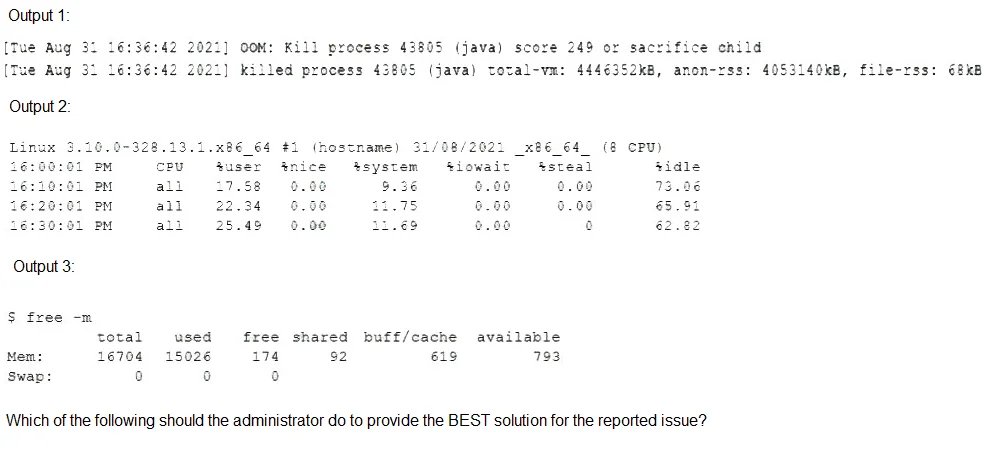
A Linux systems administrator receives reports from various users that an application hosted on a server has stopped responding at similar times for several days in a row. The administrator logs in to the system and obtains the following output:
A.
Configure memory allocation policies during business hours and prevent the Java process from going into a zombie state while the server is idle.
B.
Configure a different nice value for the Java process to allow for more users and prevent the Java process from restarting during business hours.
C.
Configure more CPU cores to allow for the server to allocate more processing and prevent the Java process from consuming all of the available resources.
D.
Configure the swap space to allow for spikes in usage during peak hours and prevent the Java process from stopping due to a lack of memory.
Configure the swap space to allow for spikes in usage during peak hours and prevent the Java process from stopping due to a lack of memory.
Summary:
The outputs indicate a critical memory issue. Output 2 shows that the system's available memory is nearly exhausted, with only 122MB free and 32GB of swap space being heavily used. Output 3 confirms that a single Java process (java -jar application.jar) is consuming over 95% of the system's memory. This pattern suggests that daily peak usage causes the Java application to exhaust physical RAM, forcing the system to rely heavily on slow swap space, which halts the application.
Correct Option:
D. Configure the swap space to allow for spikes in usage during peak hours and prevent the Java process from stopping due to a lack of memory.:
This is the most direct and effective solution. The Java process is hitting the physical memory limit. While adding more RAM is the ideal long-term fix, the question asks for the administrator's action. Increasing swap space provides a larger safety net for these daily memory spikes, allowing the Java process to continue running (albeit more slowly when swapping) instead of being killed by the Out-of-Memory (OOM) Killer. This directly addresses the "stopped responding" symptom reported by users.
Incorrect Options:
A. Configure memory allocation policies...prevent the Java process from going into a zombie state...:
The process is not in a zombie state (a terminated process waiting for its parent to read its exit status). It is a runaway process consuming all available memory. The issue is resource exhaustion, not a zombie process.
B. Configure a different nice value for the Java process...:
The "nice" value controls CPU scheduling priority. The primary bottleneck here is memory, not CPU. Changing the nice value would have no effect on the memory exhaustion problem and would not prevent the process from restarting.
C. Configure more CPU cores to allow for the server to allocate more processing...:
While Output 1 shows high CPU usage, this is likely a symptom of the memory problem. When a system spends excessive time swapping (reading/writing memory to disk), it appears as high CPU usage due to the kernel's management of I/O wait. Adding CPU cores does not solve the underlying lack of RAM and would not prevent the Java process from consuming all available memory.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.3: "Given a scenario, analyze and troubleshoot application and hardware issues," which includes troubleshooting performance issues such as memory and CPU utilization. The ability to interpret top and free output to identify a memory-bound process is a key skill.
