A PM is working to establish accepted communication channels and to define access requirements. In which of the following phases is the project?
A. Discovery
B. Execution
C. Initiating
D. Planning
A procurement team analyzes solutions submitted from multiple vendors for the upcoming release of a required development service. The procurement team identifies a potential partnership. Which of the following would the procurement team most likely request?
A. Quote
B. Information
C. Proposal
D. Bid
Explanation: A proposal is a detailed document submitted by vendors outlining how they will meet project requirements. It helps in assessing vendor solutions and suitability, consistent with CompTIA Project+ procurement and vendor management practices.
Which of the following should be considered first when determining the privacy management for project data?
A. Evaluating the current privacy protection program
B. Understanding applicable privacy regulations
C. Maintaining awareness of industry best practices
D. Implementing security role-based controls
Explanation: Before starting a new project that involves personal data, the project manager should first understand the relevant privacy regulations that apply to the data subjects, the data controllers, and the data processors. These regulations may vary depending on the location, industry, and nature of the data. For example, GDPR applies to any project that processes the personal data of individuals in the European Union, regardless of where the project is based or executed. Understanding the applicable privacy regulations will help the project manager to identify the legal obligations, risks, and compliance requirements for the project data. References = CompTIA Project+ Study Guide, Chapter 3: Project Planning, Section 3.4: Data Privacy and Security, p. 121-122; A Project Management Approach to Data Protection Compliance; 10 Data Protection Considerations Before Starting a New Project; Project Teams Must Manage Risk and New Requirements to Ensure Data Privacy
A project manager distributes minutes after each project meeting. However, the project manager is having difficulties hosting the meetings and documenting the discussions simultaneously. Which of the following should the project manager do in order to be most efficient?
A. Assign a scribe to take notes.
B. Record the meeting and transcribe the notes later.
C. Instruct each team member to take notes.
D. Get a facilitator for the meetings.
Explanation: Assigning a scribe allows the project manager to focus on hosting and facilitating the meeting effectively without being distracted by note-taking. This approach is consistent with best practices in meeting management and aligns with CompTIA Project+ guidelines, which emphasize the importance of efficient meeting roles and responsibilities.
During the stabilization phase for recently deployed software, an end user reports a bug that is compromising data integrity. Which of the following tools will the project manager MOST likely use?
A. Issue log
B. Defect log
C. Change log
D. Task board
Explanation: During the stabilization phase of recently deployed software, the project manager will most likely use a defect log to track and manage reported bugs. A defect log is a document that contains information about the defects or issues identified during testing or after the deployment of software. It includes the severity of the defect, the steps to reproduce the problem, and the actions taken to resolve the defect. The project manager will most likely use a defect log during the stabilization phase for recently deployed software to record a bug that is compromising data integrity. A defect log is a tool that tracks and documents any errors or flaws found in a software product or system during testing or operation. It usually includes information such as defect ID, description, severity, priority, status, resolution, and responsible person. A defect log can help to monitor and manage the quality of the software product or system and ensure that all defects are identified and resolved before delivery or release.
Several stakeholders have declined the invitation for the kickoff of a major digital transformation protect. Which of the following actions should the project manager take NEXT?
A. Escalate directly to the project sponsor
B. Push the kickoff meeting out by one week
C. Proceed with the kickoff as planned
D. Identity replacements for project stakeholders
Explanation: The project sponsor is the person who provides the authority, funding, and support for the project. The project sponsor can also help to influence and engage the key stakeholders who are essential for the success of the project. If several stakeholders have declined the invitation for the kickoff meeting, which is an important event to establish the vision, scope, and expectations of the project, the project manager should escalate this issue to the project sponsor and seek their assistance to ensure the participation of the stakeholders.
Given the following velocity chart:
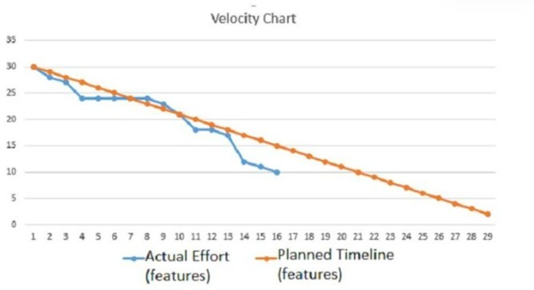
Which of the following updates on the project status should the Scrum master provide to the senior management team?
A. The project utilized all of its available reserve.
B. The project has scope creep.
C. The project deviated from the critical path.
D. The project is trending ahead of schedule.
Hackers are attempting to extract large amounts of data to sell on the dark web. Which of the following steps should a project manager take next to mitigate this risk?
A. Update the issue log.
B. Apply the contingency plan.
C. Transfer the risk.
D. Submit a change request.
A critical business initiative introduced new processes and technology to the organization. Which of the following approaches should be used to ensure the deliverables are increasingly adopted and leveraged by the organization over time?
A. Creation of a social news forum
B. Management directives to use the new system
C. New user kickoff meeting
D. Monthly feedback and training sessions
Explanation: Monthly feedback and training sessions are the best approach to ensure that the deliverables of a critical business initiative are increasingly adopted and leveraged by the organization over time. Feedback and training sessions are communication and learning activities that provide information and guidance on how to use and benefit from the new processes and technology introduced by the initiative. Feedback and training sessions can help to increase awareness, understanding, acceptance, and adoption of the deliverables among the organization’s employees and stakeholders. They can also help to identify and address any issues or challenges that may arise during the implementation and transition phases.
During a complex, multiyear project, a PM must discern which project tasks overlap so resources can be allocated appropriately. Which of the following is best for determining this information?
A. PERT chart
B. Milestone chart
C. Gantt chart
D. Budget burndown chart
| Page 10 out of 37 Pages |
