CompTIA CS0-002 Practice Test
Prepare smarter and boost your chances of success with our CompTIA CS0-002 Practice test. This test helps you assess your knowledge, pinpoint strengths, and target areas for improvement. Surveys and user data from multiple platforms show that individuals who use CS0-002 practice exam are 40–50% more likely to pass on their first attempt.
Start practicing today and take the fast track to becoming CompTIA CS0-002 certified.
14830 already prepared
Updated On :483 Questions
4.8/5.0
Topic 1: Exam Pool A
Which of the following BEST describes the process by which code is developed, tested,
and deployed in small batches?
A.
Agile
B.
Waterfall
C.
SDLC
D.
Dynamic code analysis
Agile
Reference: https://www.cleverism.com/software-development-life-cycle-sdlcmethodologies/
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application, the user is redirected to the login page. After successful
authentication, the user is then redirected
back to the original page. Some users have reported receiving phishing emails with a link
that takes them to the application login page but then redirects to a fake login page after
successful authentication.
Which of the following will remediate this software vulnerability?
A.
Enforce unique session IDs for the application.
B.
Deploy a WAF in front of the web application.
C.
Check for and enforce the proper domain for the redirect
D.
Use a parameterized query to check the credentials.
E.
Implement email filtering with anti-phishing protection
Check for and enforce the proper domain for the redirect
A company's modem response team is handling a threat that was identified on the network
Security analysts have as at remote sites. Which of the following is the MOST appropriate
next step in the incident response plan?
A.
Quarantine the web server
B.
Deploy virtual firewalls
C.
Capture a forensic image of the memory and disk
D.
Enable web server containerization
Deploy virtual firewalls
You are a cybersecurity analyst tasked with interpreting scan data from Company A's
servers. You must verify the requirements are being met for all of the servers and
recommend changes if you find they are not.
The company's hardening guidelines indicate the following:
- TLS 1.2 is the only version of TLS running.
• Apache 2.4.18 or greater should be used.
• Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for
each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make
recommendations for issues based ONLY on the hardening guidelines provided.
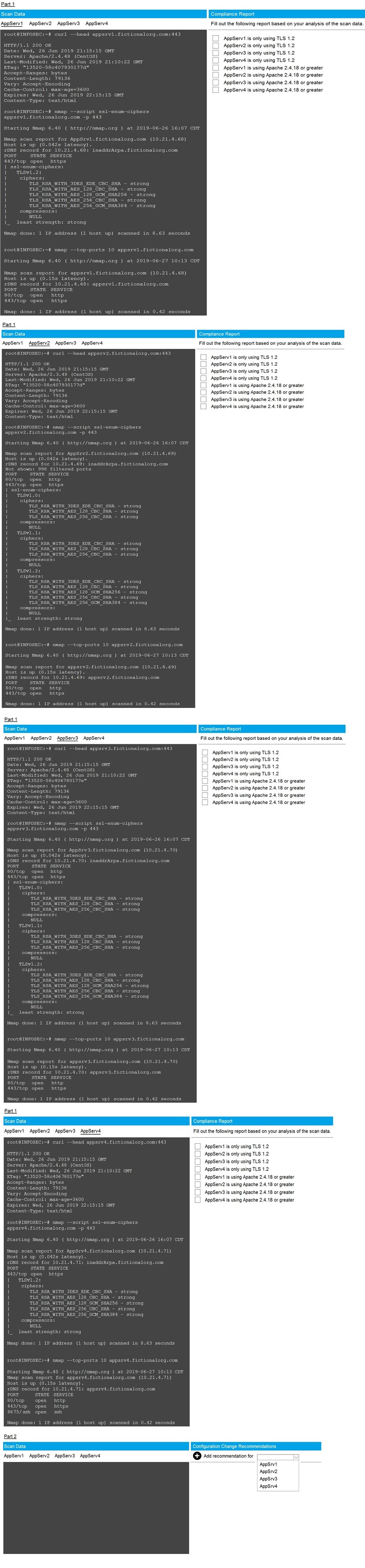
Part 1 Answer:
Check on the following:
AppServ1 is only using TLS.1.2
AppServ4 is only using TLS.1.2
AppServ1 is using Apache 2.4.18 or greater
AppServ3 is using Apache 2.4.18 or greater
AppServ4 is using Apache 2.4.18 or greater
Part 2 answer:
Recommendation:
Recommendation is to disable TLS v1.1 on AppServ2 and AppServ3. Also upgrade
AppServ2 Apache to version 2.4.48 from its current version of 2.3.48

A security analyst wants to identify which vulnerabilities a potential attacker might initially exploit if the network is compromised Which of the following would provide the BEST
results?