After installing a new version of a package, a systems administrator notices a new version of the corresponding, service file was Installed In order to use the new version of the, service file, which of the following commands must be Issued FIRST?
A.
systemctl status
B.
systemctl stop
C.
systemctl reinstall
D.
systemctl daemon-reload
systemctl daemon-reload
Summary:
A new version of a systemd service file has been installed on the system. The systemd manager keeps an in-memory copy of unit files. When the on-disk version of a unit file is modified, the systemd manager must be explicitly told to reload its configuration to recognize the changes. Without this step, any subsequent commands (like restarting the service) will use the old, in-memory configuration.
Correct Option:
D. systemctl daemon-reload:
This is the necessary first command. It instructs the systemd manager to reload its configuration from disk, thereby picking up the new version of the service file. After this command is run, the new service file is active in systemd's memory, and the service can then be restarted to use the new configuration.
Incorrect Options:
A. systemctl status:
This command only displays the current status of the service (whether it is running, enabled, etc.). It is a read-only command and does not load new configuration files.
B. systemctl stop:
This command stops the service if it is running. However, if issued before a daemon-reload, it would stop the service using the old configuration. More importantly, simply stopping the service does not make systemd aware of the new service file.
C. systemctl reinstall:
This is not a valid systemctl command. There is no reinstall subcommand.
Reference:
systemd Official Documentation (systemctl): The official man page explains the daemon-reload command, which reloads the manager configuration.
A systems administrator has been unable to terminate a process. Which of the following should the administrator use to forcibly stop the process?
A.
kill -1
B.
kill -3
C.
kill -15
D.
kill -HUP
E.
kill -TERM
kill -TERM
Summary:
A systems administrator needs to forcibly stop a process that has not responded to a standard termination request. While a standard kill command sends a TERM signal (15), which allows the process to shut down gracefully, a more forceful signal is required when a process is hung or unresponsive. The correct signal must be one that the process cannot ignore.
Correct Option:
E. kill -TERM:
This is the correct answer for forcibly stopping a process. The -TERM signal (which is signal 15) is the standard, default termination signal that requests a process to shut down. It is more forceful than a HUP and is the standard first step before resorting to the unconditional -KILL signal. If a process is ignoring this, the next step would be kill -KILL or kill -9.
Incorrect Options:
A. kill -1:
This sends the HUP (hangup) signal. Its primary purpose is to tell a process to reload its configuration files, not to terminate. While some daemons may exit on a HUP, this is not standard behavior and is not a reliable way to forcibly stop a process.
B. kill -3:
This sends the QUIT signal. It often causes a process to terminate and produce a core dump for debugging. It is not more forceful than TERM and is primarily used by developers, not for general administrative process termination.
C. kill -15:
This is the numeric equivalent of kill -TERM. It is the standard termination signal but is not the most forceful option available. The question implies the administrator has already been unable to terminate the process, suggesting a more forceful signal like KILL is needed.
D. kill -HUP:
This is the same as kill -1. It is a "hangup" signal used for reinitialization, not for forced termination. It is not the correct tool to stop an unresponsive process.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.1: "Given a scenario, use the appropriate system and service management commands to accomplish administrative tasks," which includes managing and troubleshooting processes and services. Knowing the different kill signals and their effects is a fundamental skill for a Linux administrator.
Joe, a user, is unable to log in to the Linux system. Given the following output:

Which of the following commands would resolve the issue?
A.
usermod -s /bin/bash joe
B.
pam_tally2 -u joe -r
C.
passwd -u joe
D.
chage -E 90 joe
usermod -s /bin/bash joe
Summary:
The provided output shows the result of the chage -l joe command, which displays password and account aging information. The key field is "Account expires," which shows a specific past date. When an account expiration date is in the past, the account is locked, and the user is prevented from logging in, regardless of whether their password is correct. This is a common security measure for temporary accounts or contract workers.
