CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
After a breach involving the exfiltration of a large amount of sensitive data a security
analyst is reviewing the following firewall logs to determine how the breach occurred:
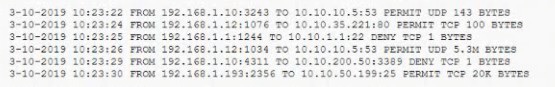
Which of the following IP addresses does the analyst need to investigate further?
A.
192.168.1.1
B.
192.168.1.10
C.
192.168.1.12
D.
192.168.1.193
192.168.1.12
A development team is testing a new application release. The team needs to import
existing client PHI data records from the production environment to the test environment to
test accuracy and functionality.
Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
A.
Deidentification
B.
Encoding
C.
Encryption
D.
Watermarking
Deidentification
A company stores all of its data in the cloud. All company-owned laptops are currently
unmanaged, and all users have administrative rights. The security team is having difficulty
identifying a way to secure the environment. Which of the following would be the BEST
method to protect the company's data?
A.
Implement UEM on an systems and deploy security software.
B.
Implement DLP on all workstations and block company data from being sent outside the company
C.
Implement a CASB and prevent certain types of data from being downloaded to a
workstation
D.
Implement centralized monitoring and logging for an company systems.
Implement a CASB and prevent certain types of data from being downloaded to a
workstation
A security analyst recently discovered two unauthorized hosts on the campus's wireless
network segment from a man-m-the-middle attack .The security analyst also verified that
privileges were not escalated, and the two devices did not gain access to other network
devices Which of the following would BEST mitigate and improve the security posture of
the wireless network for this type of attack?
A.
Enable MAC filtering on the wireless router and suggest a stronger encryption for the
wireless network,
B.
Change the SSID, strengthen the passcode, and implement MAC filtering on the
wireless router.
C.
Enable MAC filtering on the wireless router and create a whitelist that allows devices on
the network
D.
Conduct a wireless survey to determine if the wireless strength needs to be reduced.
Enable MAC filtering on the wireless router and suggest a stronger encryption for the
wireless network,
A network attack that is exploiting a vulnerability in the SNMP is detected.
Which of the following should the cybersecurity analyst do FIRST?
A.
Apply the required patches to remediate the vulnerability
B.
Escalate the incident to senior management for guidance
C.
Disable all privileged user accounts on the network
D.
Temporarily block the attacking IP address
Apply the required patches to remediate the vulnerability
An analyst determines a security incident has occurred Which of the following is the most appropnate NEXT step in an incident response plan?
A.
Consult the malware analysis process
B.
Consult the disaster recovery plan
C.
Consult the data classification process
D.
Consult the communications plan
Consult the communications plan
A new vanant of malware is spreading on ihe company network using TCP 443 to contact
its command-and-control server The domain name used for callback continues to change,
and the analyst is unable to predict future domain name variance Which of the following
actions should the analyst take to stop malicious communications with the LEAST
disruption to service?
A.
Implement a sinkhole with a high entropy level
B.
Disable TCP/53 at the penmeter firewall
C.
Block TCP/443 at the edge router
D.
Configure the DNS forwarders to use recursion
Configure the DNS forwarders to use recursion
Which of the following BEST articulates the benefit of leveraging SCAP in an organization’s
cybersecurity analysis toolset?
A.
It automatically performs remedial configuration changes to enterprise security services
B.
It enables standard checklist and vulnerability analysis expressions for automation
C.
It establishes a continuous integration environment for software development operations
D.
It provides validation of suspected system vulnerabilities through workflow orchestration
It enables standard checklist and vulnerability analysis expressions for automation
A company offers a hardware security appliance to customers that provides remote
administration of a device on the customer's network Customers are not authorized to alter
the configuration The company deployed a software process to manage unauthorized
changes to the appliance log them, and forward them to a central repository for evaluation
Which of the following processes is the company using to ensure the appliance is not
altered from its ongmal configured state?
A.
CI/CD
B.
Software assurance
C.
Anti-tamper
D.
Change management
Change management
The help desk provided a security analyst with a screenshot of a user's desktop:

For which of the following is aircrack-ng being used?
A.
Wireless access point discovery
B.
Rainbow attack
C.
Brute-force attack
D.
PCAP data collection
Rainbow attack
| Page 11 out of 49 Pages |
| CS0-002 Practice Test | Previous |