A.
Baseline configuration assessment
B.
Uncredentialed scan
C.
Network ping sweep
D.
External penetration test
External penetration test
A hybrid control is one that:
A.
is implemented differently on individual systems
B.
is implemented at the enterprise and system levels
C.
has operational and technical components
D.
authenticates using passwords and hardware tokens
is implemented at the enterprise and system levels
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:

The analyst accesses the server console, and the following console messages are
displayed:
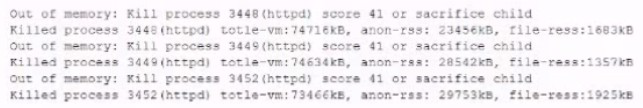
The analyst is also unable to log in on the console. While reviewing network captures for
the server, the analyst sees many packets with the following signature:
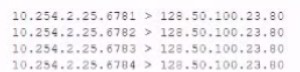
Which of the following is the BEST step for the analyst to lake next in this situation?
A.
Load the network captures into a protocol analyzer to further investigate the
communication with 128.30.100.23, as this may be a botnet command server
B.
After ensuring network captures from the server are saved isolate the server from the
network take a memory snapshot, reboot and log in to do further analysis.
C.
Corporate data is being exfilltrated from the server Reboot the server and log in to see if
it contains any sensitive data.
D.
Cryptomining malware is running on the server and utilizing an CPU and memory.
Reboot the server and disable any cron Jobs or startup scripts that start the mining
software.
Load the network captures into a protocol analyzer to further investigate the
communication with 128.30.100.23, as this may be a botnet command server
Which of the following roles is ultimately responsible for determining the classification
levels assigned to specific data sets?
A.
Data custodian
B.
Data owner
C.
Data processor
D.
Senior management
Data owner
A security analyst working in the SOC recently discovered Balances m which hosts visited
a specific set of domains and IPs and became infected with malware. Which of the
following is the MOST appropriate action to take in the situation?
A.
implement an IPS signature for the malware and update the blacklisting for the
associated domains and IPs
B.
Implement an IPS signature for the malware and another signature request to Nock all
the associated domains and IPs
C.
Implement a change request to the firewall setting to not allow traffic to and from the IPs
and domains
D.
Implement an IPS signature for the malware and a change request to the firewall setting
to not allow traffic to and from the IPs and domains
Implement a change request to the firewall setting to not allow traffic to and from the IPs
and domains
A security analyst is investigate an no client related to an alert from the threat detection platform on a host (10.0 1.25) in a staging environment that could be running a cryptomining tool because it in sending traffic to an IP address that are related to Bitcoin.
The network rules for the instance are the following:
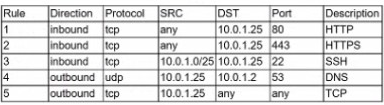
Which of the following is the BEST way to isolate and triage the host?
A.
Remove rules 1.2. and 3.
B.
Remove rules 1.2. 4. and 5.
C.
Remove rules 1.2. 3.4. and 5.
D.
Remove rules 1.2. and 5.
E.
Remove rules 1.4. and 5.
F.
Remove rules 4 and 5
Remove rules 1.2. and 5.
| Page 10 out of 49 Pages |
| CS0-002 Practice Test | Previous |