Correct Option:
D. chage -E 90 joe:
This command would resolve the issue by setting a new, future expiration date. The -E option with the chage command sets the account expiration date. The value 90 is interpreted as the number of days since January 1, 1970 (the epoch), which would be a date in 1970. To properly fix this, a more realistic future date or -1 to never expire would be used, but the command syntax itself is for managing account expiration, which is the root cause.
Incorrect Options:
A. usermod -s /bin/bash joe:
This command changes the user's login shell. The chage output does not show any issue with the login shell. The problem is the account expiration, not the shell.
B. pam_tally2 -u joe -r:
This command is used to reset the failed login counter for a user. It would unlock an account that was locked due to too many failed password attempts. There is no evidence of a failed login counter in the chage output; the issue is an expired account, not a locked one.
C. passwd -u joe:
This command is used to unlock a user's password, which is only relevant if the password itself was locked using passwd -l. The chage output shows the account is expired, which is a different type of lock that is not resolved by unlocking the password.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.3: "Given a scenario, manage users and groups," which includes user account creation and modification. The chage command is a core utility for managing password and account expiration policies.
After installing some RPM packages, a systems administrator discovers the last package that was installed was not needed. Which of the following commands can be used to remove the package?
A.
dnf remove packagename
B.
apt-get remove packagename
C.
rpm -i packagename
D.
apt remove packagename
dnf remove packagename
Summary:
The question asks for the command to remove an unwanted package from a Linux system. The correct command depends on the system's package manager. The output from the initial history command shows dnf install being used, which is the package manager for modern Red Hat-based distributions like RHEL, CentOS, and Fedora. Therefore, the removal command must use the same package manager.
Correct Option:
A. dnf remove packagename:
This is the correct command for a system using the dnf package manager. The dnf remove command cleanly uninstalls the specified package and its dependencies that are no longer needed, ensuring the package is fully removed from the system.
Incorrect Options:
B. apt-get remove packagename and D. apt remove packagename:
These commands are used by Debian-based distributions like Ubuntu. Since the system's history shows the use of dnf install, using apt or apt-get would be incorrect and would not work, as these package managers are not present on this system.
C. rpm -i packagename:
The rpm -i command is used to install a package from a local .rpm file, not to remove one. The flag for removing a package with rpm is -e (erase), but using the higher-level dnf tool is preferred because it automatically handles dependencies.
Reference:
DNF Command Reference: The official documentation for the dnf package manager, which includes the remove command.
Users have reported that the interactive sessions were lost on a Linux server. A Linux administrator verifies the server was switched to rescue.target mode for maintenance. Which of the following commands will restore the server to its usual target?
A.
telinit 0
B.
systemctl reboot
C.
systemctl get-default
D.
systemctl emergency
systemctl reboot
Summary:
The server is currently in rescue.target mode, a minimal, single-user state used for system maintenance. In this mode, most services, including those allowing user logins and multi-user sessions, are not running. To restore full functionality and interactive user sessions, the administrator needs to reboot the server, which will load the default target (typically multi-user.target or graphical.target) and start all the necessary services.
Correct Option:
B. systemctl reboot:
This is the correct command to resolve the issue. The systemctl reboot command cleanly shuts down the system and initiates a reboot. Upon restart, the system will automatically boot into the default system target, which will start all the required services for multi-user operation and restore interactive sessions for users.
Incorrect Options:
A. telinit 0:
This command is used to shut down or power off the system (runlevel 0). It will not restore the server to its usual target; it will completely turn the server off, requiring manual power-on to restore service.
C. systemctl get-default:
This is a diagnostic command that only displays the current default target (e.g., multi-user.target). It is a read-only command that retrieves information but performs no action to change the system's current state or target.
