change management
issues.
D.
FPGA applications are easily cloned, increasing the possibility of intellectual property
theft.
FPGA applications are easily cloned, increasing the possibility of intellectual property
theft.
A security technician is testing a solution that will prevent outside entities from spoofing the
company's email domain, which is comptiA.org. The testing is successful, and the security
technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
A.
Add TXT @ "v=spf1 mx include:_spf.comptiA.org all" to the DNS record.
B.
Add TXT @ "v=spf1 mx include:_spf.comptiA.org all" to the email server
C.
Add TXT @ "v=spf1 mx include:_spf.comptiA.org +all" to the domain controller
D.
Add TXT @ "v=spf1 mx include:_spf.comptiA.org +all" to the web server
Add TXT @ "v=spf1 mx include:_spf.comptiA.org all" to the DNS record.
A security analyst is evaluating two vulnerability management tools for possible use in an
organization. The analyst set up each of the tools according to the respective vendor's
instructions and generated a report of vulnerabilities that ran against the same target
server.
Tool A reported the following:
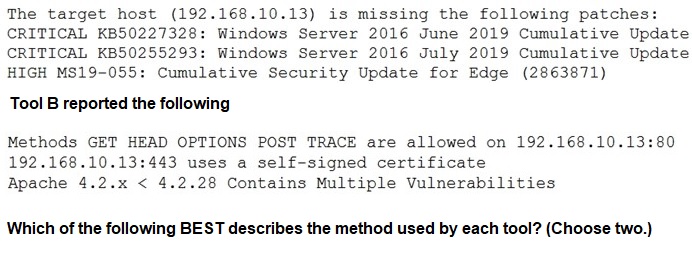
A.
Tool A is agent based.
B.
Tool A used fuzzing logic to test vulnerabilities
C.
Tool A is unauthenticated.
D.
Tool B utilized machine learning technology
E.
Tool B is agent based.
F.
Tool B is unauthenticated.
Tool A is unauthenticated.
E.
Tool B is agent based.
An organization that handles sensitive financial information wants to perform tokenization
of data to enable the execution of recurring transactions. The organization is most
interested m a secure, built-in device to support its solution. Which of the following would
MOST likely be required to perform the desired function?
A.
TPM
B.
eFuse
C.
FPGA
D.
HSM
E.
UEFI
HSM
A security analyst receives an alert that highly sensitive information has left the company's network Upon investigation, the analyst discovers an outside IP range has had connections
from three servers more than 100 times m the past month The affected servers are virtual
machines Which of the following is the BEST course of action?
A.
Shut down the servers as soon as possible, move them to a clean environment, restart,
run a vulnerability scanner to find weaknesses determine the root cause, remediate, and
report
B.
Report the data exfiltration to management take the affected servers offline, conduct an
antivirus scan, remediate all threats found, and return the servers to service.
C.
Disconnect the affected servers from the network, use the virtual machine console to
access the systems, determine which information has left the network, find the security
weakness, and remediate
D.
Determine if any other servers have been affected, snapshot any servers found,
determine the vector that was used to allow the data exfiltration. fix any vulnerabilities,
remediate, and report.
Shut down the servers as soon as possible, move them to a clean environment, restart,
run a vulnerability scanner to find weaknesses determine the root cause, remediate, and
report
| Page 3 out of 49 Pages |
| CS0-002 Practice Test | Previous |