An employee is trying to connect their company laptop to an airport’s Wi-Fi during a business trip. Once the network is connected, a pop-up window appears with the airport logo, which the employee quickly closes. The internet connection is not working properly. Which of the following should a help desk technician suggest?
A. Look for a wall socket with RJ45 and try to connect the laptop to it
B. Contact the airport IT department
C. Tell the employee that company policy prohibits connection to public Wi-Fi
D. Reconnect to the network and read the pop-up carefully
Explanation:
✅ Correct Answer (D. Reconnect to the network and read the pop-up carefully):
The pop-up window is a captive portal requiring users to accept terms or enter credentials to gain full internet access. Closing it prematurely prevents proper authentication, causing connectivity failure. Advising the user to reconnect and follow the prompts ensures successful network access.
❌ Incorrect Answers:
A. Look for a wall socket with RJ45 and try to connect the laptop to it:
This is impractical in an airport and unnecessary if Wi-Fi is available.
B. Contact the airport IT department:
While possible, it’s usually faster and easier for users to follow the captive portal steps themselves.
C. Tell the employee that company policy prohibits connection to public Wi-Fi:
No such policy was mentioned, and this does not solve the connectivity problem.
A technician installs a Bluetooth headset for a user. During testing, the sound still comes from the speaker on the computer. The technician verifies the headset shows up in Device Manager. Which of the following would the technician most likely do to fix this issue?
A. Update the drivers for the wireless headset
B. Replace the battery on the headset and try again later
C. Verify that the sound is not muted in the control panel
D. Change the headset as the default device in sound settings
Explanation:
✅ Correct Answer (D. Change the headset as the default device in sound settings):
If the Bluetooth headset appears in Device Manager but sound still plays through the speakers, the likely cause is that the headset is not set as the default playback device. Changing this setting in sound preferences directs audio to the headset. This is a common and straightforward fix.
❌ Incorrect Answers:
A. Update the drivers for the wireless headset:
Drivers can cause issues but if the device shows up properly, it’s less likely the cause here.
B. Replace the battery on the headset and try again later:
Battery issues would prevent connection entirely or cause dropouts, not cause default audio routing problems.
C. Verify that the sound is not muted in the control panel:
Muting would silence all audio, not cause it to route through speakers instead of the headset.
An administrator is investigating a zero-day vulnerability. If left unpatched, it could severely impact business. The patch requires downtime. What should the administrator do?
A. Create a standard change request.
B. Implement an emergency change.
C. Immediately freeze all changes.
D. Continue operations until the next change interval.
Explanation:
✅ Correct Answer (B. Implement an emergency change):
A zero-day vulnerability that requires urgent patching justifies an emergency change, which expedites the approval and deployment process to quickly reduce risk. Emergency changes are critical for urgent fixes that cannot wait for standard change windows, balancing speed with control.
❌ Incorrect Answers:
A. Create a standard change request:
Standard change processes are too slow for urgent, high-risk vulnerabilities.
C. Immediately freeze all changes:
Freezing changes delays remediation and leaves the system vulnerable.
D. Continue operations until the next change interval:
Waiting exposes the organization to unnecessary risk.
A user has been adding data to the same spreadsheet for several years. After adding a significant amount of data, they are now unable to open the file. Which of the following should a technician do to resolve the issue?
A. Revert the spreadsheet to the last restore point.
B. Increase the amount of RAM.
C. Defragment the storage drive.
D. Upgrade the network connection speed
Explanation:
✅ Correct Answer (B. Increase the amount of RAM):
Large spreadsheets require significant system memory to open and process. If the file is too large for the current RAM, the system may fail to open it. Increasing RAM provides the necessary resources to handle large files efficiently and resolves performance issues related to memory limitations.
❌ Incorrect Answers:
A. Revert the spreadsheet to the last restore point:
This might lose recent data and does not address the memory issue causing the file not to open.
C. Defragment the storage drive:
Defragmentation improves disk access but does not help with RAM shortages.
D. Upgrade the network connection speed:
Network speed affects file transfer but is irrelevant to opening a local file.
Which of the following is the quickest way to move from Windows 10 to Windows 11 without losing data?
A. Using gpupdate
B. Image deployment
C. Clean install
D. In-place upgrade
Explanation:
✅ Correct Answer (D. In-place upgrade):
An in-place upgrade installs the new OS version over the existing one, preserving user data, applications, and settings. This is the fastest way to move from Windows 10 to Windows 11 without data loss. It avoids the complexities of wiping the disk or restoring from backups.