D. systemctl emergency:
This command would switch the system to emergency.target, which is an even more minimal state than rescue.target. It provides the most basic environment for recovery when the rescue target is unsuccessful and would make the problem worse, not better.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.1: "Given a scenario, use the appropriate system and service management commands to accomplish administrative tasks," which includes managing systemd targets. Knowing how to properly exit maintenance modes like rescue or emergency is a key administrative skill.
A Linux system is failing to boot. The following error is displayed in the serial console:
[[1;33mDEPEND[Om] Dependency failed for /data.
[[1;33mDEPEND[Om] Dependency failed for Local File Systems
...
Welcome to emergency mode! After logging in, type "journalctl -xb" to viewsystem logs,
"systemctl reboot" to reboot, "systemctl default" to try again to boot into default mode.
Give root password for maintenance (or type Control-D to continue}
Which of the following files will need to be modified for this server to be able to boot again?
A.
/etc/mtab
B.
/dev/sda
C.
/etc/fstab
D.
/ete/grub.conf
/etc/fstab
Summary:
The system has failed to boot and has entered emergency mode. The specific error messages indicate a "Dependency failed for /data" and "Dependency failed for Local File Systems." This state is almost always caused by a problem defined in the /etc/fstab file, which contains the instructions for what filesystems to mount at boot. If a device listed in this file is unavailable, incorrectly configured, or has errors, the boot process will halt.
Correct Option:
C. /etc/fstab:
This is the file that needs to be modified. The /etc/fstab (file systems table) is read by the system during the boot process to automatically mount filesystems. The error explicitly states that the mount for /data failed. The administrator must log in via emergency mode, check the /etc/fstab file for the entry corresponding to /data, and correct the device path, filesystem type, or other options. Alternatively, they could temporarily comment out the line to allow the system to boot.
Incorrect Options:
A. /etc/mtab:
This file dynamically lists the filesystems that are currently mounted. It is maintained by the mount command and is a reflection of the system's state, not a configuration file. Modifying it would not fix the underlying configuration error causing the boot failure.
B. /dev/sda:
This is a device file representing the first disk drive. It is not a configuration file that can be edited to solve a boot dependency issue. Modifying a raw block device would corrupt data, not fix a boot problem.
D. /ete/grub.conf:
This path is incorrect and contains a typo (/ete instead of /etc). The correct GRUB configuration file is typically /boot/grub2/grub.cfg or /etc/grub2.cfg. While GRUB issues can prevent booting, the specific error message about filesystem dependencies points directly to fstab, not the bootloader.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 1.3: "Given a scenario, conduct a Linux boot process and troubleshooting," which includes troubleshooting boot issues and managing the fstab file. Understanding that emergency mode is often entered due to fstab errors is a critical troubleshooting skill.
A cloud engineer needs to change the secure remote login port from 22 to 49000. Which of the following files should the engineer modify to change the port number to the desired value?
B.
/etc/hostname
C.
/etc/services
D.
/etc/ssh/sshd_config
/etc/ssh/sshd_config
Summary:
The engineer needs to change the port on which the SSH daemon (sshd) listens for incoming connections. This is a service-specific configuration change, not a system-wide network or hostname setting. The configuration must be modified in the file that controls the behavior of the SSH server itself.
Correct Option:
D. /etc/ssh/sshd_config:
This is the primary configuration file for the SSH daemon. It contains directives that control the operation of the server, including the port number. The engineer would edit this file and change the Port directive (or add it if it doesn't exist) to 49000, then restart the sshd service for the change to take effect.
Incorrect Options:
A. /etc/host.conf:
This file determines the order in which hostnames are resolved (e.g., via hosts file or DNS). It has no control over service ports.
B. /etc/hostname:
This file contains the system's hostname. Changing this file would affect how the system identifies itself on the network, not the port SSH listens on.
C. /etc/services:
This file is a static database that maps well-known service names to their assigned port numbers and protocols (e.g., ssh 22/tcp). It is used for informational purposes by network utilities but does not control which ports services actually bind to. Changing a port here would not reconfigure the SSH daemon.
