Topic 2: Exam Pool B
A user reports limited or no connectivity on a laptop. A technician runs ipconf ig /all with the
following result: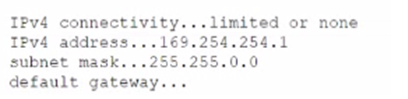
Which of the following is the MOST likely cause of this issue?
A. DHCP failure
B. ARP cache
C. DNS resolution
D. Duplicate IP address
The IT department at an insurance brokerage needs to acquire laptops that have built-in fingerprint readers in order to create a more secure environment. Which of the following would be the MOST secure way to implement the fingerprint readers?
A. Grant all registered employees access to each machine.
B. Restrict device access to only the user to whom the laptop is assigned
C. Limit device access to departments and guest users
D. Give each team member a USB drive that bypasses the reader to allow guest users lo log in.
Explanation: The most secure way to implement fingerprint readers would be to restrict device access to only the user to whom the laptop is assigned. This ensures that only authorized personnel have access to the device, reducing the risk of unauthorized access and data breaches.
A customer reports a problem connecting to network resources. After asking open-ended questions, the technician determines the issue likely exists on the remote server. Which of the following should the technician do next?
A. Document the findings.
B. Test the theory
C. Gather information
D. Establish a plan of action
Explanation: After determining the issue is likely on the remote server, the technician should test the theory to confirm the root cause before proceeding.
✑ Why Not A (Document the findings): Documentation comes after confirming the
issue.
✑ Why Not C (Gather information): Information gathering is already completed.
✑ Why Not D (Establish a plan of action): This is done after confirming the issue.
CompTIA A+ Exam Reference: Core 2 (220-1102), Section 3.1, troubleshooting methodology.
A technician was called in to look at a user's PC. The user reported the PC was very sluggish. The HDD light on the PC was constantly on without blinking. The PC itself was slow receiving input and took a very long time to load the OS. The technician also noticed updates had failed. Which of the following is MOST likely the cause of these issues?
A. The hard disk drivers have been corrupted
B. The HDD cables need reseating
C. A RAID disk failed
D. The HDD has no free space.
Explanation: If a user’s PC is very sluggish, the HDD light on the PC is constantly on without blinking, the PC itself is slow receiving input, and it takes a very long time to load the OS, the HDD has no free space is most likely the cause of these issues. When the hard disk drive (HDD) has no free space, the computer may become slow and unresponsive. The technician should check the amount of free space on the HDD and delete any unnecessary files to free up space.
After a technician updated the wireless APs to 5GHz, users report they have degraded Wi- Fi performance. The technician tests for interference but finds none. Which of the following should the technician do next?
A. Select a different channel.
B. Switch the Wi-Fi back to the 2.4GHz frequency.
C. Upgrade the wireless drivers on the users' devices.
D. Add more access points for better coverage.
A technician is troubleshooting a thermal receipt printer that will not print. Which of the following should the technician do first to restore functionality?
A. Update the printer driver on the computer.
B. Replace the thermal printhead.
C. Make sure the thermal head is heating up.
D. Flip the paper roll orientation.
Explanation: In the case of a thermal receipt printer that will not print, the first step in troubleshooting should be to ensure that the thermal head is heating up. Thermal printers operate by applying heat to a special thermally sensitive paper, creating marks on the paper to form text and images. If the thermal head is not heating up, it cannot create these marks, leading to no print output. Verifying that the thermal head is operational can help isolate the issue, whether it's a hardware malfunction of the thermal head itself or another problem in the printer.
Which of the following wireless technologies has the MOST range and wireless throughput?
A. 802.11ac
B. 802.11ax
C. 802. 11b/gin
D. 802.11g
Explanation: 802.11ax, also known as Wi-Fi 6, has the longest range and the highest wireless throughput of all the wireless technologies listed. References: CompTIA A+ Certification Exam Guide, 220-1001, Chapter 3
A company has implemented a policy that allows employees to use personal devices to perform work duties. Which of the following policies should the technician activate to protect company information?
A. MFD
B. MAM
C. MFA
D. MDM
Explanation: Mobile Device Management (MDM) policies are crucial for companies that allow employees to use personal devices for work duties. MDM enables the company to enforce security policies, manage and secure corporate data on personal devices, and ensure compliance with company standards. It allows for remote management of these devices, including the ability to remotely wipe company data if the device is lost or stolen, without impacting personal data, thereby protecting company information effectively.
Following a security breach that revealed employee username and password information, an organization would like to implement additional security for users logging in to company devices. Which of the following would be the best solution for the organization to use?
A. Biometric authentication
B. Peer-reviewed log-ins
C. Log-in scripts
D. One-time tokens
Explanation: In response to a security breach involving compromised credentials, one- time tokens provide an effective method to enhance authentication security. These tokens are part of multi-factor authentication (MFA) and generate unique codes for each login attempt, ensuring that even if credentials are stolen, unauthorized access is prevented.
✑ Why One-time Tokens?
✑ Incorrect Options:
CompTIA A+ Exam Objectives References:
✑ 220-1102 (Core 2), Section 2.1 and 2.2: Discuss security measures, including multi-factor authentication and one-time token implementations.
Employees are concerned about sensitive data being printed on a shared multifunction printer located in a high-traffic hallway. Which of the following should a technician do to address this concern?
A. Set up a PIN for user authentication at the printer.
B. Relocate the printer to an unused office space.
C. Configure printing of sensitive data through a specific tray.
D. Schedule print jobs to be released at certain times.
| Page 29 out of 85 Pages |
| 220-1101 Practice Test | Previous |