❌ Incorrect Answers:
A. Using gpupdate:
Gpupdate refreshes Group Policy settings, unrelated to OS upgrades.
B. Image deployment:
This involves wiping and replacing the system image, which may cause data loss unless carefully managed.
C. Clean install:
A clean install erases the drive and installs a fresh OS, requiring data backup and restoration, which is slower and riskier for data loss.
You have been contacted through the help desk chat application. A user is setting up a
replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each
response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.
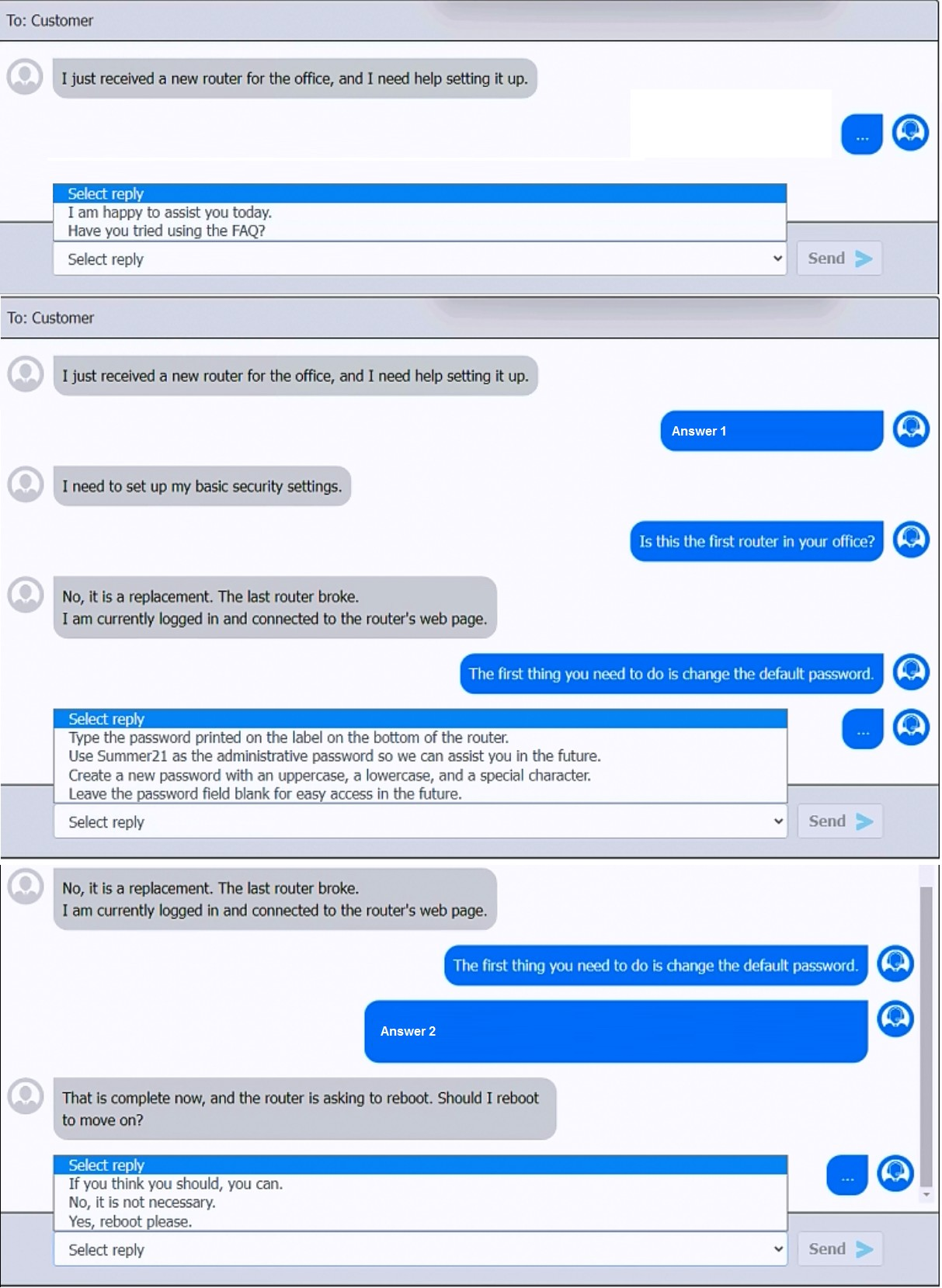
Explanation:
✅ Answer 1
The first thing you need to do is change the default password.