Reference:
OpenSSH Manual (sshd_config): The official documentation for the SSH daemon configuration file, which describes the Port directive.
A systems administrator is compiling a report containing information about processes that are listening on the network ports of a Linux server. Which of the following commands will allow the administrator to obtain the needed information?
A.
ss -pint
B.
tcpdump -nL
C.
netstat -pn
D.
lsof -It
ss -pint
Summary:
The administrator needs to generate a report of processes that are actively listening for network connections. The command must show which network ports are open and which process has each port open. The tool should provide a clear, list-based output suitable for a report, showing port numbers, the listening process, and its PID.
Correct Option:
A. ss -pint:
This is the most efficient and modern command for this task. The ss (socket statistics) command is designed to dump socket statistics and replaces the older netstat.
-p shows the process name and PID using the socket.
-i shows internal TCP information.
-n prevents service name resolution, showing port numbers instead (faster and better for reports).
-t shows only TCP sockets.
-l shows only listening sockets.
Incorrect Options:
B. tcpdump -nL:
tcpdump is a network packet analyzer, not a socket lister. The -L flag lists the data link types for an interface, it does not list processes listening on network ports. This command is for capturing or analyzing network traffic, not for reporting on listening services.
C. netstat -pn:
While netstat can provide this information and was the traditional tool, it is now considered obsolete and is replaced by ss. The -p shows the PID/program, and -n shows numerical addresses. However, it is missing the -l flag to show only listening ports, so it would show all network connections, making the output less focused for a report on listening services.
D. lsof -It:
The lsof command lists open files, and network connections are considered files in Linux. However, the flags are incorrect. -I is for selecting by IP version, and -t produces a terse (PID-only) output, which is not suitable for a detailed report. The correct lsof syntax would be more complex, such as lsof -iTCP -sTCP:LISTEN -P -n.
Reference:
Linux man-pages project (ss): The official documentation for the ss command, which is the recommended tool for showing socket statistics.
A user is asking the systems administrator for assistance with writing a script to verify whether a file exists. Given the following:
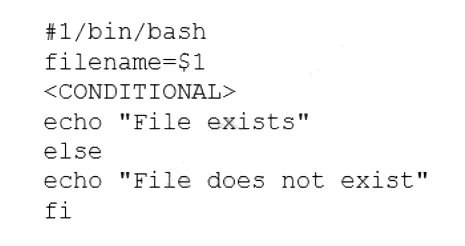
Which of the following commands should replace the
A.
if [ -f "$filename" ]; then
B.
if [ -d "$filename" ]; then
C.
if [ -f "$filename" ] then
D.
if [ -f "$filename" ]; while
if [ -f "$filename" ]; then
Summary:
The script snippet is a Bash script designed to check if a file exists. The script takes a filename as an argument ($1). The
Correct Option:
A. if [ -f "$filename" ]; then: This is the correct and complete syntax.
if starts the conditional statement.
[ -f "$filename" ] is the test command. The -f flag checks if the path exists and is a regular file. The variable $filename is quoted to handle filenames with spaces.
; terminates the test command, allowing then to be on the same line.
then begins the block of code to execute if the condition is true.
Incorrect Options:
B. if [ -d "$filename" ]; then:
This uses the -d flag, which checks if the path exists and is a directory. The requirement is to check for a file, so this operator is incorrect for the stated goal.
C. if [ -f "$filename" ] then:
This is missing the semicolon (;) or a newline before the then keyword. In Bash, the then must be a separate command, which requires either being on a new line or being separated from the test bracket with a semicolon. This syntax would cause a syntax error.
D. if [ -f "$filename" ]; while:
This incorrectly uses the while loop keyword after the conditional test. The if statement must be followed by then to start the conditional block, not by another loop keyword.
Reference:
Bash Reference Manual (Conditional Constructs): The official documentation explains the syntax for the if statement.
| Page 10 out of 48 Pages |
| XK0-005 Practice Test | Previous |