From the choices given in the screenshot, the correct follow-up to this is:
→ Create a new password with an uppercase, a lowercase, and a special character.
Why?
It’s best practice to replace the default administrative password on any network device for security.
CompTIA A+ Core 2 exam objectives (220-1102 and continuing into 220-1202) emphasize using strong passwords with complexity (upper/lowercase, numbers, symbols).
Reference:
CompTIA A+ 220-1102 Objective 2.3: “Given a scenario, apply security best practices to secure a workstation or SOHO network.”
Official CompTIA A+ Study Guide, Core 2 (Passwords: complexity, changing defaults, etc.)
✅ Answer 2
After changing the password, the user asks:
“The router is asking to reboot. Should I reboot?”
The correct answer is:
→ Yes, reboot please.
Why?
Many router configuration changes (especially admin password changes) require a reboot to take effect.
Advising the user to reboot finalizes the setup.
Reference:
CompTIA A+ 220-1102 Objective 2.6: “Given a scenario, configure SOHO multifunction devices / routers”
Vendor best practices for applying configuration changes
✅ Final Answers:
Answer 1: Create a new password with an uppercase, a lowercase, and a special character.
Answer 2: Yes, reboot please.
Users are reporting that an unsecured network is broadcasting with the same name as the normal wireless network. They are able to access the internet but cannot connect to the file share servers. Which of the following best describes this issue?
A. Unreachable DNS server
B. Virtual local area network misconfiguration
C. Incorrect IP address
D. Rogue wireless access point
Explanation:
1. A rogue wireless access point is an unauthorized device set up to broadcast a wireless network, often using the same SSID (network name) as a legitimate network.
2. Users may connect to this rogue network instead of the real one. While they might get internet access, other internal resources (like file shares) are typically unavailable because they’re no longer on the proper corporate network segment.
3. This is a classic security issue covered in CompTIA A+ Core 2 under wireless security threats.
Why the others are incorrect:
A. Unreachable DNS server → would prevent name resolution, but users would still be on the correct network and might be able to reach servers via IP.
B. VLAN misconfiguration → could isolate users from servers, but wouldn’t explain the duplicate SSID from a separate network.
C. Incorrect IP address → could cause connectivity issues but not the presence of a second, unsecured network with the same name.
As a corporate technician, you are asked to evaluate several suspect email messages on a
client's computer. Corporate policy requires the following:
>All phishing attempts must be reported.
>Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the following within the email:
>Classify the emails
>Identify suspicious items, if applicable, in each email
>Select the appropriate resolution
If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.
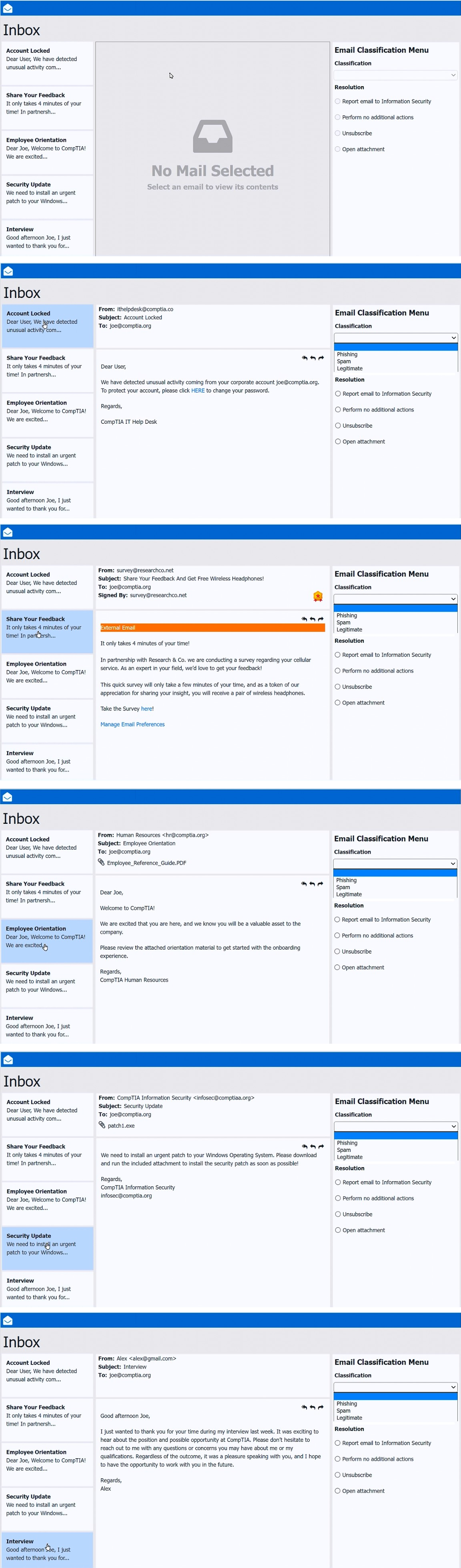
Explanation:
✅ Email #1 – “Account Locked”
From: ithelpdesk@comptia.co
To: joe@comptia.org
Subject: Account Locked
Suspicious Details:
Sender domain is “.co”, not the corporate domain “.org.”
Urgent language (“detected unusual activity”) is typical phishing
Classification: Phishing
Resolution: Report email to Information Security
✅ Email #2 – “Share Your Feedback”
From: survey@researchco.net
Subject: Share Your Feedback And Get Free Wireless Headphones!
Suspicious Details:
External sender (legitimate surveys typically use internal addresses)
Incentive of a free gift is a common spam technique
Classification: Spam
Resolution: Unsubscribe
✅ Email #3 – “Employee Orientation”
From: Human Resources hr@comptia.org
Subject: Employee Orientation
Suspicious Details: None
Internal sender
Expected onboarding communication
Classification: Legitimate
Resolution: Perform no additional actions
✅ Email #4 – “Security Update”
From: CompTIA Information Security infosec@comptia.org
Subject: Security Update
Suspicious Details:
Attachment: patch1.exe → Highly suspicious. Security patches are rarely distributed as direct .exe attachments via email.
Security updates should come via official channels or internal patch management tools.
Classification: Phishing
Resolution: Report email to Information Security
✅ Email #5 – “Interview”
From: Alex alex@gmail.com
Subject: Interview
Suspicious Details: None
Context matches a recent interview
No suspicious links or attachments
Classification: Legitimate
Resolution: Perform no additional actions
MFA for a custom web application on a user's smartphone is no longer working. The last time the user remembered it working was before taking a vacation to another country. Which of the following should the technician do first?
A. Verify the date and time settings
B. Apply mobile OS patches
C. Uninstall and reinstall the application
D. Escalate to the website developer
Explanation:
→ Multifactor authentication (MFA) applications, such as Google Authenticator or Authy, frequently generate time-based one-time passwords (TOTP). These numeric codes rely on the smartphone’s internal clock aligning precisely with the time maintained by the authentication server.
→ When someone travels internationally, the device may automatically adjust its time zone or retain an incorrect offset due to network settings or manual changes. This discrepancy disrupts the code generation process, rendering the one-time passwords invalid during login attempts.
→ Investigating and correcting the device’s date, time, and time zone ensures synchronization between the smartphone and the server, restoring proper MFA functionality. Therefore, before reinstalling applications or escalating the issue, technicians should prioritize confirming that the system clock reflects the correct local settings.
Which of the following is the best way to distribute custom images to 800 devices that include four device vendor classes with two types of user groups?
A. Use xcopy to clone the hard drives from one to another
B. Use robocopy to move the files to each device
C. Use a local image deployment tool for each device
D. Use a network-based remote installation tool
Explanation:
Deploying images to 800 devices is a large-scale task that requires speed, consistency, and minimal manual effort.
A network-based remote installation tool (like Windows Deployment Services, SCCM, MDT, or other enterprise deployment solutions) allows IT teams to:
1. Deploy images to multiple machines simultaneously over the network
2. Handle different hardware classes (e.g. drivers for four vendor types) using hardware-specific driver injection
3. Apply custom images based on user groups (e.g. different software for two user types) through task sequences or deployment rules
4. Maintain consistent configurations, reducing human error
This method is highly scalable and far more efficient than copying files manually or imaging each machine one by one.
Why the others are incorrect:
A. Use xcopy to clone the hard drives from one to another
Xcopy is a file copy utility, not suitable for imaging entire disks or deploying OS installations.
B. Use robocopy to move the files to each device
Robocopy can copy files robustly but cannot deploy OS images or handle partitions, boot records, or drivers.
C. Use a local image deployment tool for each device
A local tool requires connecting physical media (USB drives, DVDs) to each machine individually, which is time-consuming and impractical for 800 devices.
Reference:
1. CompTIA A+ Core 2 (220-1102) Objective 1.8: “Given a scenario, deploy and configure imaging tools.”
2. Microsoft Docs – Windows Deployment Services
3. CompTIA A+ Official Study Guide – Deployment strategies
| Page 3 out of 21 Pages |
